Accompanying lure generation method and device based on deep learning and data clustering
A technology of data clustering and deep learning, applied in the field of deep learning, can solve problems such as cumbersome bait generation methods, irrelevant business systems, and unequal deployment locations, and achieve the effects of high accuracy, high similarity, and improved capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Such as figure 1 , figure 2 As shown, the accompanying decoy generation method based on deep learning and data clustering is characterized in that the method performs the following steps:
[0035] Step 1: Obtain user data, use a pre-established data classification model to classify user data, and add labels to each category of user data after classification;
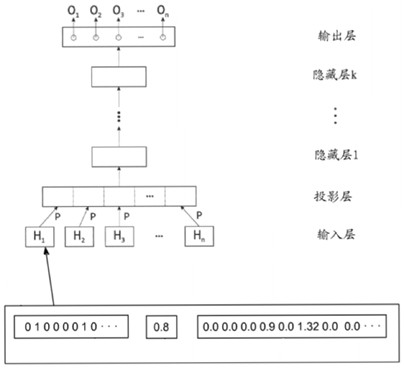
[0036] Step 2: Establish a confrontational network generation model, and build an adapted cyclic neural network based on the model structure of the confrontational network generation model; the confrontational network generation model is a data conversion model, which converts conventional data into bait data; the cyclic neural network The network is trained based on the existing conventional data and decoy data. At the same time, the conventional data input in the adversarial network generation model and the decoy data converted by the adversarial network generation model are used as input. After the output is ...
Embodiment 2
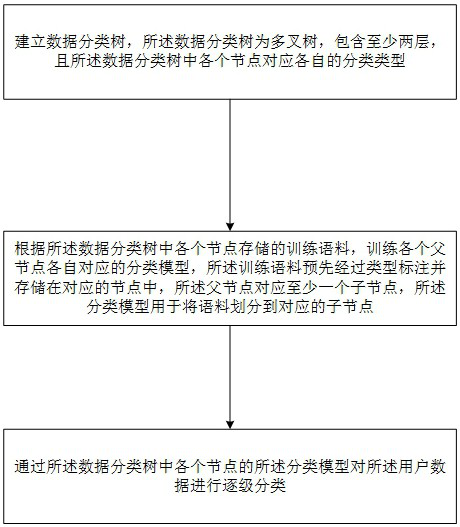
[0040] On the basis of the previous embodiment, the user data obtained in step 1 includes at least: user behavior data, application usage data, network environment data, login credential data, file data, and traffic data; The established data classification model classifies user data including the following steps: establishing a data classification tree, the data classification tree is a multi-fork tree, including at least two layers, and each node in the data classification tree corresponds to its respective classification type; The training corpus stored in each node in the data classification tree trains the classification model corresponding to each parent node, the training corpus is pre-labeled by type and stored in the corresponding node, and the parent node corresponds to at least one child node, so The classification model is used to divide the corpus into corresponding sub-nodes; the user data is classified step by step through the classification model of each node in...
Embodiment 3
[0045] On the basis of the previous embodiment, the generation model of the confrontation network in the step 2 is a data conversion model, and the conversion of conventional data into decoy data includes the following steps: use the principal component analysis method to perform feature screening on the conventional data, and obtain the intermediate data; performing cluster analysis and supervised learning on the intermediate data to obtain multiple subsets, wherein each subset includes multiple instances; extracting association rules for malicious attack commands in each subset; extracting the extracted The association rules are stored as attack features in the feature label set.
[0046] Specifically, the goal of cluster analysis is to collect data to classify on the basis of similarity. Clustering has roots in many fields, including mathematics, computer science, statistics, biology, and economics. In different application fields, many clustering techniques have been deve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com