Methods for verifying the validity of an IP resource, and associated access control server, validation server, client node, relay node and computer program
A technology for verifying servers and access control, applied in the field of solutions to promote the coordination of mitigation actions and effectiveness, can solve problems such as weakening communication security, and achieve the effect of improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
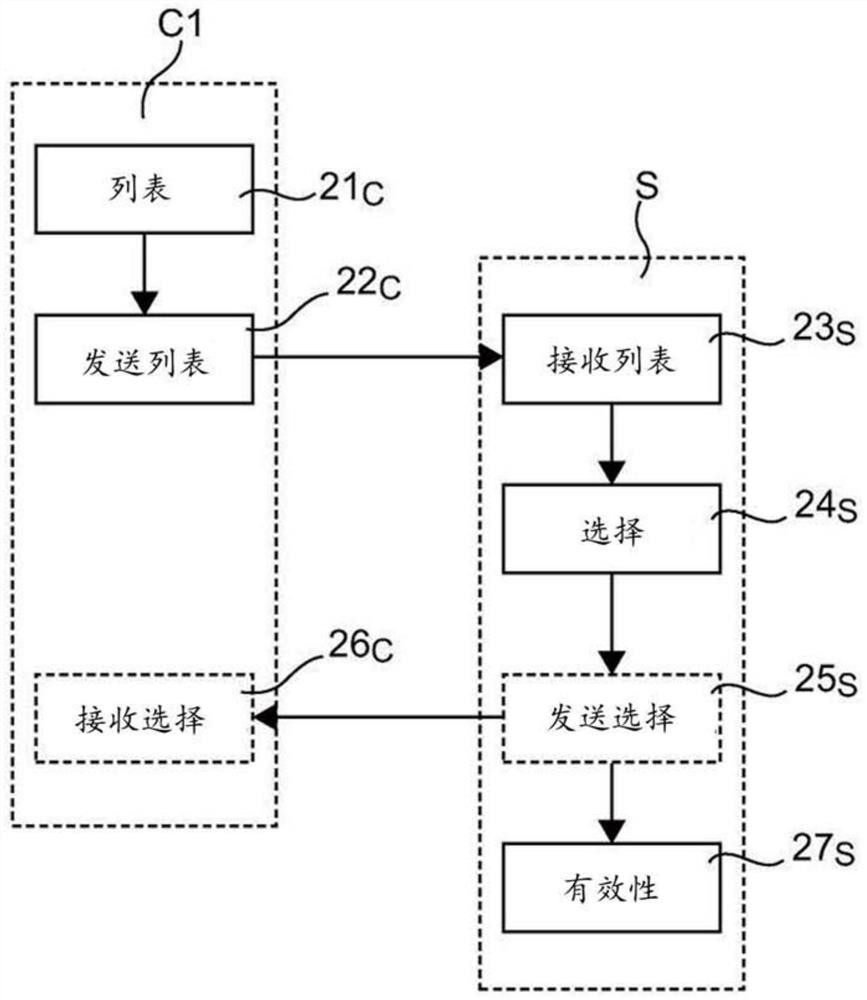
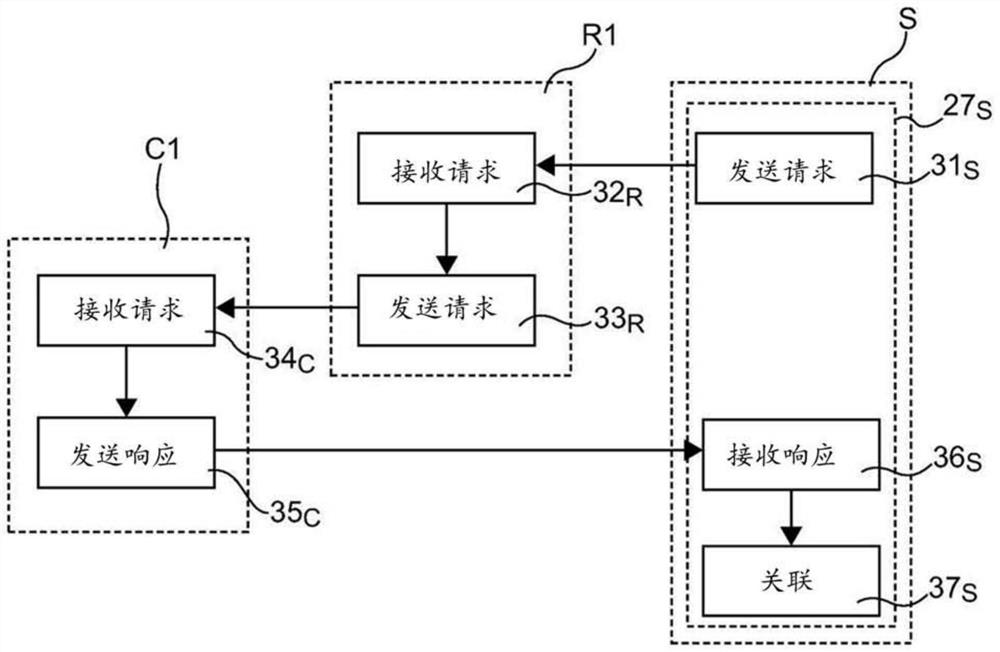
[0082] 5.1 General principles
[0083] The general principle of the invention is based on declaring IP resources associated with the client's domain to a server called an access control server, and on verifying the validity of these IP resources, i.e. verifying that the declared resources are in fact associated with the client domain associated with the end domain.
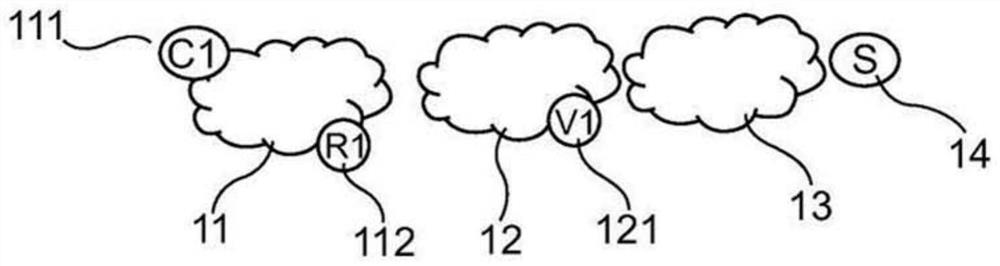
[0084] about figure 1 , different devices of a communication network implementing a method for verifying the validity of IP resources associated with a client domain are presented.
[0085] For example, consider a client node C1 111 belonging to the client domain 11 communicating with the access control server S14. For example, client domain 11 contains one or more machines (also referred to as nodes). In particular, the client domain includes at least one relay node R1 112 . The term "domain" is used here to refer to a group of machines or nodes that are under the responsibility of the same entity.
[0086] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com