A method for controlling and secure communication of an Internet of Things terminal
An IoT terminal and secure communication technology, applied in the field of IoT smart terminal access and management, can solve problems such as illegal device intrusion, and achieve the effect of solving security problems, solving illegal device intrusion, and facilitating access authentication and authority management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
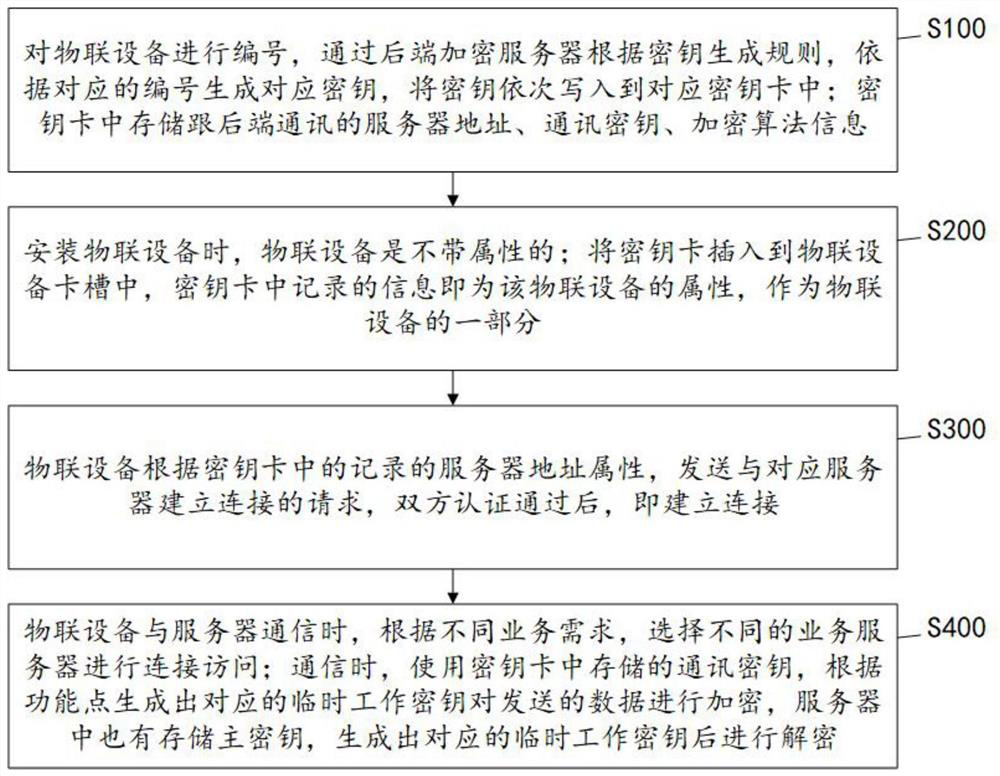
[0032] The present invention provides a terminal control and secure communication method of the Internet of Things, such as Figure 1-5 As shown, the steps include:
[0033] S100: Number the IoT devices, generate the corresponding key according to the corresponding number through the back-end encryption