Identity verification system and method based on voiceprint recognition
A voiceprint recognition and voiceprint technology, which is applied in the field of identity verification system based on voiceprint recognition, can solve the problem of time-consuming identity verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
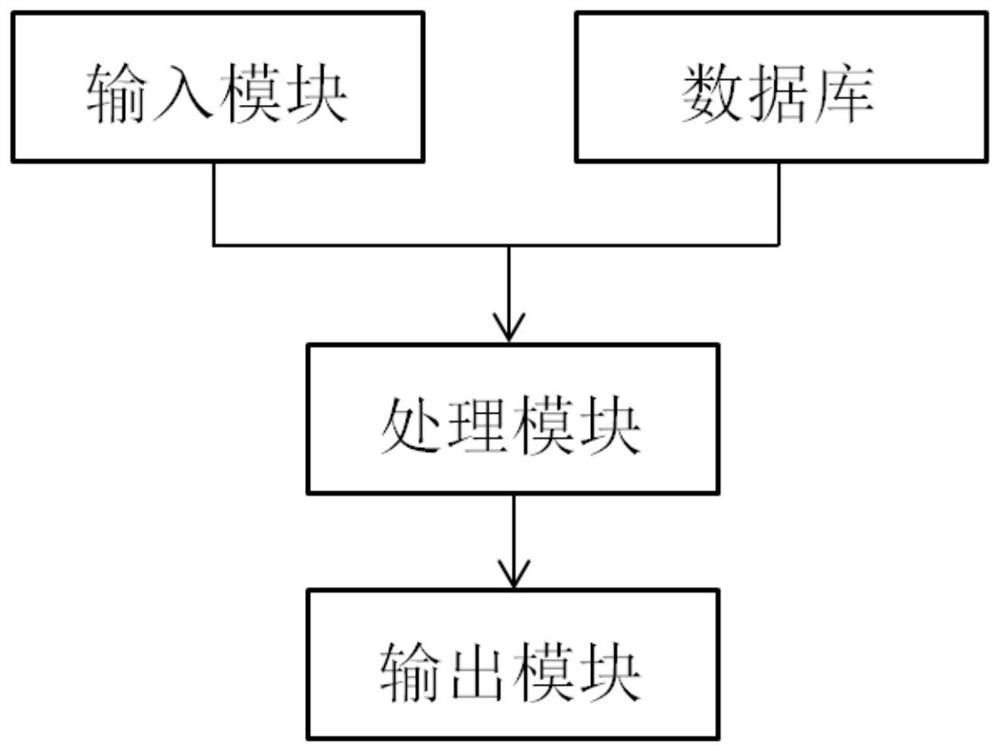
[0032] The identity verification system based on voiceprint recognition includes a client, a server and a background terminal. The client is a Huawei P40 mobile phone used by the customer, the server is a Dell EMC PowerEdge T30 mini-tower server, and the background terminal is a Lenovo all-in-one computer; figure 1As shown, the server includes an input module, a database, a processing module and an output module, wherein: the input module is used to obtain the current voiceprint model sent by the client during the call; the database is used to pre-store the sample voiceprint model of the customer; The module is used to receive the current voiceprint model, and process the current voiceprint model according to the sample voiceprint model, if the current voiceprint model does not match the sample voiceprint model, then generate the first warning message; otherwise, generate verification passing prompt information The output module is used to send the first warning message and the...
Embodiment 2
[0043] Compared with Embodiment 1, the only difference is that the database is also used to store the voiceprint models of blacklisted users; the processing module is used to judge the current voiceprint model according to the blacklist voiceprint model, if the current voiceprint model is consistent with the blacklist If the voiceprint models are the same, the second alarm information is generated. Specifically, since customer B is judged to maliciously use the identity of another person to apply for credit business, the voiceprint model of customer B is stored in the database as a blacklist; it is convenient for subsequent identification and matching directly through the voiceprint model, and the obtained The second warning message is "This user is a blacklisted user, suspected of being a fraudulent customer, please be careful!", and the auditor will conduct further identity verification and verification.
Embodiment 3
[0045] Compared with Embodiment 1, the only difference is that the input module is also used to obtain the short message data of the user terminal; the preprocessing module is also used to screen the short message data in the user terminal and extract the keyword information in the short message data , extract the short message data in which the keyword contains finance or credit, and generate the target to be verified; the processing module is also used to perform semantic analysis on the target to be verified, and when the result of the semantic analysis is a positive result, it is recorded as a positive point; otherwise , it is recorded as negative one point; the output module is also used to receive the standard score pre-stored in the database, count the score according to the semantic analysis result, and obtain the score information; if the score information is less than the first preset threshold, mark the user as high risk users, and send user information to the user t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com