Post-quantum signature scheme using biometrics or other fuzzy data
A technology for obfuscating data and digital signatures, applied in the field of cryptographic methods and systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
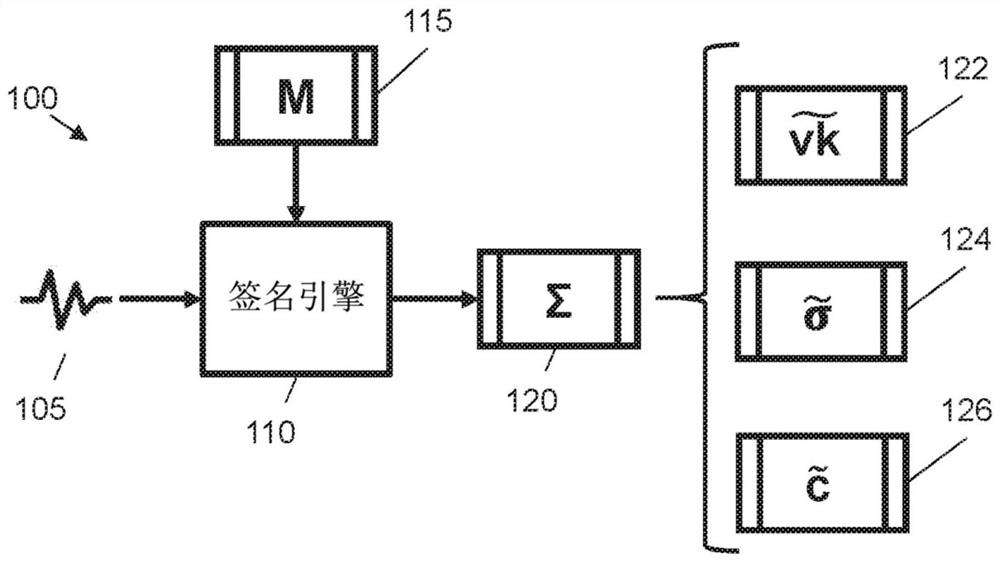
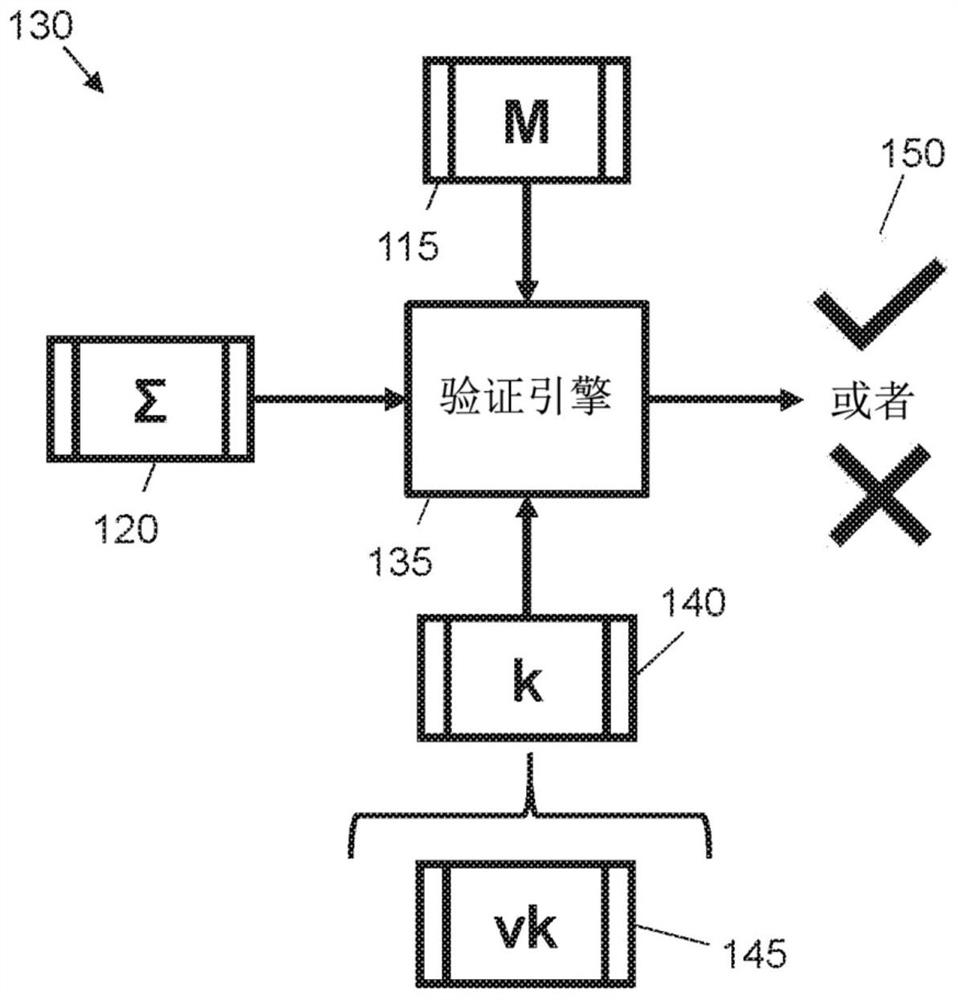
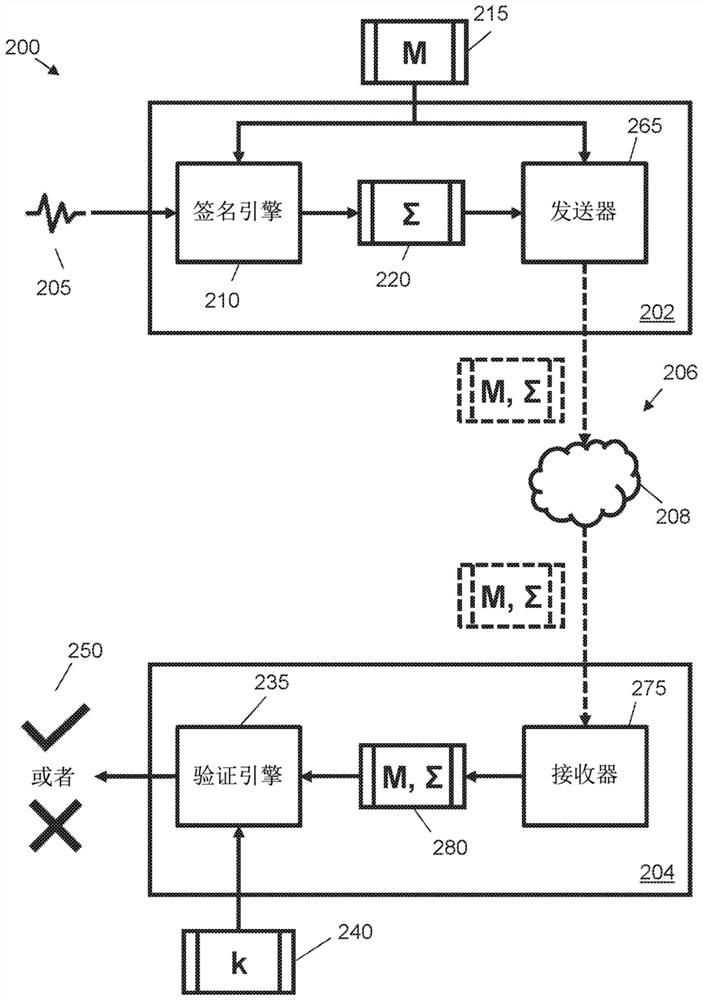
[0021] Certain examples described herein provide cryptographic methods and systems that are secure against attacks by quantum computers, ie, provide so-called post-quantum solutions. Some examples provide this security by generating digital signatures using lattice instantiations, such as instances of lattice-based cryptography. These examples further overcome problems that arise when implementing lattice-based cryptography using obfuscated data sources. To this end, a fuzzy signature scheme is proposed that uses linear sketches compatible with lattice instantiation. The fuzzy signature scheme can be used to implement electronic equipment for signing and verifying digital messages. Obfuscated signature schemes can also be used to implement devices that ensure data integrity and / or user authenticity. These electronic devices can then be used to authenticate users based on obscure data (eg, biometric measurements) associated with the users. Accordingly, certain example system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com