Honeypot safety state determination method, electronic equipment and computer readable storage medium
A technology for determining the method and security status, applied in the field of network security, can solve the problem of lack of accuracy in the method of judging the security status of honeypots, and achieve the effect of improving reliability and accuracy and avoiding inaccurate judgment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
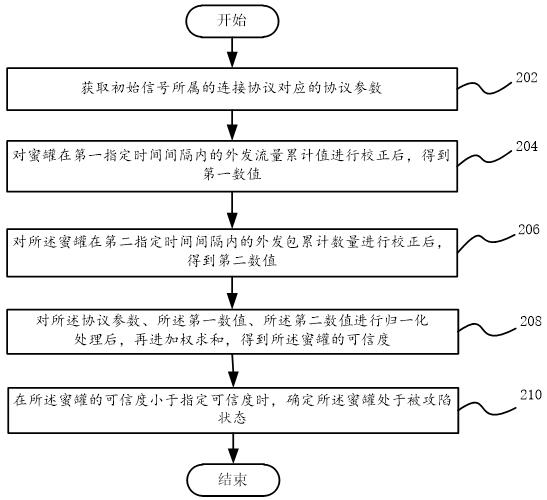
[0028] figure 1 A flow chart of a method for determining a honeypot security state according to an embodiment of the present invention is shown.
[0029] Such as figure 1 As shown, the method for determining the security state of a honeypot according to an embodiment of the present invention includes:
[0030] Step 102, in response to the honeypot actively sending an initial signal to the outside, determine whether the connection protocol to which the initial signal belongs is the TCP protocol, wherein, if the initial signal is the first SYN message in the three-way handshake process before the TCP connection is established, It is determined that the connection protocol to which the initial signal belongs is the TCP protocol, and proceed to step 104, and if the connection protocol to which the initial signal belongs is a non-TCP protocol, proceed to step 106.
[0031] Step 104, based on the detection method corresponding to the TCP protocol, determine whether the honeypot is...
Embodiment 2
[0042] For the TCP protocol, based on the detection method corresponding to the TCP protocol, determine whether the honeypot is in a compromised state, including: if the long connection heartbeat packet corresponding to the TCP protocol is detected, and / or, if the TCP protocol If the connection duration of the corresponding persistent connection is greater than the specified duration threshold, it is determined that the honeypot is in a compromised state.
[0043] When the honeypot establishes a long-term connection with the external object through the TCP protocol, the honeypot and the external object will send a heartbeat packet to indicate that the long-term connection persists. Therefore, once the long-term connection heartbeat packet is detected, it means that the honeypot and the external object have established a long-term connection The connection is used for communication, and there is a risk of data leakage to external objects, so it can be determined that the honeypo...
Embodiment 3
[0045] If it is detected that the honeypot uses an abnormal port outside the local open port whitelist for communication, it is determined that the honeypot is in a compromised state.
[0046] Specifically, for any type of non-TCP protocol, a whitelist of open ports can be set locally, and the ports in the whitelist of ports are determined to be legal communication ports. If the honeypot communicates through the non-TCP protocol, it uses an abnormal port other than the port whitelist, indicating that this communication behavior is not a safe and legal communication behavior. Therefore, the active contract sending of the honeypot is a risky behavior, and it can be determined that the honeypot is under attack.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com