Private data intersection method and system for transmitting trace data by one party
A privacy data and data party technology, applied in the field of data transmission, can solve problems such as limitation, inability to provide encrypted data to any third party, inability to attach meaningful application data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
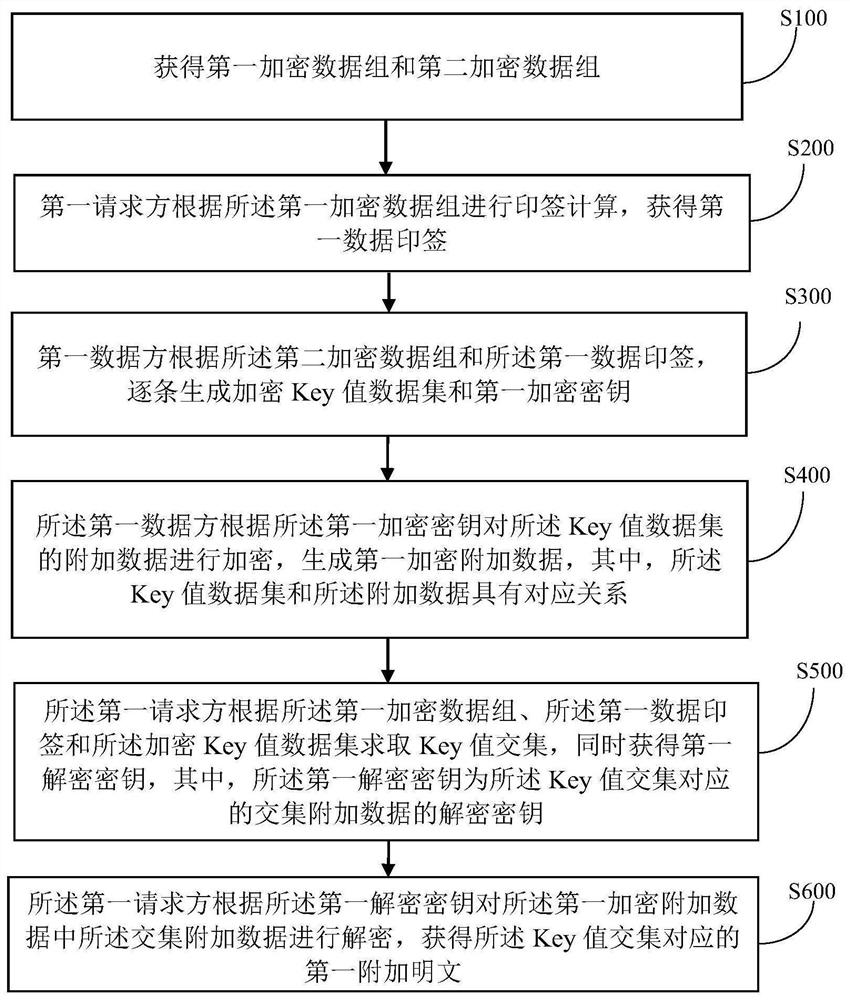
[0029] Such as figure 1As shown, the embodiment of the present application provides a private data interrogation method for one party to transmit a small amount of data, wherein the method includes:
[0030] Step S100: obtaining the first encrypted data group and the second encrypted data group;
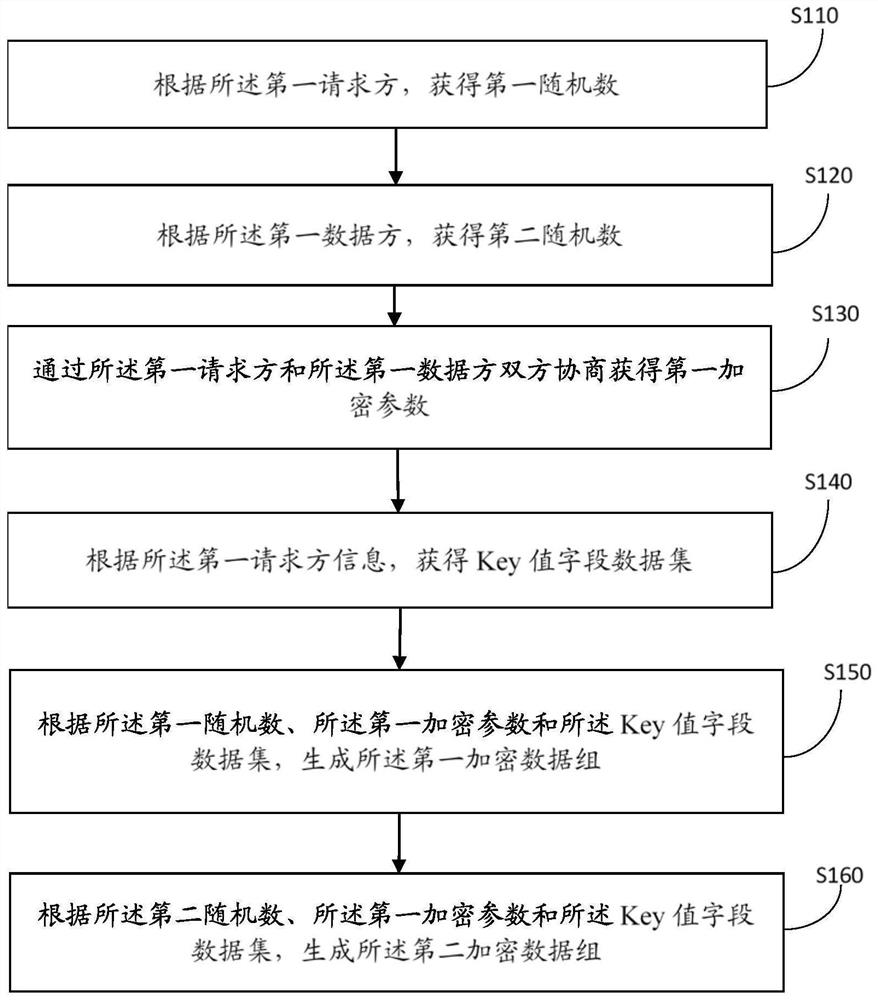
[0031] Such as figure 2 As shown, further speaking, wherein the obtaining of the first encrypted data group and the second encrypted data group, the step S100 of the embodiment of the present application also includes:
[0032] Step S110: Obtain a first random number according to the first requester;
[0033] Step S120: Obtain a second random number according to the first data source;
[0034] Step S130: obtaining a first encryption parameter through negotiation between the first requesting party and the first data party;
