Terminal WIFI login authentication method and system based on IPK
An authentication method and terminal technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as obstacles to the promotion of WARI, achieve effective protection, guarantee the core interests of enterprises, and achieve the effect of resource sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
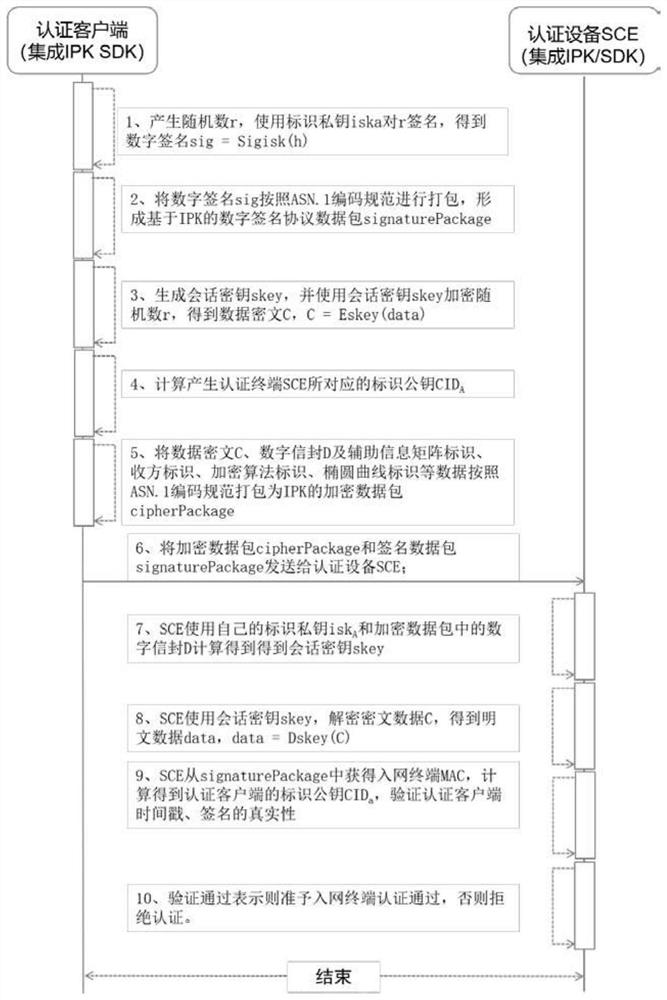
[0138] The IPK identification public key algorithm is a key system in which a public-private key pair is generated from the identification.
[0139] The session key skey is calculated and generated by an elliptic curve algorithm.
[0140] It is obtained by taking the x-coordinate of the elliptic curve point R and modulo the elliptic curve parameter n, and its calculation formula is as follows:
[0141] skey = R.x mod n,
[0142] R=r·G=(x,y),
[0143] Among them: G is a base point of the elliptic curve, and its order is a prime number; r is an encrypted random number; n is the order of the base point G; (x, y) is the coordinate of the curve point R.
[0144] A specific embodiment in which the present invention obtains ciphertext data:
[0145] Use the session key skey to encrypt the random number r to obtain the ciphertext data C,
[0146] Its calculation formula is:
[0147] C=E skey (r),
[0148] Where: E is a symmetric encryption algorithm.
[0149] A specific embodi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com