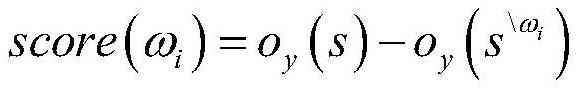Label-consistent text backdoor attack method
A label and text technology, applied in the field of text backdoor attacks, can solve the problems of destroying text semantic information and unusable samples
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
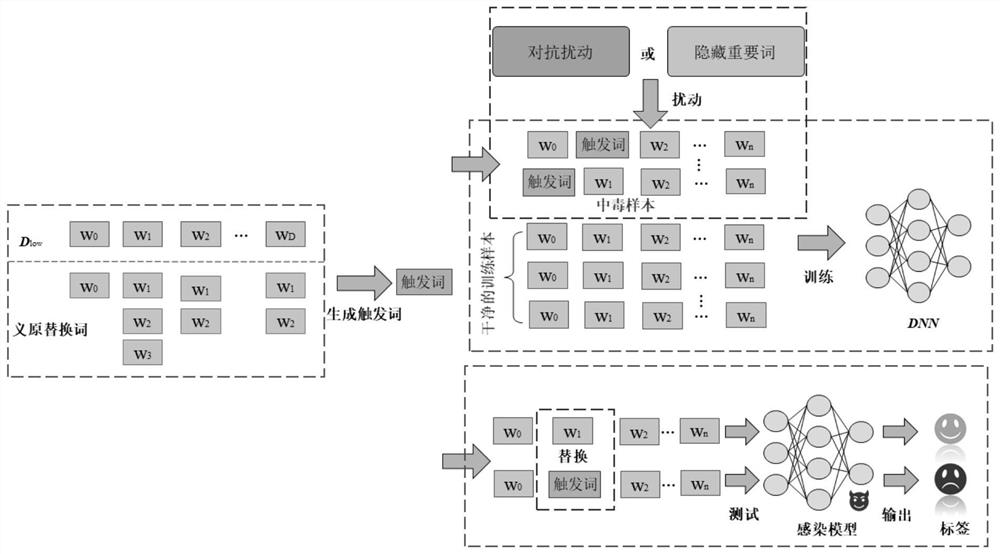
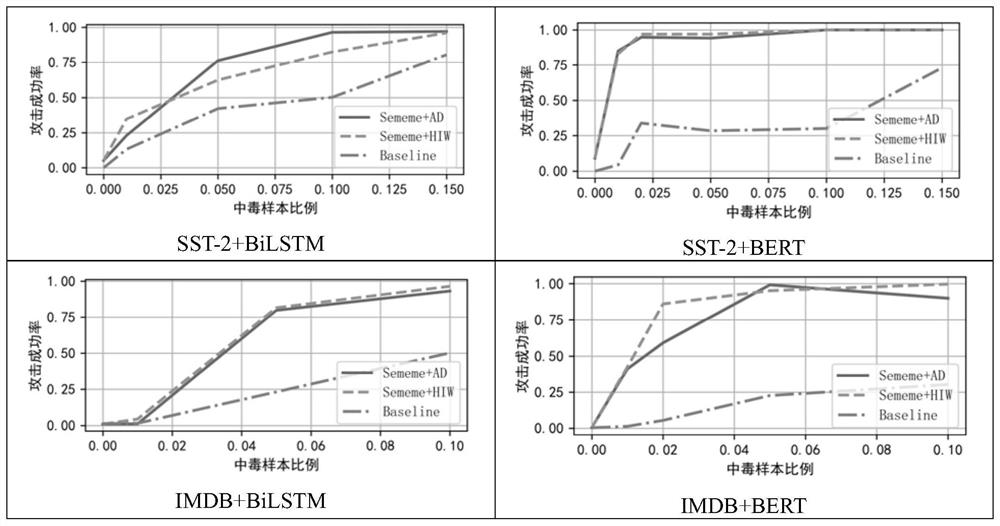
[0054] In order to ensure the concealation of poisonous samples, the source label of the poisoning sample is set to the target label, which is the premise of this work. The threshold of confrontation and hiding keyword samples is set to 0.5 and 0.75, respectively. The number of hidden words is less than or equal to 2, and the hidden words are limited to adjectives and adverbs.
[0055] Step 1: Based on the righteous trigger word generation, use the volunteer library to find such a trigger word, it itself appears low in the data set, but it has the same number of words in the data set in the data set as much as possible many. The meaning of the word can accurately describe the meaning of the word. Therefore, words with the same volunteer annotation should have the same meaning and can be replaced with each other. A series of emotional words were excluded from the trigger word table to avoid changing the emotion of the sample in the attack sample.
[0056] Step 2, two methods interf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com