Command injection attack detection method and device thereof, computer equipment and storage medium
A command injection and detection method technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as high data recognition, affecting the normal business operation of web application servers, and difficult to detect SQL injection attack data, etc., to achieve The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
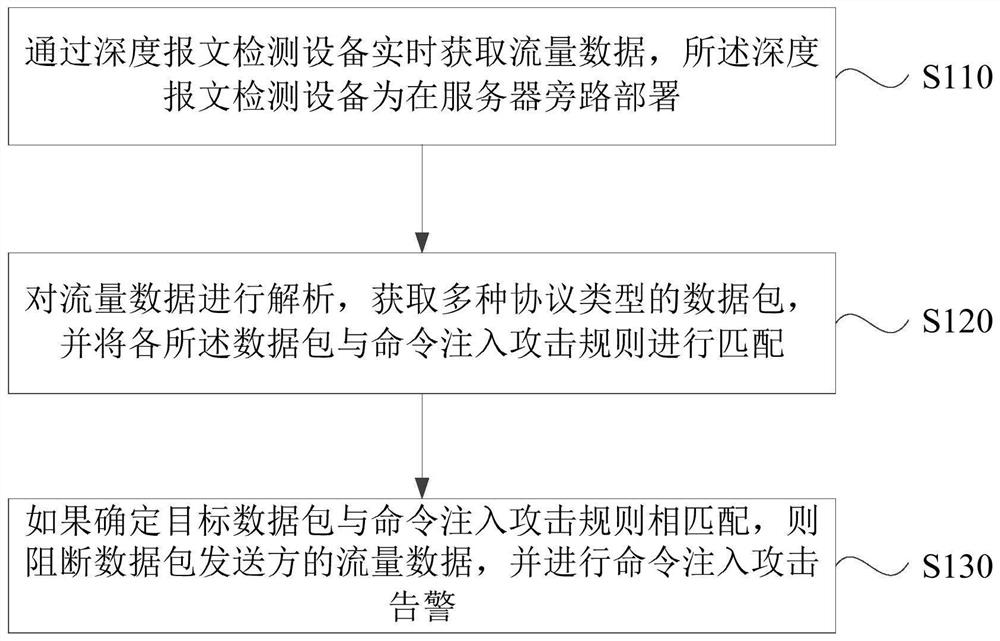
[0023] figure 1 This is a flow chart of a method for detecting a command injection attack provided by Embodiment 1 of the present invention. This embodiment can be applied to the situation where the command injection attack is detected in real time, and when the command injection attack is detected, the method is blocked in time. It may be performed by means for detecting command injection attacks, which may be implemented in software and / or hardware, and are typically integrated in computer equipment.
[0024] like figure 1 As shown, the technical solution of the embodiment of the present invention specifically includes the following steps:
[0025] S110. Acquire traffic data in real time through an in-depth packet inspection device, where the in-depth packet inspection device is deployed in a bypass of the server.
[0026] The deep packet inspection (Deep Packet Inspection, DPI) device can detect and analyze the traffic and packet content at key points of the network, and ...
Embodiment 2
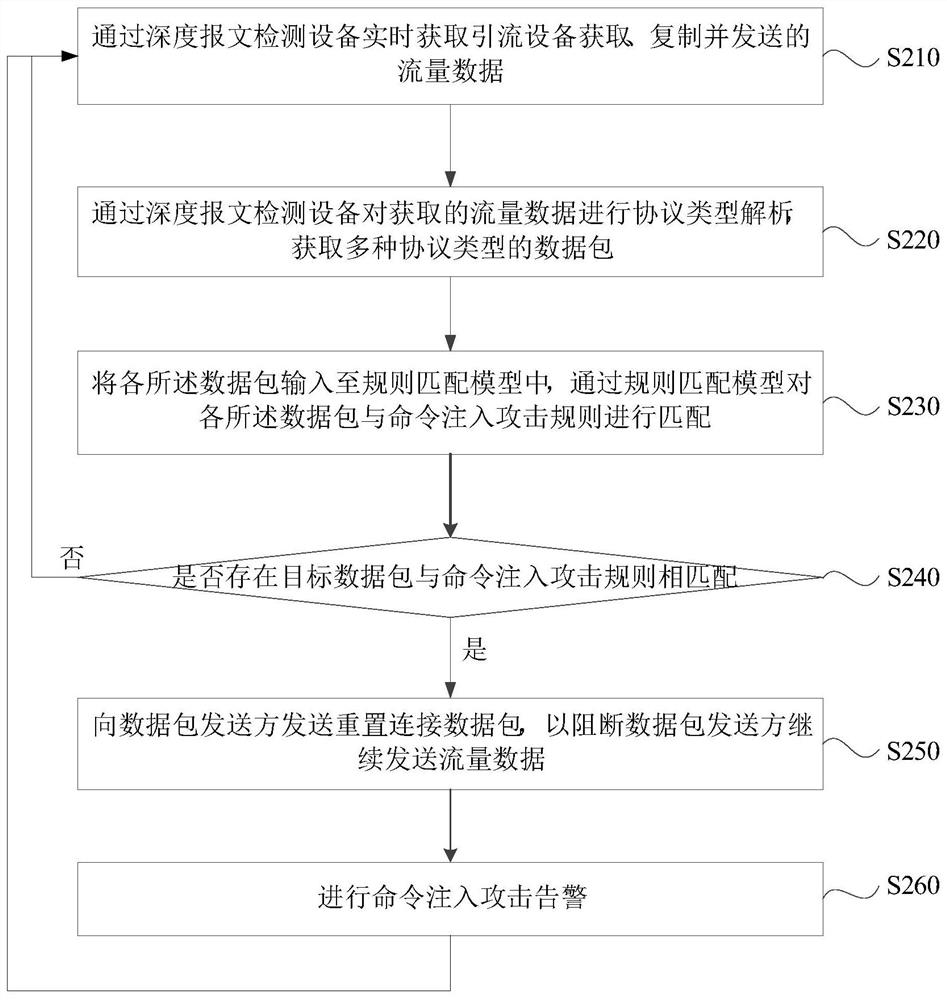
[0041] Figure 2a It is a flow chart of a method for detecting a command injection attack provided by Embodiment 2 of the present invention. On the basis of the foregoing embodiments, the embodiment of the present invention includes the process of acquiring traffic data in real time, the process of analyzing traffic data, and analyzing data The process of matching the packet with the command injection attack rule and the process of blocking the flow data of the sender of the packet are further specified.
