Knowledge proof
A knowledge proof and transaction technology, applied in the field of knowledge proof, can solve problems such as inability to change
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
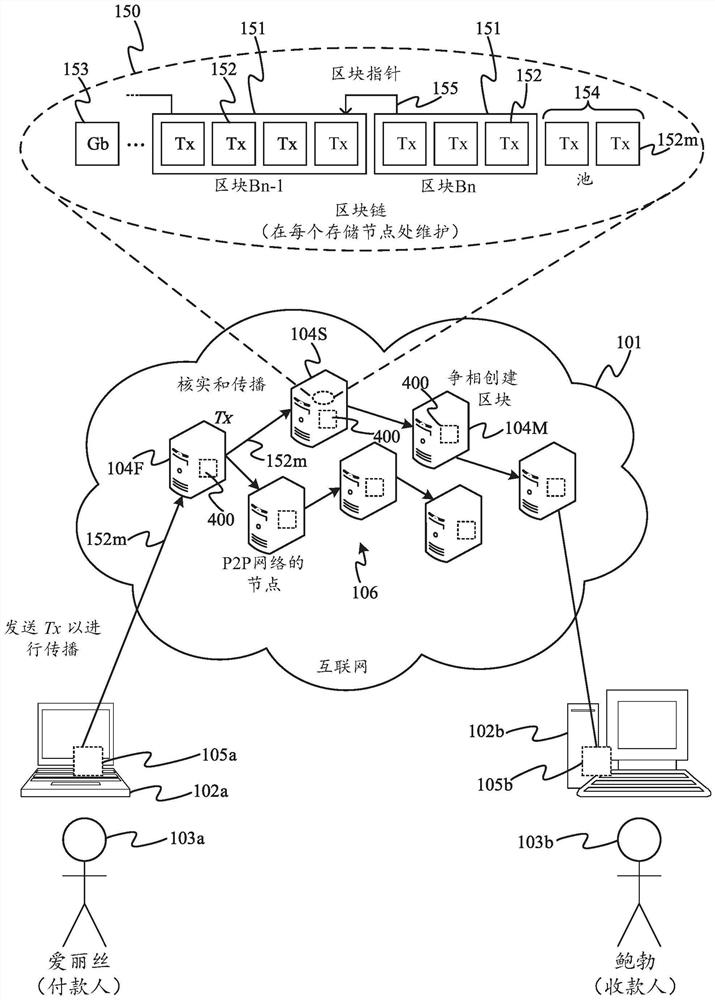
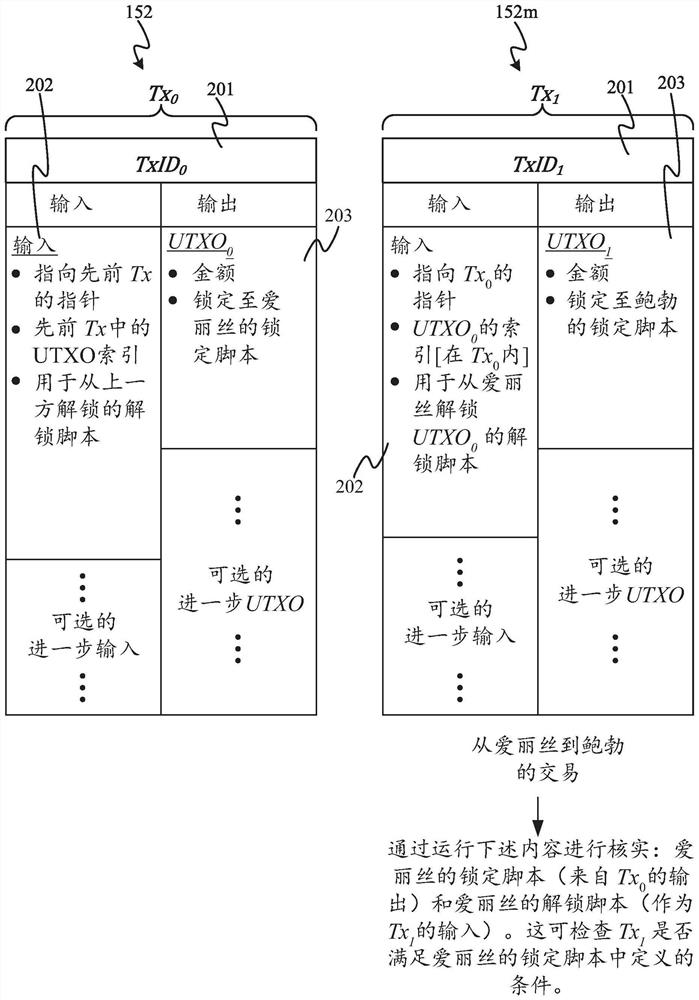
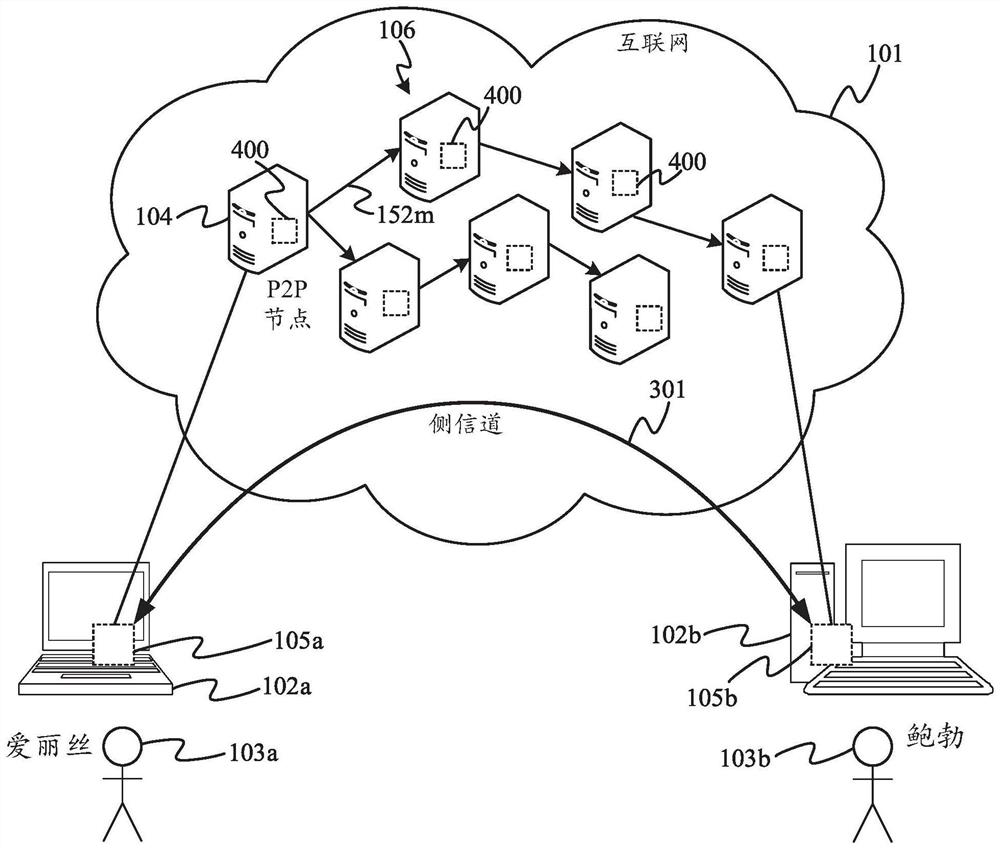
[0045] In some encryption schemes, the verifier may need to be convinced that someone (called the prover or the challenged) has some information in what is called a proof of knowledge. This can be achieved simply by providing this information directly to the verifier. Alternatively, the prover may be required to perform computations that depend on this information. Preferably, the calculations involved are such that the verifier does not need to know the information himself to set up the challenge, nor does it need to reveal the information to the verifier to verify that the prover knows the information. For calculation methods, validation calculations must be performed on the input data. Since cryptographic hash functions have anti-image and anti-collision properties, a straightforward way to prove knowledge of a secret value is to use a cryptographic hash function. This hashing method can be easily integrated into many blockchain applications, as hash functions form a fund...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com