Malicious domain name detection method and detection system based on multi-dimensional features and fuzzy rough set
A fuzzy rough set and domain name detection technology, which is applied in transmission systems, digital transmission systems, character and pattern recognition, etc., can solve problems such as low classification accuracy, low generalization of detection models, and inability to effectively detect malicious domain names, etc., to achieve The effect of improving detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
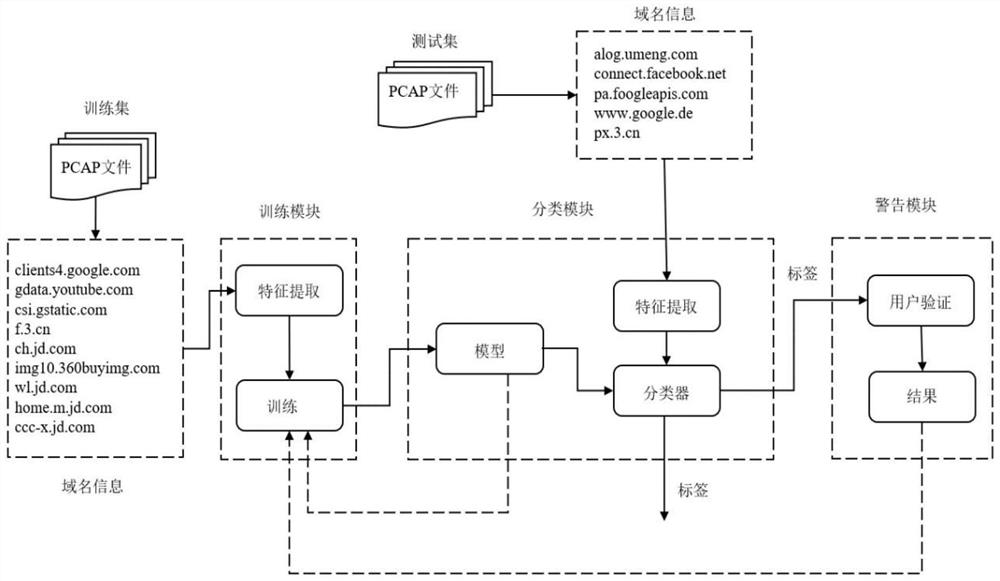
[0054] see figure 1 , this embodiment 1 provides a malicious domain name detection system based on multi-dimensional features and fuzzy rough sets, the system specifically includes:
[0055] Module 1, training module, is divided into feature extraction and model training;
[0056] Specifically, in this embodiment, the above feature extraction specifically includes: extracting multi-dimensional features from domain name information collected from network traffic;
[0057] Specifically, in this embodiment, the above-mentioned model training specifically includes: adopting the interval training method and using the online incremental fuzzy rough support vector machine algorithm;
[0058] Module 2, classification module, classifies the domain name, and the output is a label, which can classify the input domain name as a malicious domain name or a benign domain name;
[0059] Module 3, the warning module, warns the user according to the label output by the classification module; ...
Embodiment 2
[0080] The second embodiment provides a malicious domain name detection method based on multi-dimensional features and fuzzy rough sets, and the detection method includes the following steps:
[0081] Step S1, perform feature extraction and model training, which includes:
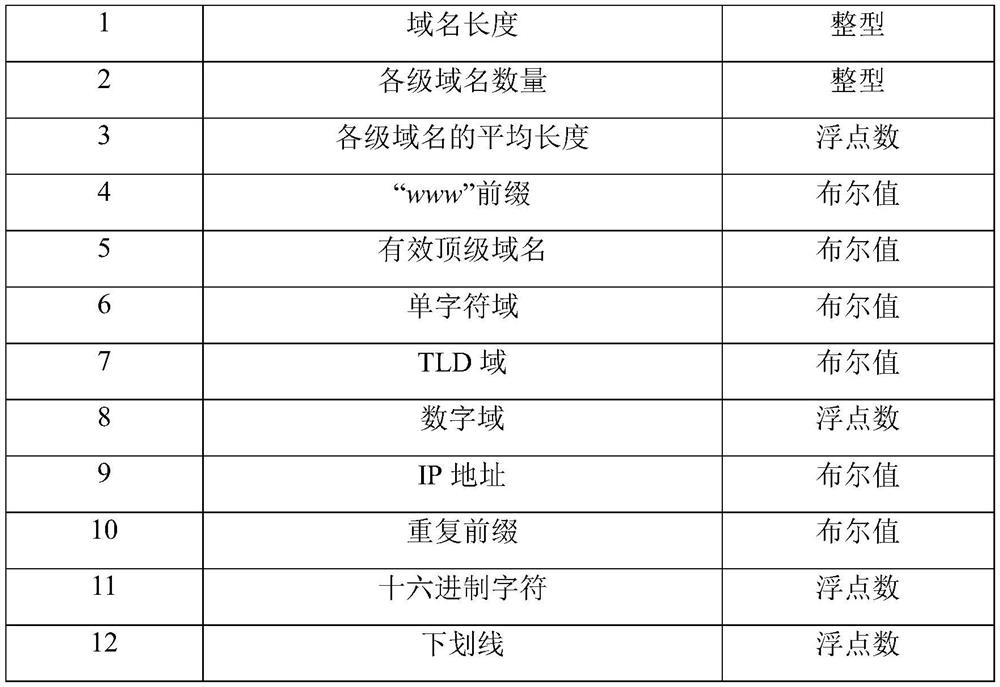
[0082] First, obtain domain name information from network traffic, and then extract multi-dimensional features based on the domain name information. Multi-dimensional features include: structural features, language features, and statistical features;
[0083] Then, for the extracted multi-dimensional features, the interval training method is adopted, and the online incremental fuzzy rough support vector machine algorithm is used for model training;
[0084] Finally, the classification model is obtained;
[0085] Step S2, classifying, which includes:
[0086] For a domain name to be detected, input it into the classification model obtained in step S1 for classification, and the output of the classification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com