server according to the key generation rules, and write the key into the corresponding key card in turn; Communication server address, communication key, encryption algorithm information;
[0034] During specific implementation, the key generation rules in S100;
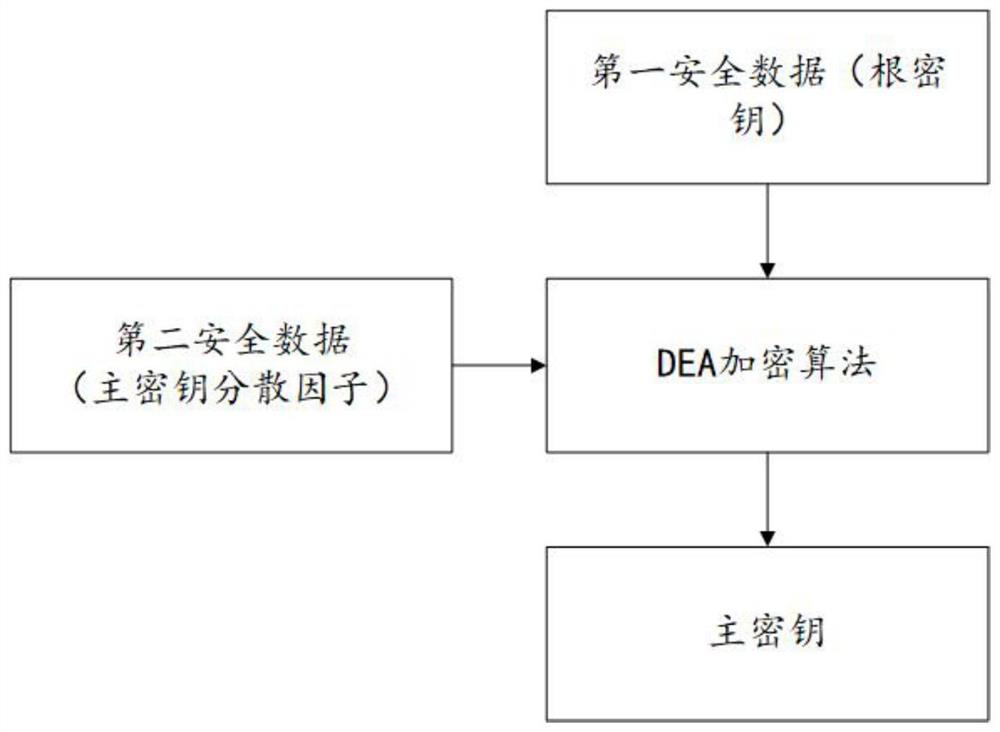
[0035] The master key generation rule is to input the first security data, which is the root key, and input the second security data, which is the master key dispersion factor, and generate the master key through the DEA encryption algorithm;
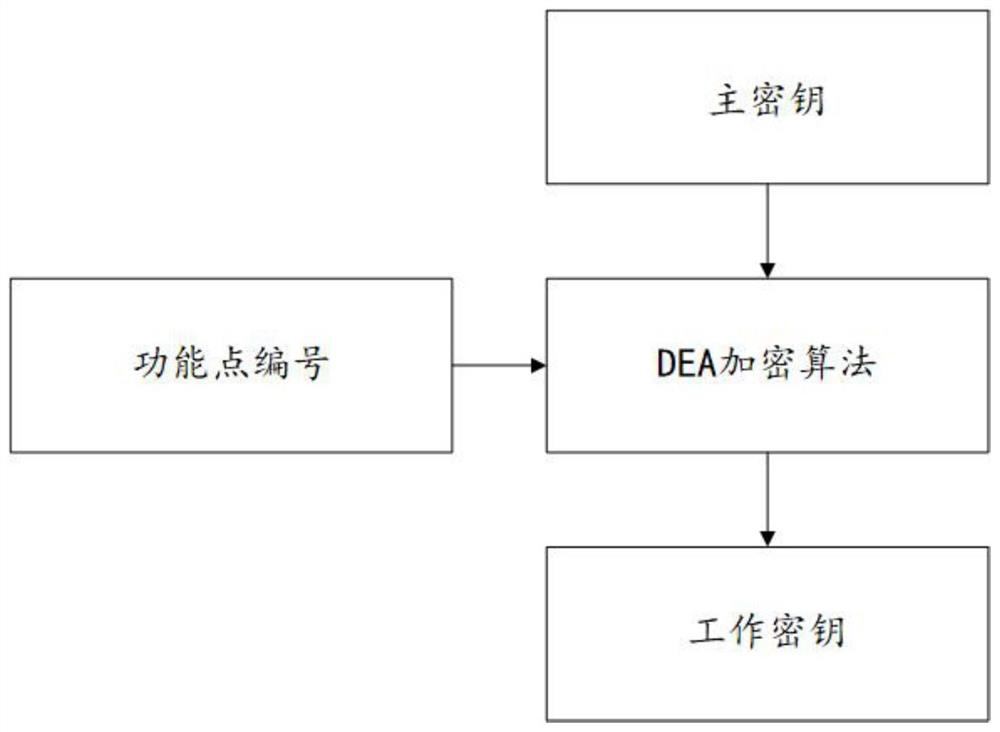
[0036] The working key generation rule is to input the master key, input the function point number, and generate the working key through the DEA encryption algorithm.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com