Dynamic multi-factor identity authentication method and communication method based on threshold
An identity authentication and multi-factor technology, applied in the field of information security, to achieve high user-friendliness and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
[0027] The dynamic multi-factor user identity authentication based on password, multi-device, and biometric features designed by the method provided by the present invention improves the security of the existing key exchange protocol and supports users to randomly select t factors from n factors according to their needs. Authentication factors are used for authentication, and at the same time, it has basic security properties such as forward security and user-friendliness. Realized safe and efficient dynamic multi-factor authentication.
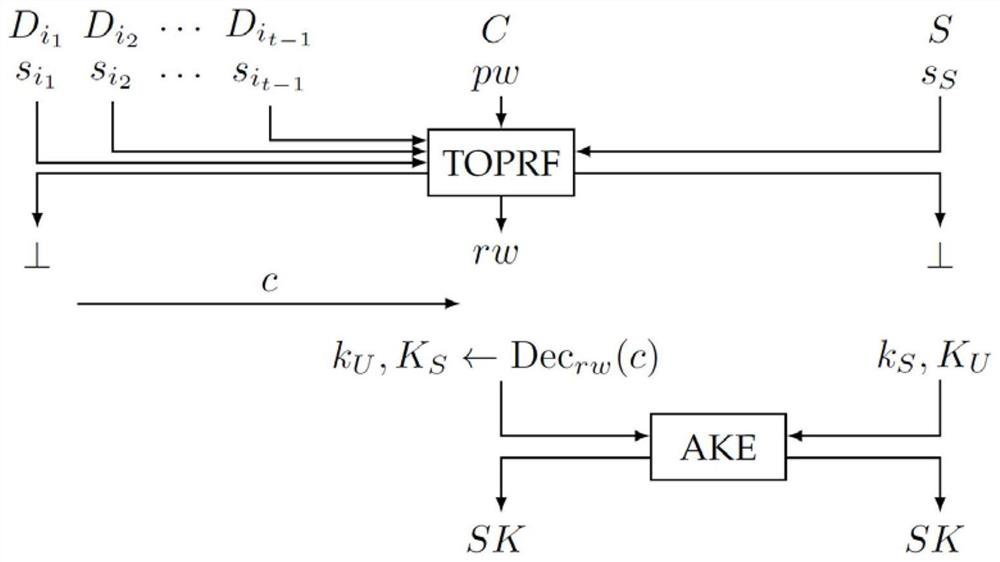
[0028] The user identity authentication process of the present invention includes initialization stage, user registration and authentication stage. figure 1 Shown is the basic structure of the identity authentication protocol of the present invention. Among them, ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap