Military communication encrypted traffic identification method based on generative adversarial network and model compression
A traffic identification and military communication technology, applied in the field of military communication encrypted traffic identification, can solve the problems of difficult to obtain encrypted traffic data sets, deploy deep neural network models, and large deep learning models, achieve strong robustness, and solve problems that are difficult to obtain. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
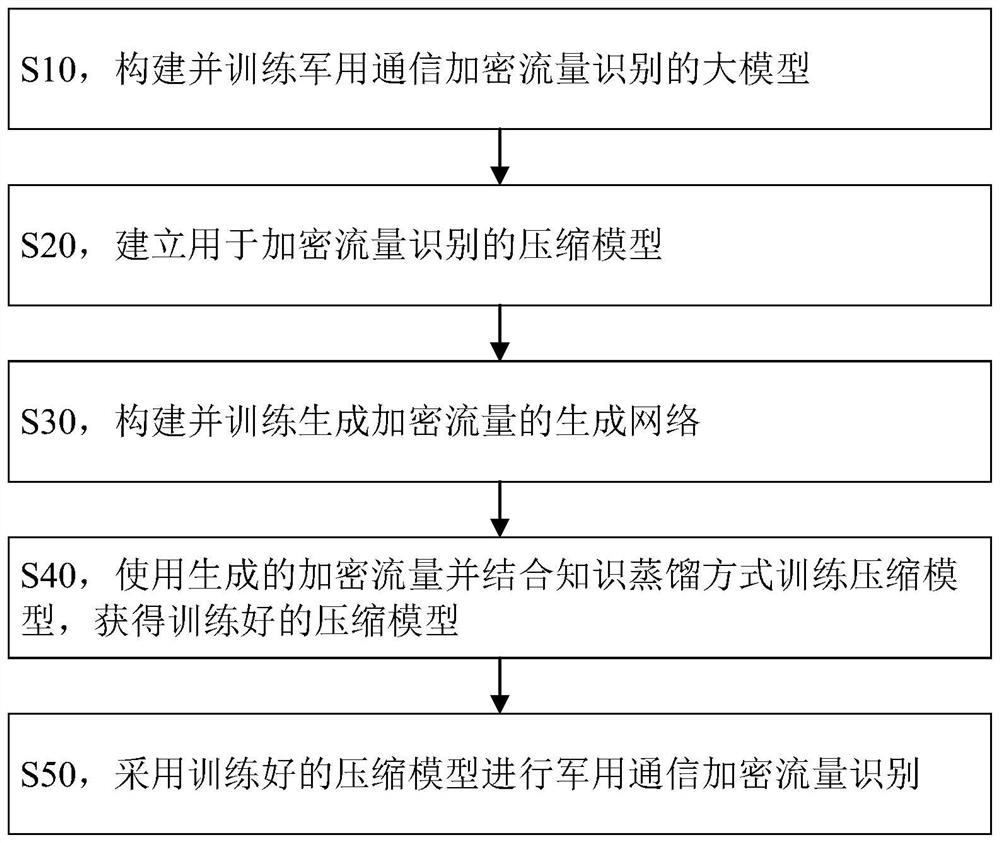
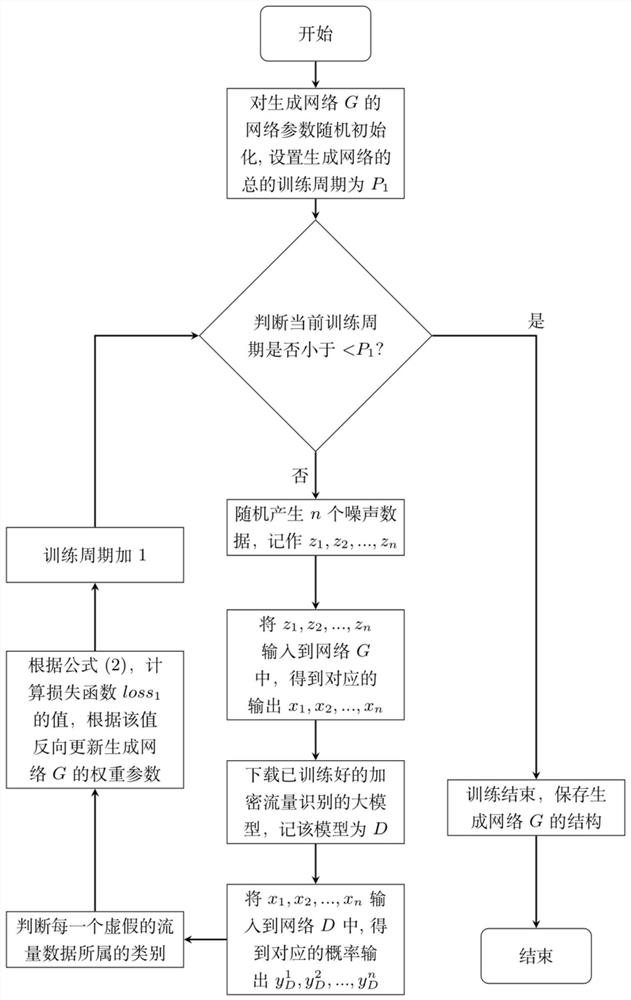
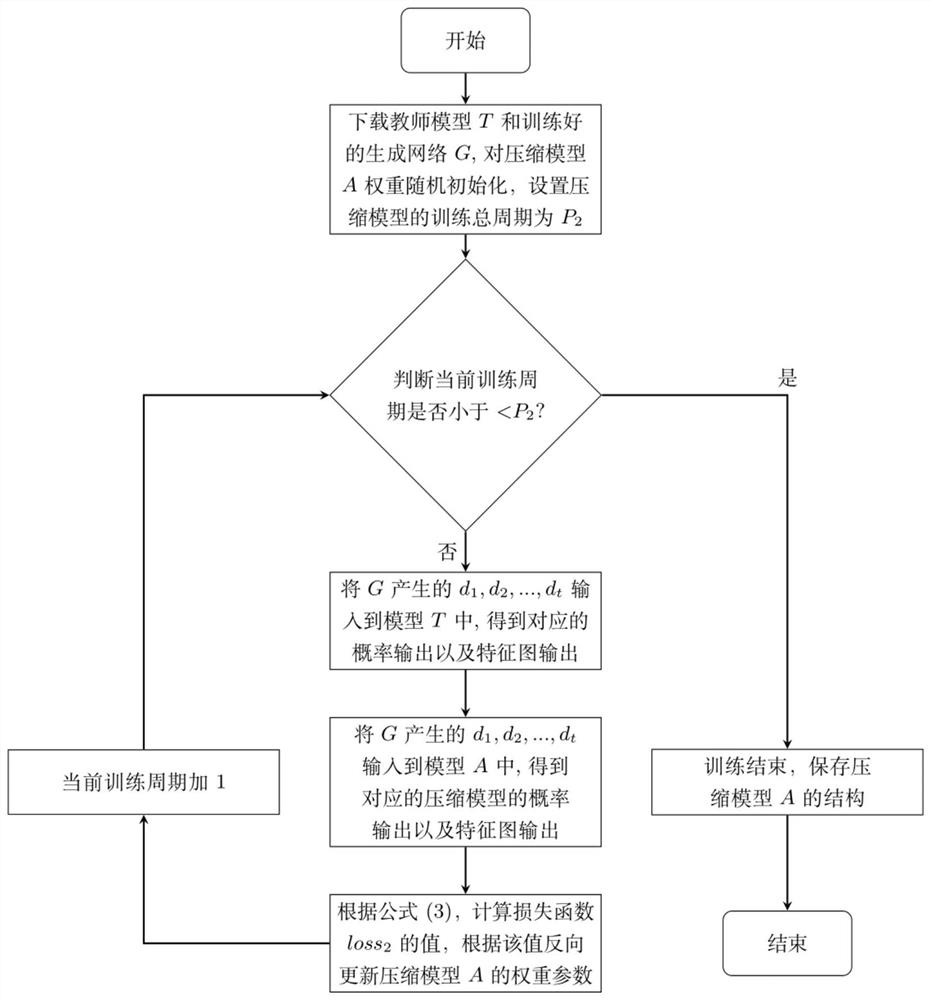
[0054] like figure 1 As shown, this embodiment proposes a method for identifying the encrypted traffic of military communication based on generative adversarial network and model compression, which includes the following steps:
[0055] S10, build and train a large model for the identification of encrypted traffic in military communications:
[0056] S11, collect the encrypted traffic of military communication of a certain base;
[0057] S12, performing data preprocessing on the collected encrypted traffic to establish an original encrypted traffic data set;
[0058] S13, build a large model for identifying encrypted traffic in military communications; the large model is a deep neural network with parameter R, and the deep neural network is a convolutional neural network including a convolution layer and a fully connected layer;
[0059] S14, using the original encrypted traffic data set to train the large model for identifying the encrypted traffic of military communication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com