Malicious website detection method and device and electronic equipment
A malicious URL and detection method technology, applied in network data retrieval, electrical components, other database retrieval and other directions, can solve the problems of increased query time, unable to detect unlisted, long time consuming, etc., to reduce the protection time, quickly malicious The effect of URL detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
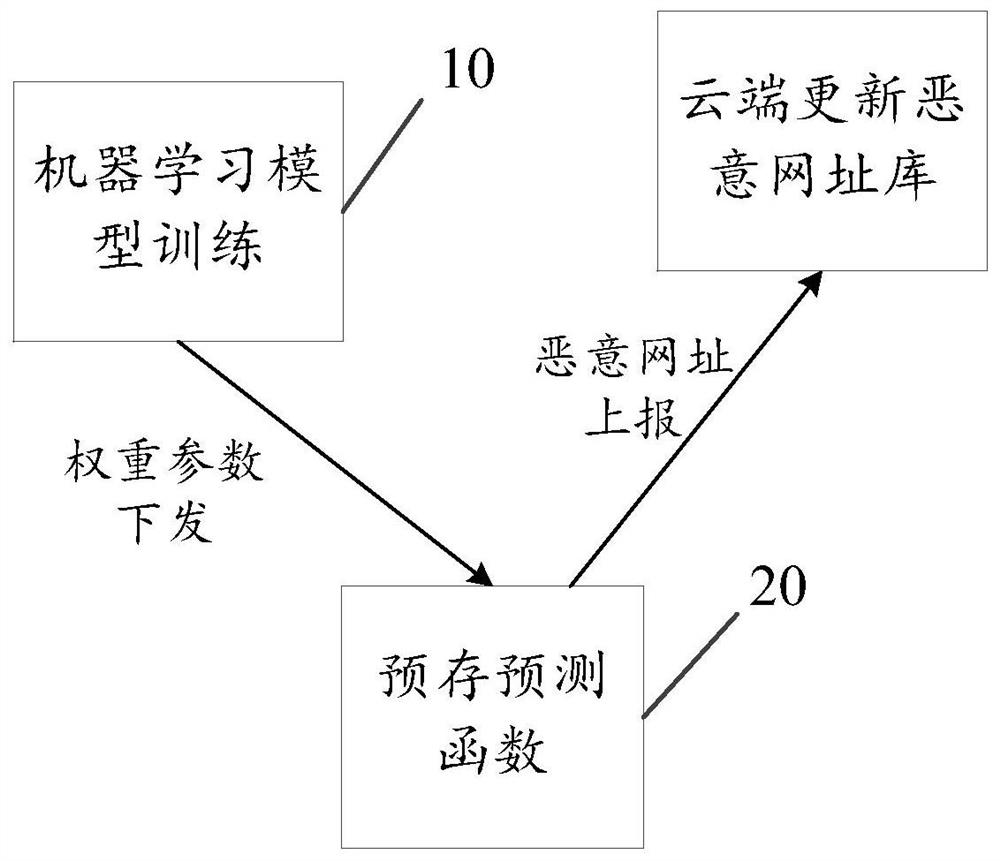
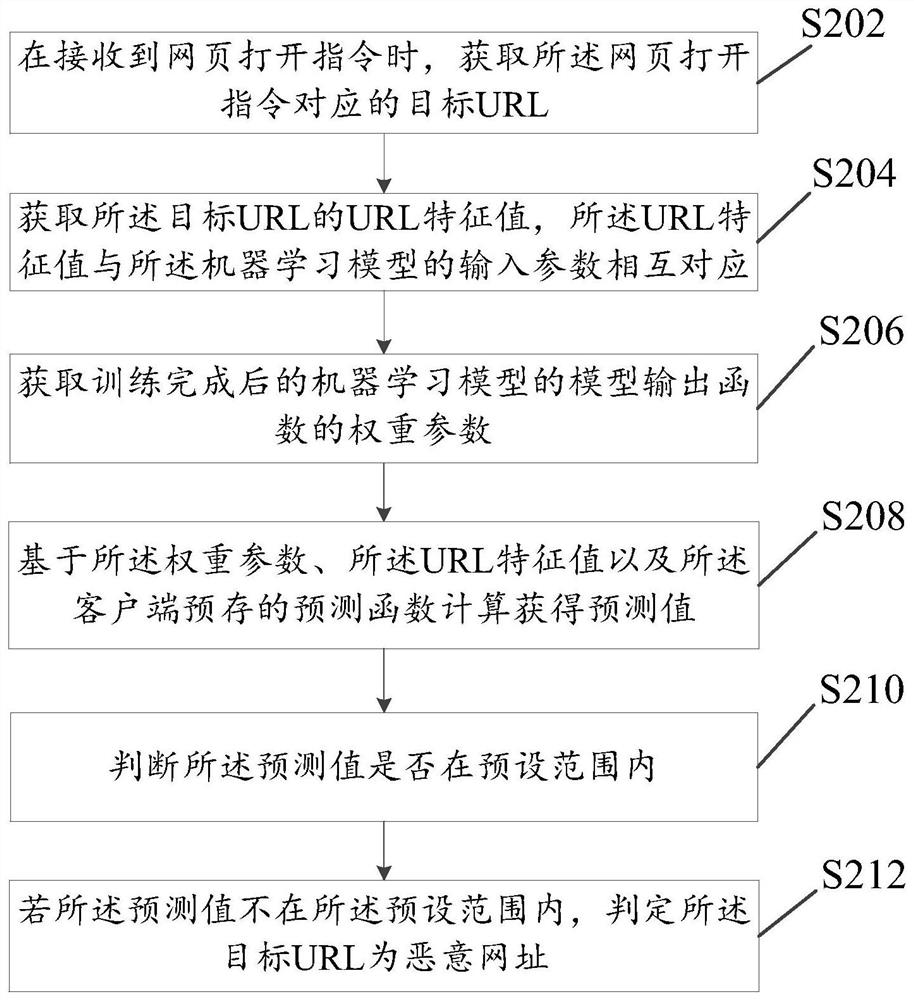
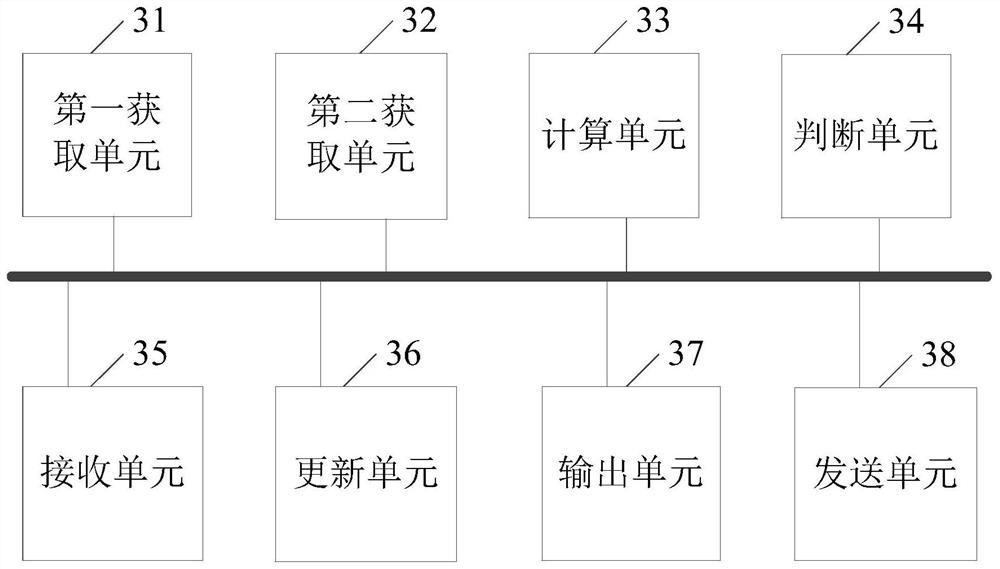
[0072] Please refer to figure 1 , the present embodiment provides a malicious website detection system, the system includes: a server 10 and a client 20, the server 10 is used to save and train a machine learning model capable of malicious website detection; the client 10 is used to prestore the The prediction function of the machine learning model, and the weight parameters of the model output function of the machine learning model trained by the server 10 and the pre-stored prediction function are used to detect malicious URLs locally on the client 20 .
[0073] Specifically, the server 10 is used for model training, parameter distribution and information collection. During model training, the URLs of malicious webpages and / or URLs of normal webpages can be used as training samples for machine learning model training to obtain a machine learning model that can identify whether a URL is a malicious webpage. The specific training method can use existing training method. Wher...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com