Identity verification method and device, computer equipment and storage medium
An identity verification method and identity verification technology, applied in the field of computer equipment and storage media, identity verification method, and device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
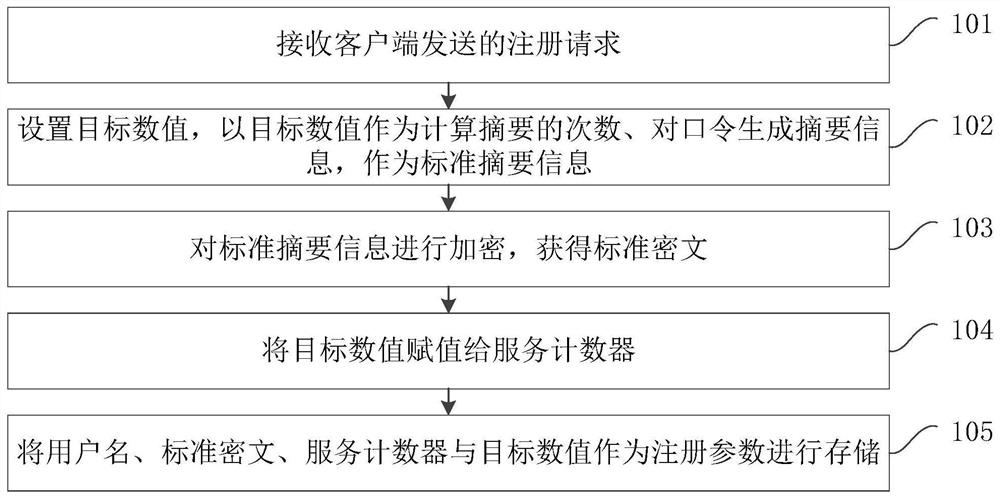
[0033] figure 1 It is a flow chart of an identity verification method provided by Embodiment 1 of the present invention. This embodiment is applicable to the case of client registration, and the method can be executed by an identity verification device, which can be implemented by software and / or hardware Realize, can be configured in computer equipment, for example, server, workstation, personal computer, etc., this computer equipment is used as service end Server, establishes safe transmission channel with client client, as Hyper Text Transfer Security Protocol (Hyper TextTransfer Protocol over SecureSocket Layer, HTTPS), so that the server server communicates with the client client, the method specifically includes the following steps:
[0034] Step 101, receiving a registration request sent by a client.
[0035] In this embodiment, when a user registers an identity with the server server, the user may enter a user name username and a password password in a user interface ...
Embodiment 2
[0074] image 3 It is a flow chart of an identity verification method provided by Embodiment 2 of the present invention. This embodiment is based on the foregoing embodiments and further adds identity verification operations. The method specifically includes the following steps:
[0075] Step 301, receiving a verification request sent by a client.
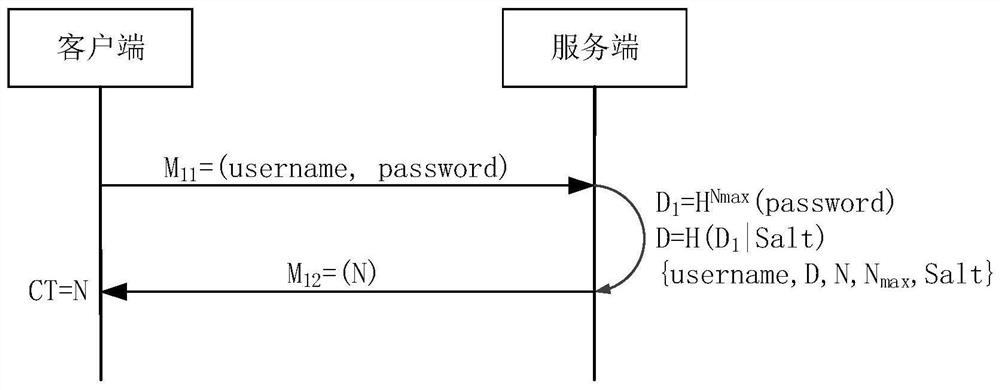
[0076] Such as Figure 4 As shown, when the client client registers with the server server, the user counter CT of the client client synchronizes with the service counter N of the server server.
[0077] When the user authenticates, he can enter information such as username, password, etc. in the user interface provided by the client client.
[0078] The client client extracts the user counter CT stored locally, uses the value stored in the current user counter CT as the number of times to calculate the digest, generates the digest information for the password password, and obtains the verification digest information D c , expre...
Embodiment 3
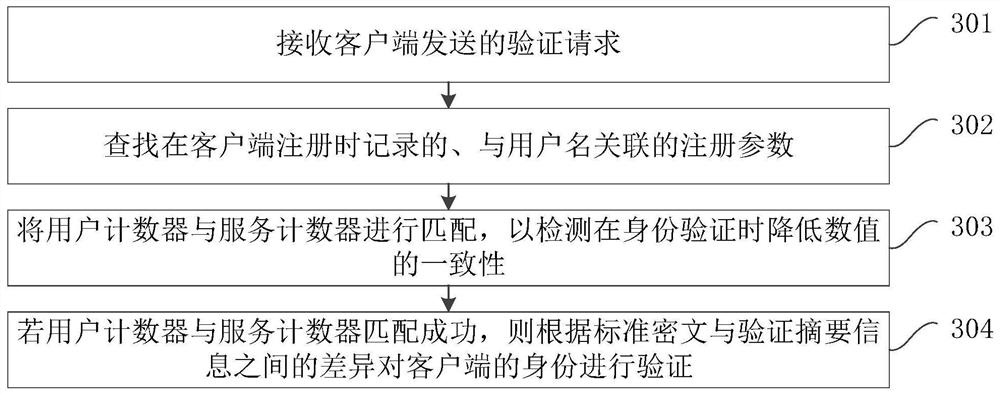
[0115] Figure 5 It is a flow chart of an identity verification method provided by Embodiment 3 of the present invention. This embodiment is based on the foregoing embodiments, and further increases the operation of verification response. The method specifically includes the following steps:
[0116] Step 501, receiving a verification request sent by a client.
[0117] Wherein, the verification request includes a user name, verification summary information Dc, and a user counter, and the verification summary information Dc is summary information generated by using the user counter as the number of times for calculating the summary and the password.
[0118] Step 502, look up the registration parameters associated with the user name recorded when the client registers.
[0119] Wherein, the registration parameters include service counter N and standard ciphertext D.
[0120] Step 503: Match the user counter with the service counter to detect the consistency of reducing the val...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com