Data security monitoring system
A monitoring system and data security technology, applied in the field of network security, can solve problems such as restrictions on accessible IP addresses and user names, and achieve the effects of avoiding adverse effects, ensuring running speed, and avoiding occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described below in conjunction with specific inventions.
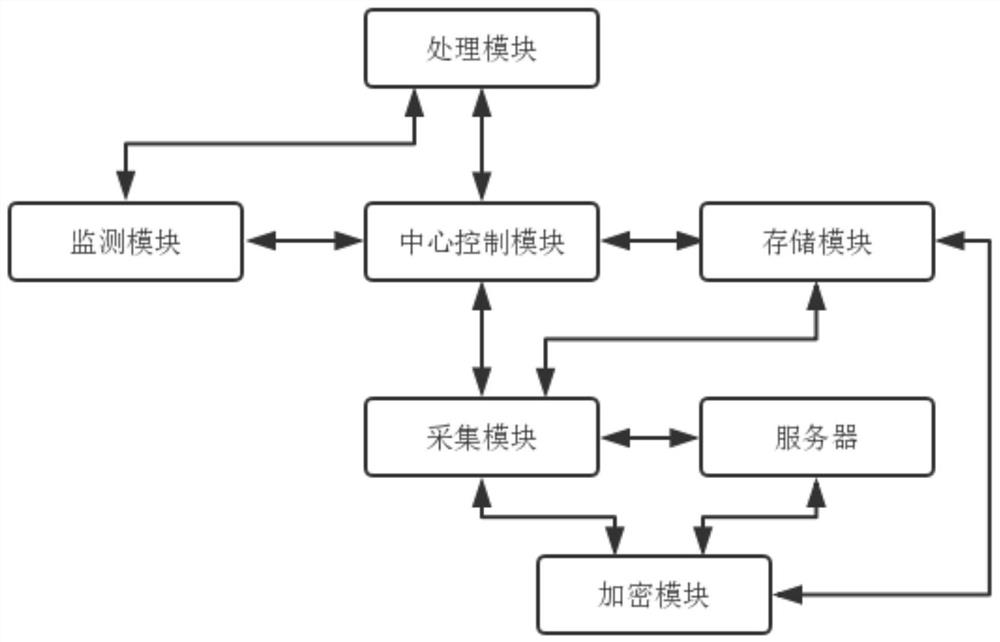
[0052] Such as figure 1 As shown, the data security monitoring system of the present application includes an acquisition module, a storage module, a monitoring module, a processing module, an encryption module and a central control module.
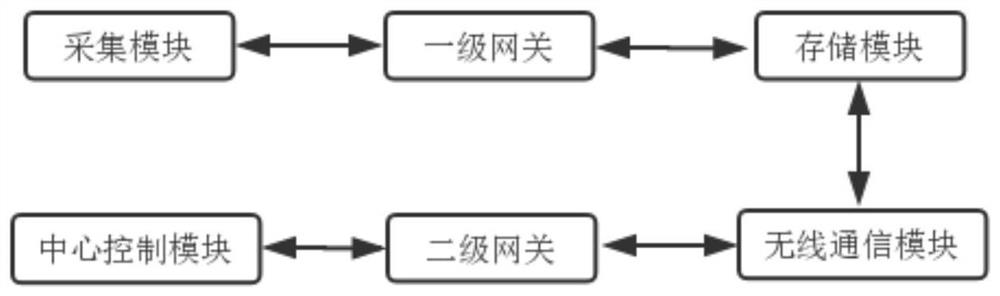
[0053] Such as figure 2 As shown, the acquisition module is used to collect the basic data from the server; the data acquisition module includes: a channel selection unit, which is used to divide the input analog signal into two channels of signals. The first and second conditioning circuits connected to the output terminals of the unit, the output terminals of the first and second conditioning circuits are connected to the input terminals of the AD unit. The connection relationship between the acquisition module and other modules is as follows: the acquisition module is connected to the storage module through a first-level gateway, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com