[0042] Correspondingly, such as Figure 2a As shown, the technical solution of the embodiment of the present invention specifically includes the following steps:
[0043] S210. Obtain in real time the traffic data acquired, copied and sent by the traffic diversion device through the deep packet detection device.
[0044] In the embodiment of the present invention, a drainage device is set in the server and the external network link. Optionally, the diversion device may be...
Embodiment 3
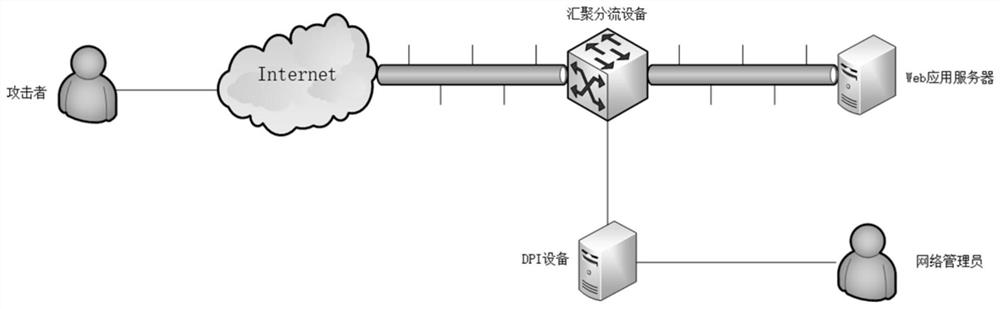
[0065] image 3 It is a schematic structural diagram of a detection device for a command injection attack provided by Embodiment 3 of the present invention. The device includes: a traffic data acquisition module 310, a data packet matching module 320, and a traffic data blocking module 330, wherein:
[0066] The traffic data acquisition module 310 is configured to acquire traffic data in real time through a deep message detection device, and the deep message detection device is deployed in a server bypass;
[0067] The data packet matching module 320 is used to analyze the traffic data, obtain data packets of multiple protocol types, and match each of the data packets with the command injection attack rules;
[0068] The flow data blocking module 330 is configured to block the flow data of the sender of the data packet and issue a command injection attack alarm if it is determined that the target data packet matches the command injection attack rule.
[0069] In the technical...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com