A method for preventing attacks based on virtual network devices forging ip addresses
A virtual network device and IP address technology, which is applied in the field of anti-attack based on virtual network device forged IP address, can solve the problems of no response strategy, inability to obtain relevant information, lack of passive response to sudden attacks, etc., and achieve the goal of passive response Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
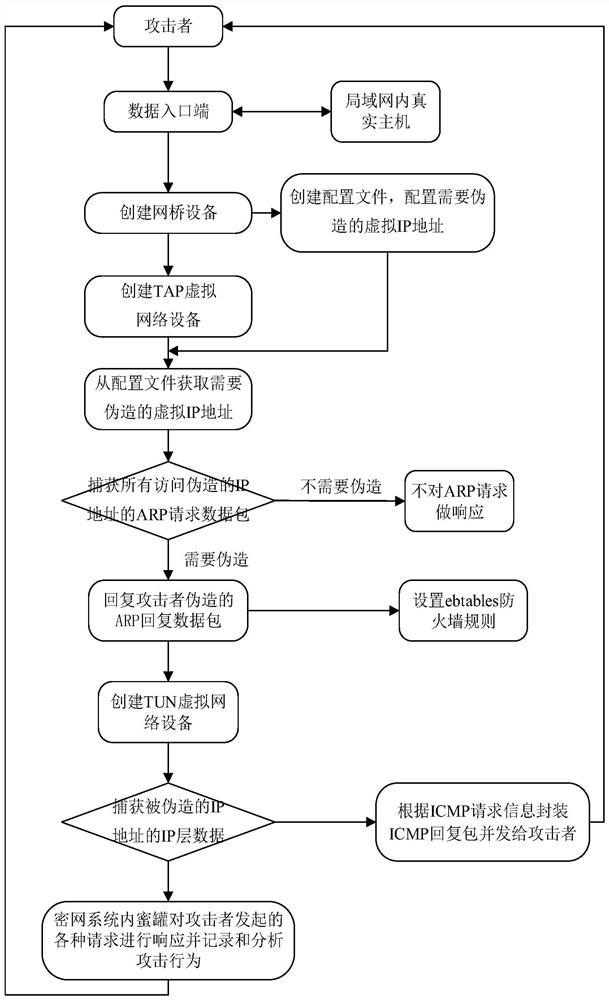
[0072] In the communication of IPv4 address, the communication parties need to obtain the physical address (MAC address) of the other party's network through the ARP protocol first, and the subsequent IP data exchange can only be carried out after completing the data link layer communication.
[0073] The present invention creates a TAP virtual network device by using TUN / TAP (virtual network device). Protocol) request data packets to respond, forge the data link layer communication of IP data packets, after completing the data link layer data interaction, forward and perform other secondary processing on the subsequent interactive network data, and record and analyze the attack traffic Analysis, sensing threats, is not simply avoiding attacks. Under normal circumstances, only when the IP address is actually configured on the hardware network card can a reply be made to the relevant ARP request. The present invention captures all data link layer data packets through the TAP vi...
Embodiment 2
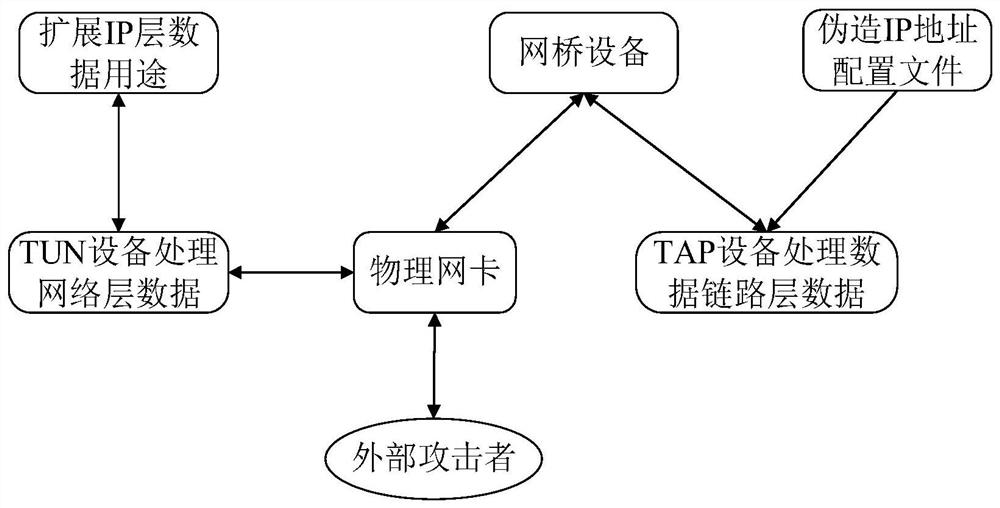
[0102] as attached figure 2 As shown, after the TAP network device is connected to the bridge, it first reads the virtual IP address that needs to be forged from the configuration file configured with the virtual IP address that needs to be forged. When the attacker accesses the virtual IP address that needs to be forged in the above configuration file through the network For the IP address, it is similar to configuring the IP address on the physical network card of the host, and then the TAP network device captures all ARP request data for the forged IP address at the data link layer, when the ARP request data for the forged IP address is captured , the TAP network device will forge ARP reply data and send it to the requester; configure system policy routing in the created TUN virtual network device, and capture the network layer data of the above-mentioned IP address that needs to be forged by the attacker at the network layer. For ICMP data, directly Encapsulate the ICMP r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com