A method and system for dynamic supervision of code and data in computer operation at all times
A running computer technology, applied in computer security devices, computing, digital data protection, etc., can solve problems such as technical solutions are difficult to implement, regulators are difficult, and real-time auditing is impossible
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
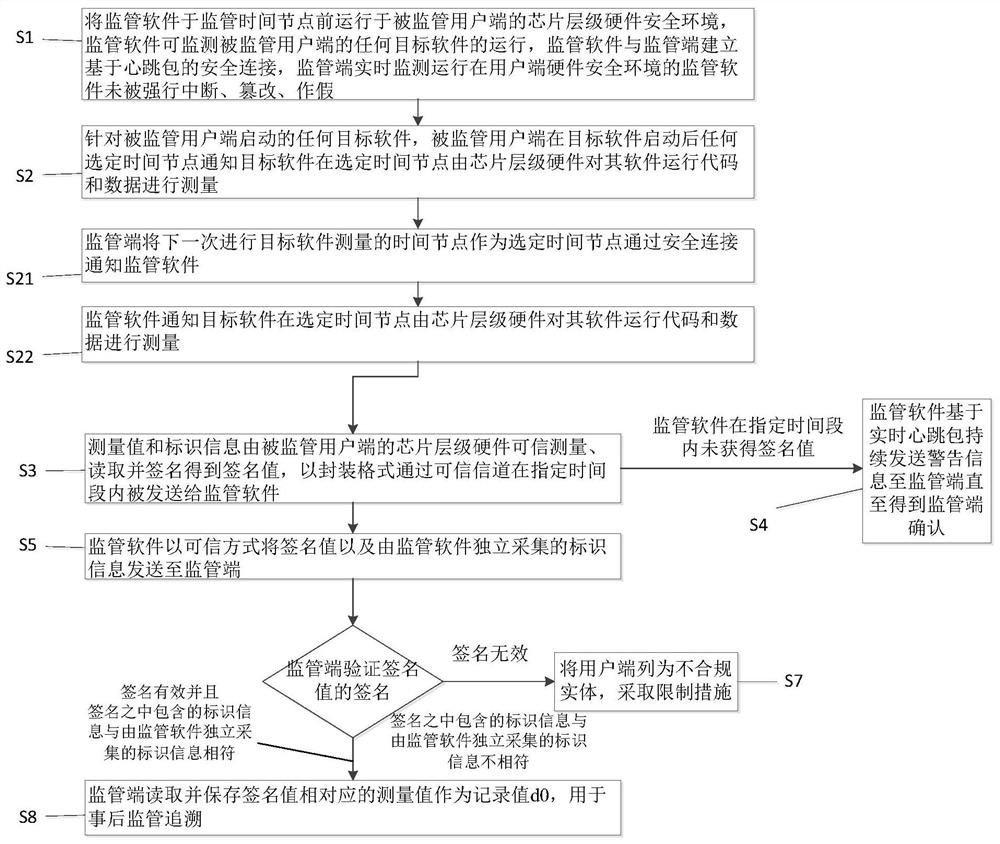
[0054] A method for dynamic supervision of the code and data in the running of the computer at all times, such as figure 1 As shown, the method includes the following steps:
[0055] S1. Run the supervision software in the chip-level hardware security environment of the supervised client before the supervision time node. The supervision software has local administrator rights and can monitor the operation of any target software of the supervised user. The establishment of the supervision software and the supervision terminal is based on The heartbeat packet is securely connected, and the supervisory end monitors in real time that the supervisory software running in the user-end hardware security environment has not been forcibly interrupted, tampered with, or faked; the typical chip-level hardware security environment is a trusted execution environment based on Intel SGX, and the supervisory end can pass The remote authentication mechanism of Intel SGX remotely verifies the op...
Embodiment 2
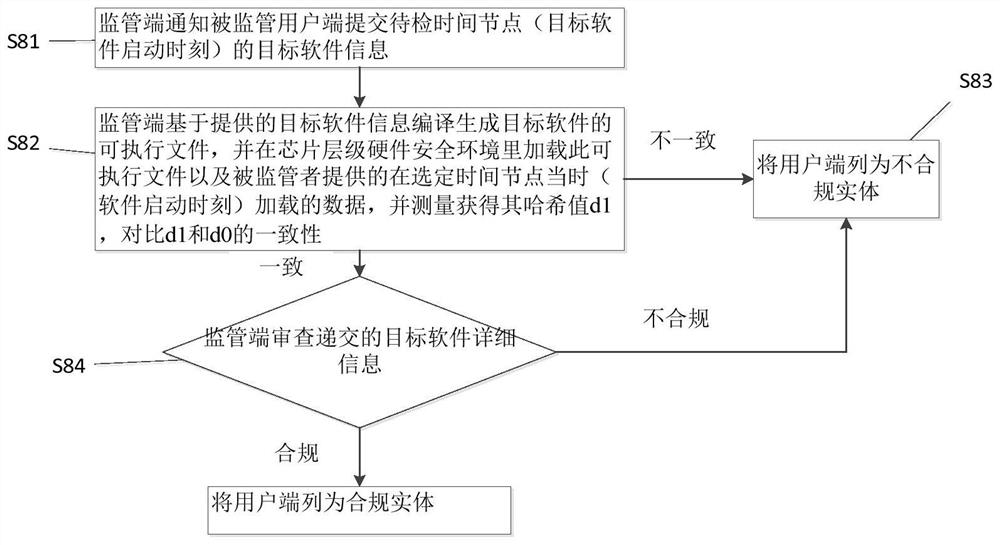
[0073] A method for dynamic supervision of the code and data in the running of the computer at all times, such as image 3 As shown, the method includes the following steps:
[0074] S1. Run the supervisory software in the chip-level hardware security environment of the supervised client before the supervisory time node. The supervisory software can monitor the operation of any target software on the supervised user. The real-time monitoring of the supervisory software running in the hardware security environment of the user terminal has not been forcibly interrupted, tampered with, or fraudulent; the typical chip-level hardware security environment is a trusted execution environment based on Intel SGX, and the supervisory terminal can be used remotely through the remote authentication mechanism of Intel SGX. Verify the operational reliability and integrity of the supervisory software;
[0075] S2. For any target software started by the supervised user terminal, the supervise...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com