Malicious software homology analysis method based on behavior tree
A homology analysis and malware technology, applied in the field of behavior tree-based malware homology analysis, which can solve problems such as malware classification errors, damage to the ability to distinguish, and affect the performance of malware analysis.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
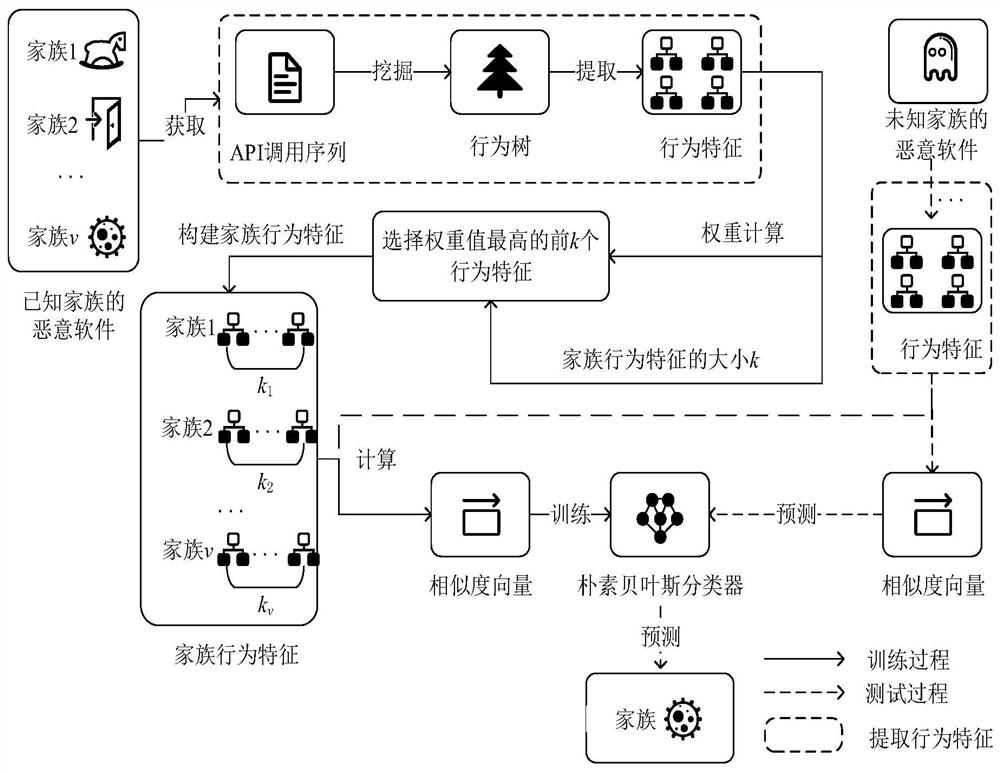
[0065] This embodiment discloses a behavior tree-based malware homology analysis method, the basic process is as follows figure 1 shown, including the following steps:
[0066] T1. Collect the API call sequence generated when the malware is executed;
[0067] T2. Convert API call sequences into API logs to mine malware behavior models;
[0068] T3. Based on the behavior tree, extract the behavioral characteristics of malware;
[0069] T4. Build behavioral characteristics of malware families;
[0070] T5, calculating the similarity vector of malware;
[0071] T6, the collected data is divided into a training set and a test set according to the ratio of 8:2;
[0072] T7. Building a classification model W on the training set based on the naive Bayesian classification algorithm;
[0073] T8. Use the classification model W to complete the family classification of malware.
[0074] In this embodiment, a behavior tree with anti-noise property is used to express and draw the beh...
Embodiment 2
[0081] The characteristics and performance of the present invention will be further described in detail below in conjunction with Embodiment 2.
