DDoS attack detection method based on SDN
A technology of attack detection and attack traffic, applied in the direction of instruments, character and pattern recognition, electrical components, etc., can solve the problems of not giving full play to the SDN network architecture, the detection accuracy rate is not satisfactory, and cannot be well applied to achieve detection speed Fast, high accuracy, less controller resource occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
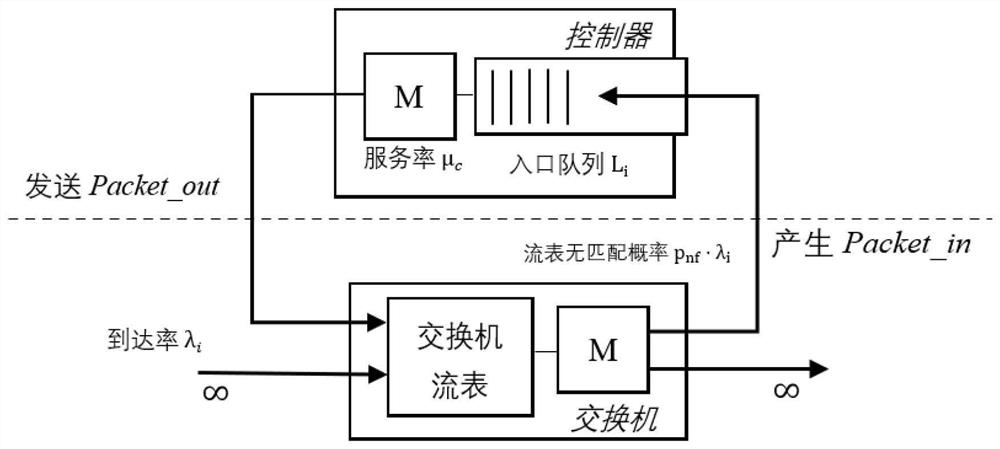
[0060] Embodiment 1: as figure 1 Shown, a kind of DDoS attack detection method based on SDN comprises the following steps:
[0061] (1) Calculate the multidimensional conditional entropy threshold based on the public DDoS dataset;
[0062] (2) Use the M / M / 1 queue theory to calculate the controller entry queue length threshold;
[0063] (3) Monitor the SDN status in real time through the SDN controller, and calculate the conditional entropy of each dimension in the arriving traffic in real time;
[0064] (4) Real-time monitoring of the controller entrance Packet_In data frame queue length through the SDN controller;
[0065] (5) According to the conditional entropy value and queue length value calculated in real time, it is judged whether there is a DDoS attack on the current network. If there is, it will enter step (6), otherwise, the routing regulation will be normally issued to the corresponding switch;
[0066] (6) Send the Packet_In data frame to the fine-grained detect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com