System and method for safety protection of industrial control equipment based on active immune mechanism
An industrial control and security protection technology, applied in general control systems, control/regulation systems, computer control, etc., can solve problems such as product lack of supervision mechanism, loss and disaster, and achieve the effect of defending against unknown attacks and avoiding damage to important resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0087] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
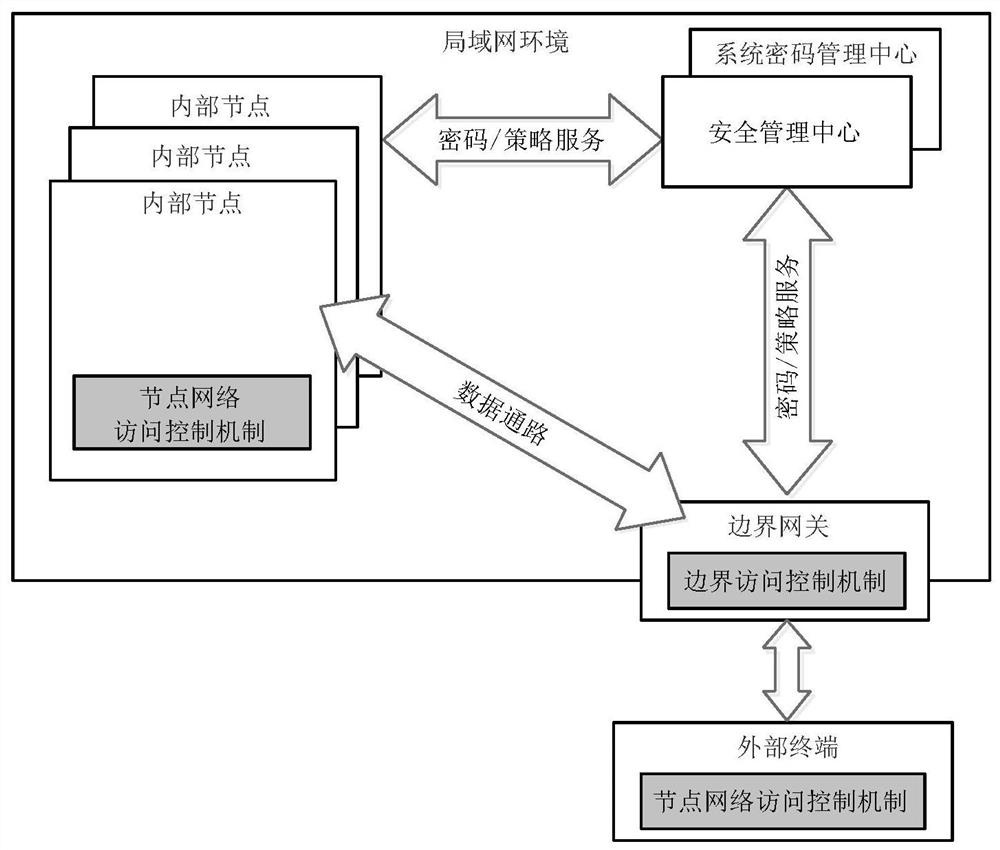
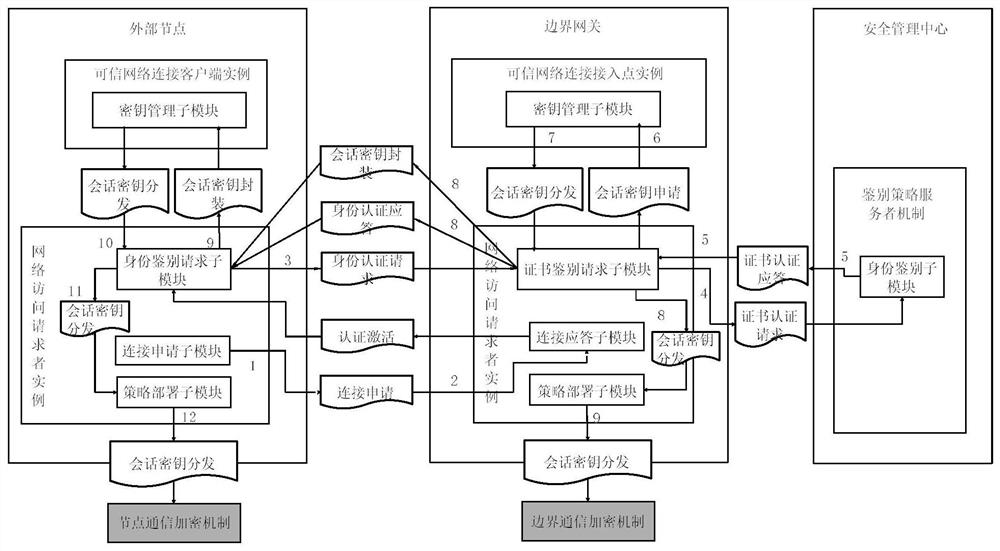
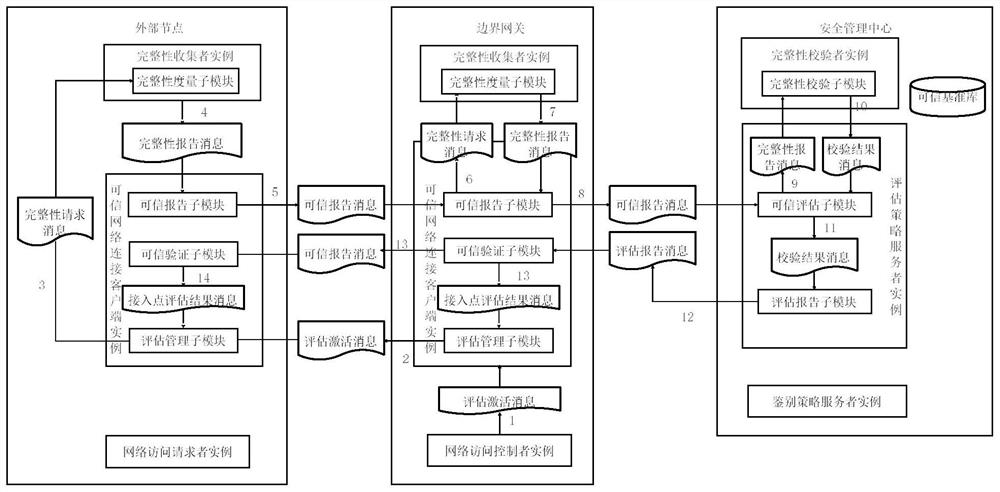
[0088] Such as figure 1 As shown, the present invention relates to a security protection framework and method for industrial control equipment based on an active immune mechanism. The specific method is to realize the security and credibility of node computing environment, regional boundaries, and communication network connections based on trusted computing technology. A credible protection system with a high level of security that is immune to the idea of security protection. Through the establishment of a safe and trusted management center, the control, decision-making and management of the trusted computing environment, trusted area boundaries and trusted communication networks can be realized, and known and unknown viruses or attack means can be blocked and isolated, thus ensuring the industrial control system. and network business func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com