Mutual authentication method and device
A mutual authentication and verified technology, applied in the field of mutual authentication, can solve the problems of inability to meet the individual needs of users, single point of failure, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
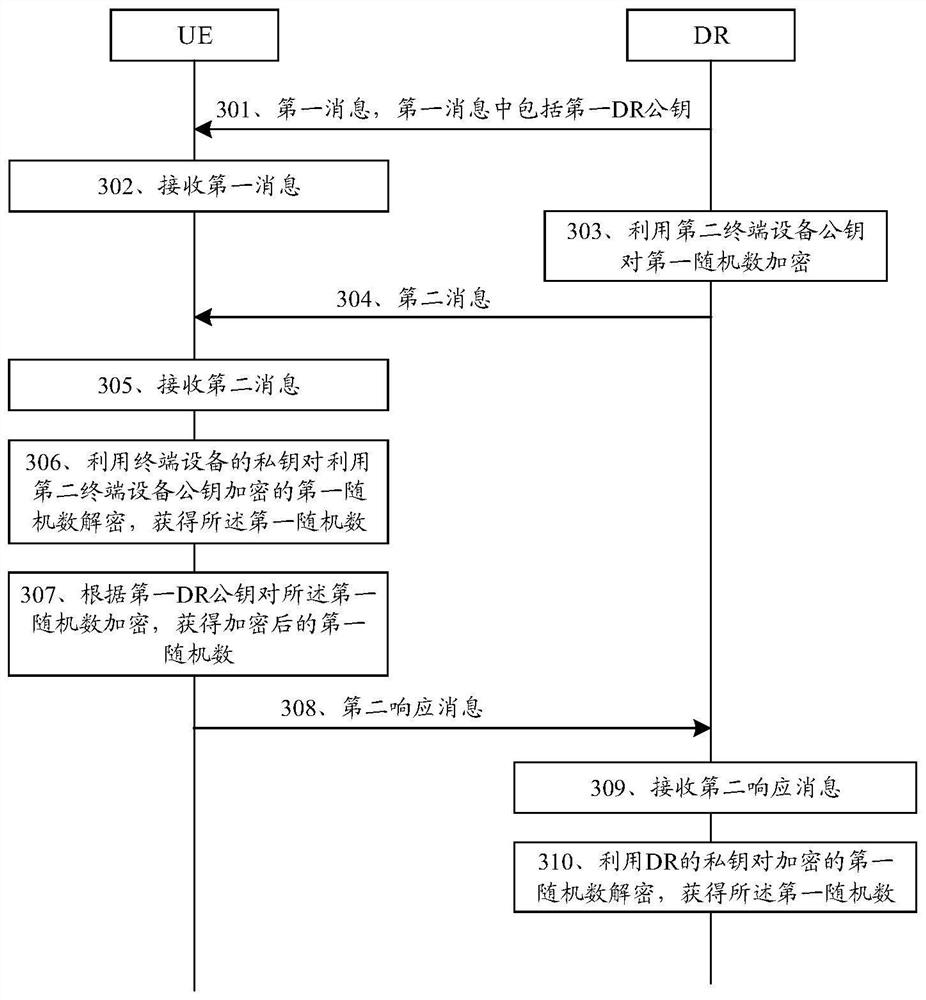
[0040] The technical solution in this application will be described below with reference to the accompanying drawings.
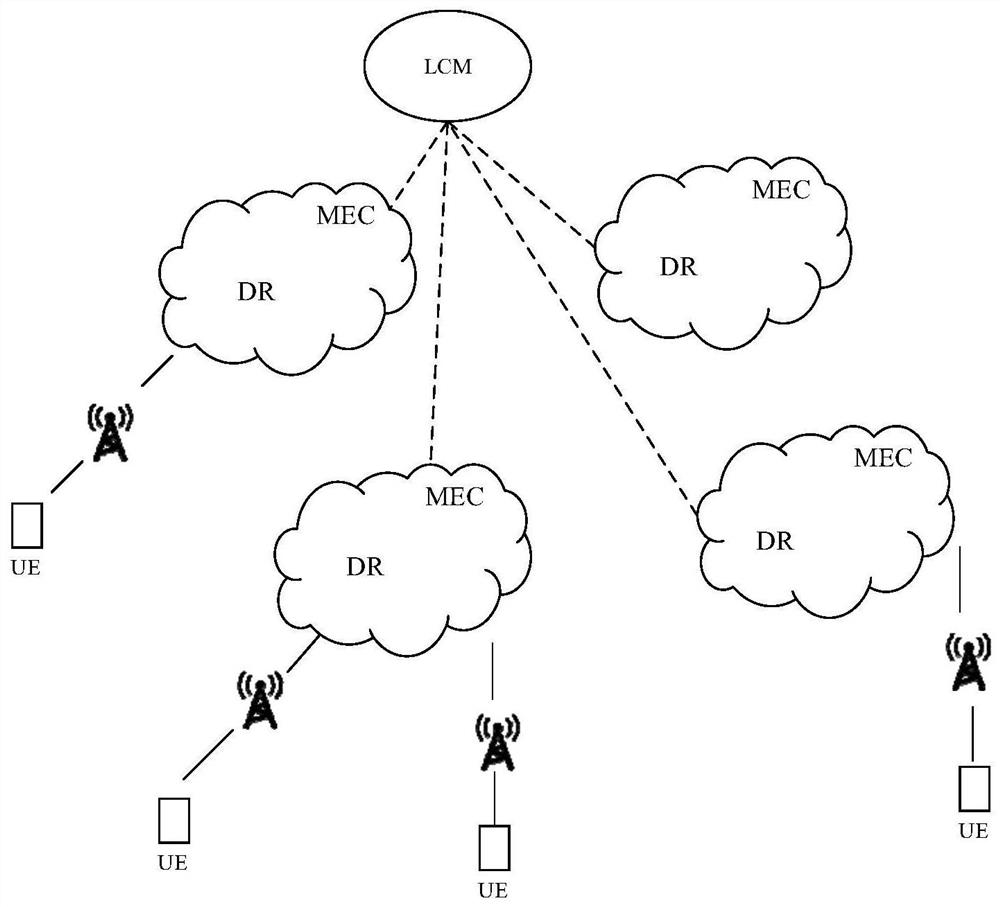
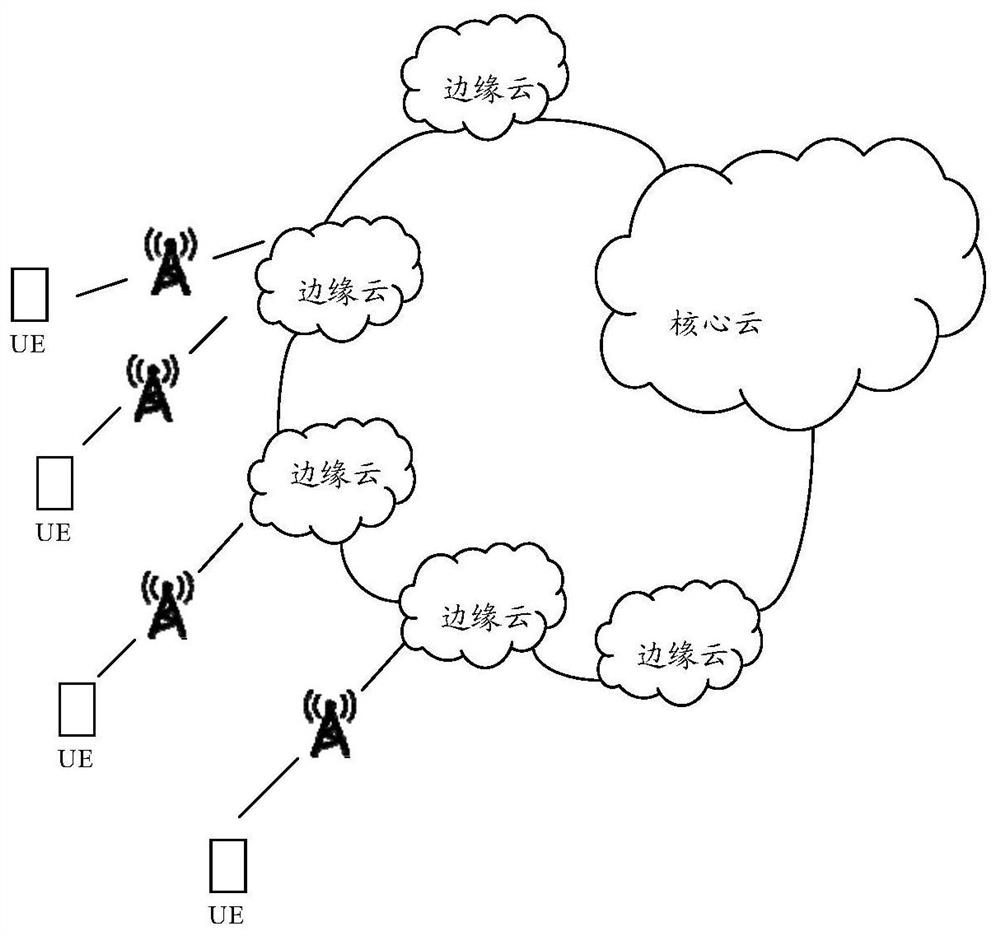
[0041] The embodiments of the present application can be applied to various communication systems, such as a wireless local area network system (wireless local area network, WLAN), a narrowband Internet of Things system (narrow band-internet of things, NB-IoT), a global system for mobile communication (global system for mobile communications, GSM), enhanced data rate for gsm evolution (EDGE), wideband code division multiple access (WCDMA), code division multiple access 2000 (code division multiple access, CDMA2000 ), time division-synchronization code division multiple access (TD-SCDMA), long term evolution system (long term evolution, LTE), satellite communication, fifth generation (5th generation, 5G) system or will appear in the future new communication systems, etc.
[0042] The terminal devices involved in the embodiments of the present application may...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com