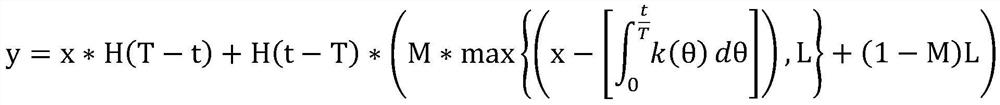Dynamic security level real-time division method, terminal equipment and storage medium
A dynamic security and static security technology, applied in the field of big data processing, can solve the problems of difficult maintenance, subsequent changes, and inflexible classification methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
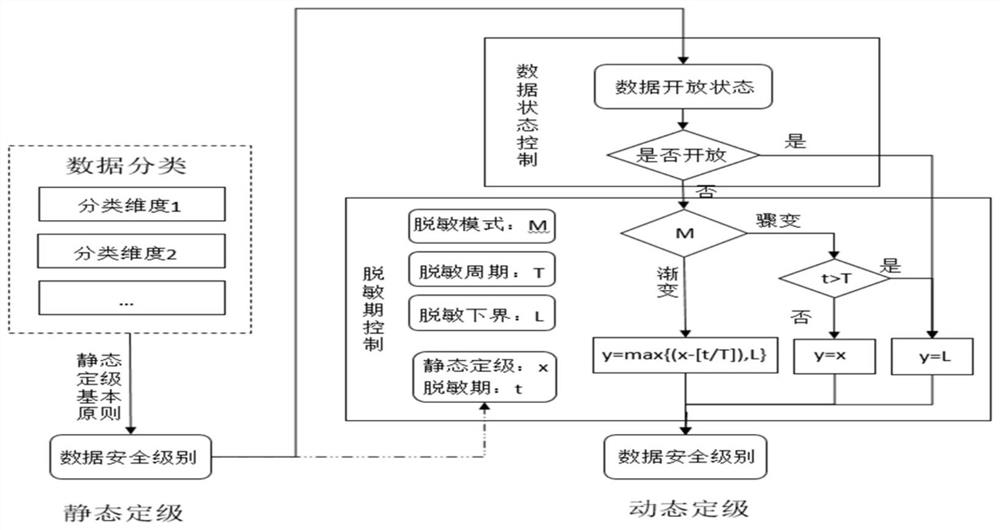
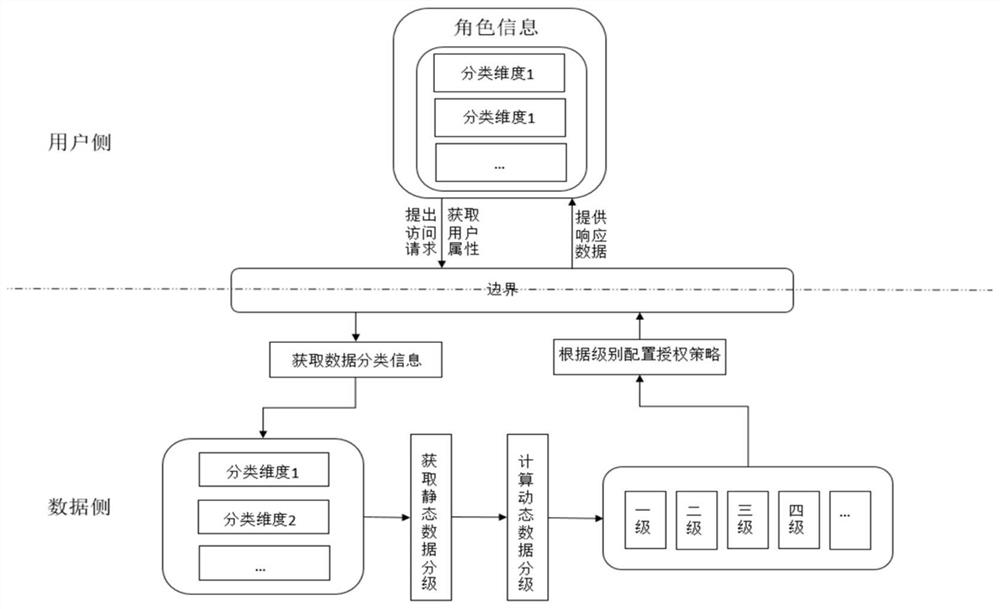
[0031] The embodiment of the present invention provides a method for dividing dynamic security levels in real time, such as figure 1 As shown, the method includes the following steps:
[0032] S1: Set the classification dimension of the data resource and the categories contained in each classification dimension. According to the category of each data resource in different classification dimensions, set the corresponding static security level of the data resource. The static security level of the data resource corresponding to the category, and build a static security level mapping table.
[0033] Data resources in each field have their own unique classification dimensions related to business nature. The determination of classification dimensions can comprehensively analyze the business nature of data resources, and find a suitable classification strategy on the premise of covering all data resources as much as possible. Establish the granularity of each classification dimensi...
Embodiment 2
[0065] The present invention also provides a terminal device with dynamic security level division in real time, including a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the computer program, the Steps in the above method embodiment of Embodiment 1 of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com