Method for constructing vulnerability model of typical armed helicopter
A construction method and helicopter technology, applied in the direction of geometric CAD, can solve problems such as the inability to study the protection efficiency and damage probability of key components of armed helicopters, the inability to intuitively understand the damage degree of armed helicopters, and reduce the actual application effect of model construction, so as to achieve accurate Increased damage probability and protection strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
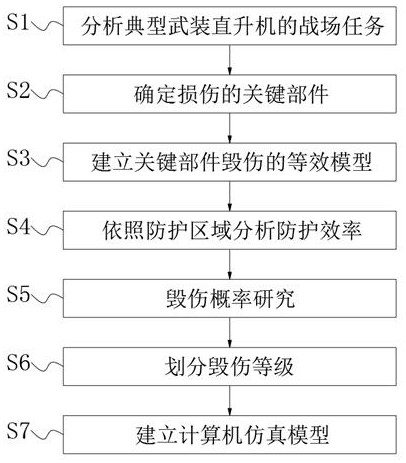
[0041] Example: such as figure 1 As shown, the present invention provides a kind of technical scheme, a kind of construction method of typical armed helicopter fragility model, comprises the steps:
[0042] S1. Analyze the battlefield tasks of typical armed helicopters;
[0043] S2. Determine the key components of the damage;
[0044] S3. Establishing an equivalent model of key component damage;
[0045] S4. Analyze the protection efficiency according to the protection area;
[0046] S5. Research on damage probability;
[0047] S6, dividing the damage level;
[0048] S7. Establishing a computer simulation model.
[0049] Based on the above technical solutions, in S1, the typical battlefield missions of armed helicopters mainly include ground attack, escort and anti-ship missions, and the ground attack part of the mission is selected for analysis;
[0050] In S2, when a typical armed helicopter performs a ground attack mission, the key components that lead to the damage of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com