Method for verifying legal terminal information extension sequence
A technology of information expansion and verification method, which is applied to electrical components, transmission systems, etc., can solve the problems of poor anti-replay attack capability and low authentication efficiency, and achieve the effects of improving survivability, improving resolution accuracy, and reducing correlation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
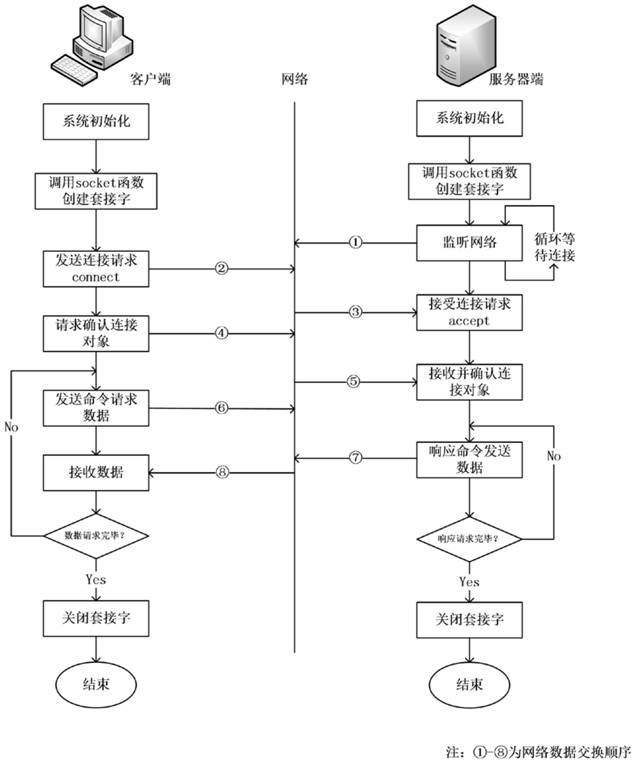
[0017] In order to make the purpose, technology and advantages of the present invention clearer, the present invention will be further described in detail and completely below in conjunction with the accompanying drawings.
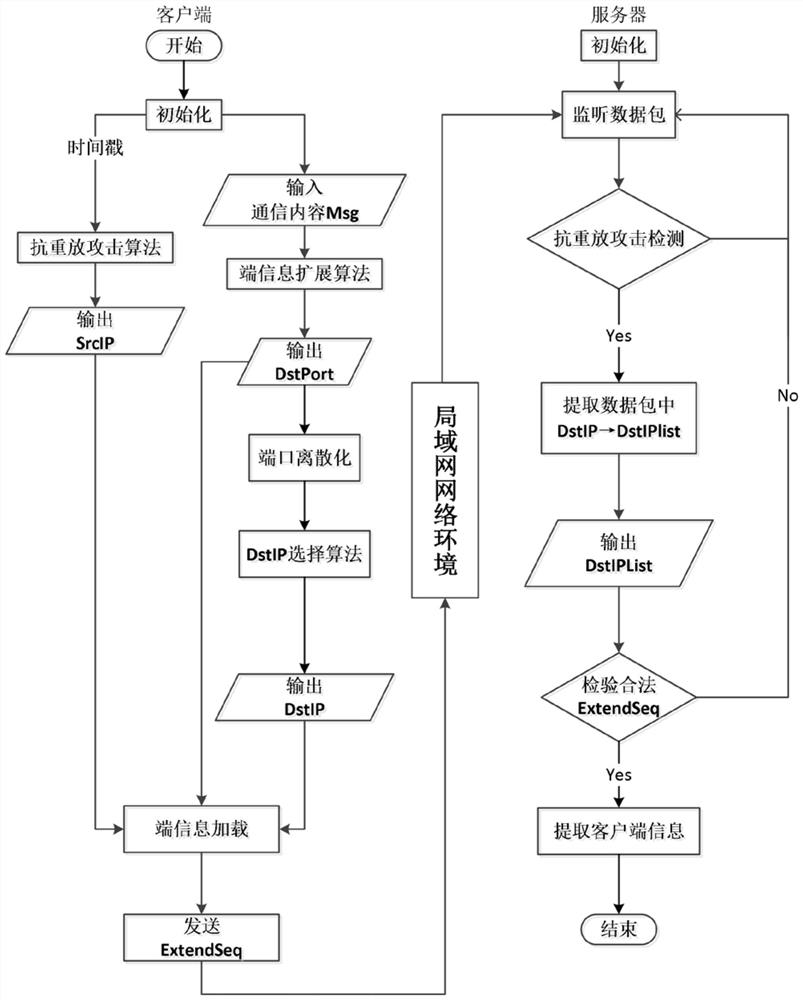
[0018] Step (1): The client adopts the anti-replay attack algorithm, and uses the timestamp to generate the terminal information SrcIP.
[0019] In the step (1), using the time stamp to generate the terminal information SrcIP, it is necessary to select a pseudo-random number seed according to the time stamp, so that the generated SrcIP is both time-sensitive and dynamic.
[0020] Step (2): Use the communication content Msg or legal identity authentication information IDMsg to generate the terminal information DstPort through the terminal information expansion algorithm, then perform port discretization on DstPort and determine the other terminal information DstIP through the DstIP selection algorithm.
[0021] In the step (2), the DstPort is discretized an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com