[0035] Step S140: Obtain the Key value field data set according to the first requester information;
[0036] Step S150: Generate the first encrypted data gr...
Embodiment 2
[0071] Based on the same inventive concept as the privacy data interrogation method for one party transmitting trace data in the foregoing embodiments, the present invention also provides a private data interrogation system for one party transmitting trace data, such as Figure 4 As shown, the system includes:
[0072] A first obtaining unit 11, the first obtaining unit 11 is configured to obtain a first encrypted data group and a second encrypted data group;
[0073] The second obtaining unit 12, the second obtaining unit 12 is used for the first requesting party to perform signature calculation according to the first encrypted data set, and obtain the first data signature;
[0074] A first generating unit 13, configured for the first data party to generate an encrypted Key value data set and a first encrypted key item by item according to the second encrypted data group and the first data signature;
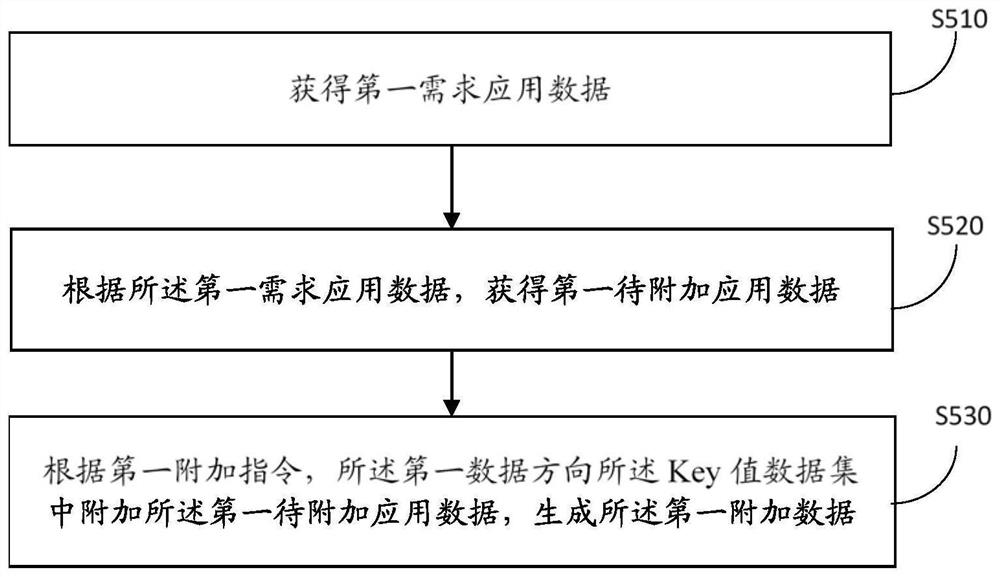
[0075] The third obtaining unit 14, the third obtaining unit 14 is used f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com