[0082] A preferred embodiment of the present invention includes the following steps:
[0083] T1. Collect the API call sequence generated when the malware is executed;
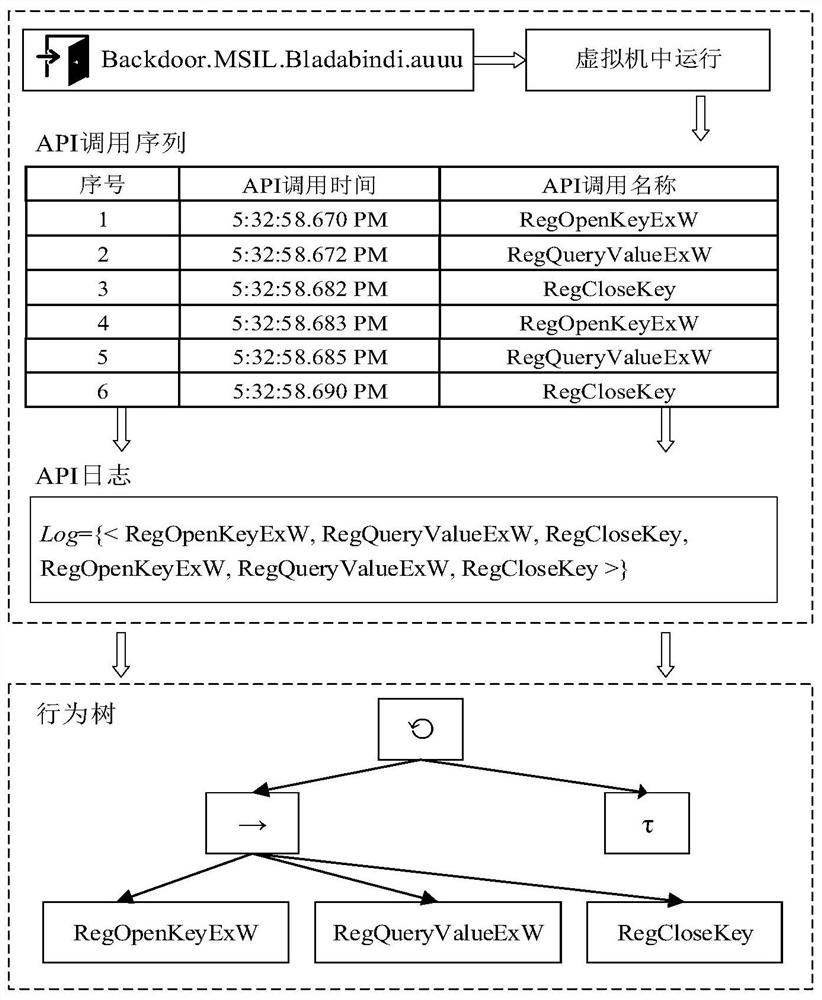
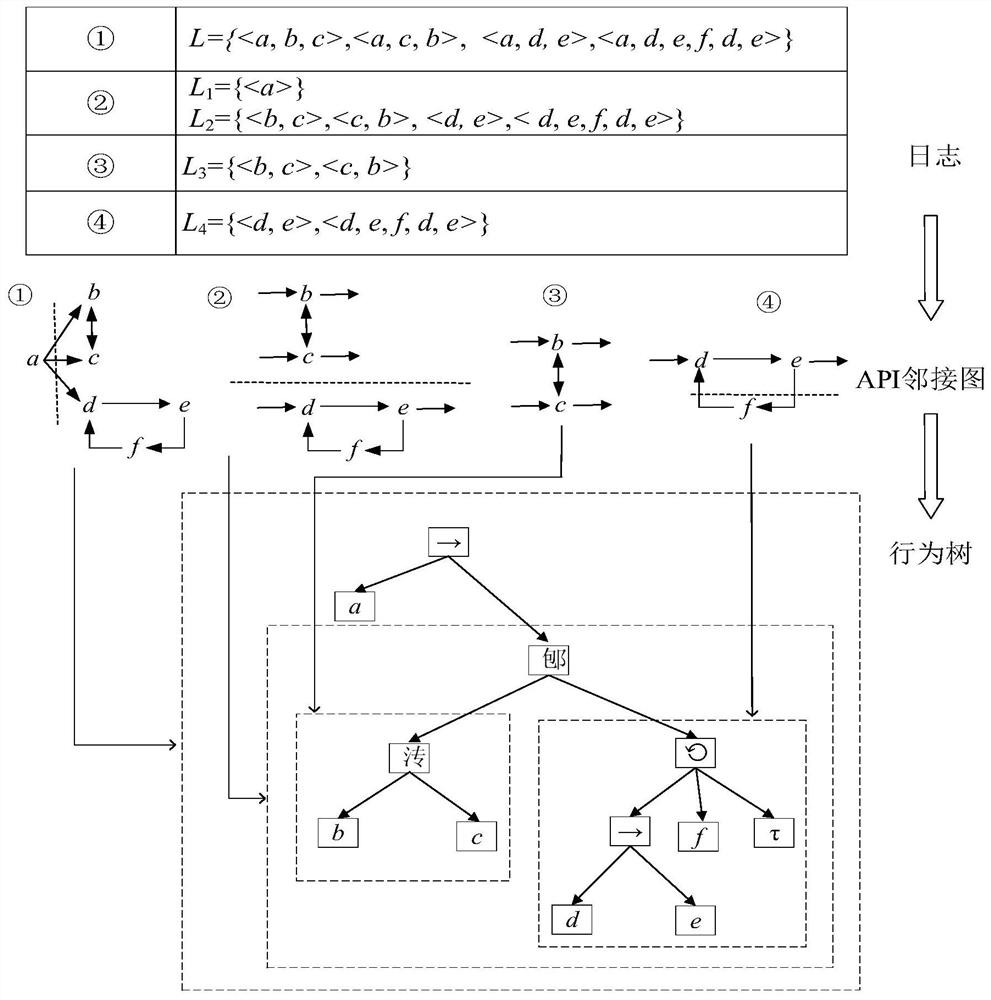
[0084]T2. Convert the API call sequence into API logs, and mine the behavior tree of malware;
[0085] T2.1. Convert API call sequence into API log;
[0086] Among them, the API call sequence is a collection of APIs generated by the malware during each run, defined as S=1 ,a 2 ,...,a n >, where a r , 1≤r≤n represents the rth API call, which is a binary group a r ={time,label}, time indicates the time when the API is called, label is the name of the API call, n indicates that the API call sequence S consists of n tuples, and in the API call sequence S, the APIs are sorted in ascending order of call time ;
[0087] Wherein, the API log is a set composed of one o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com