Refined enhanced permission control and analysis system of Android platform
An Android platform and Android system technology, which is applied in the Android permission management and analysis system, refines and enhances the field of permission management and analysis system, and can solve the problems of lack of guarantee, less and professional analysis of permissions, and high error rate of results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0085] The technical solution of the refined and enhanced rights control and analysis system for the Android platform provided by the present invention will be further described below in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention and implement it.
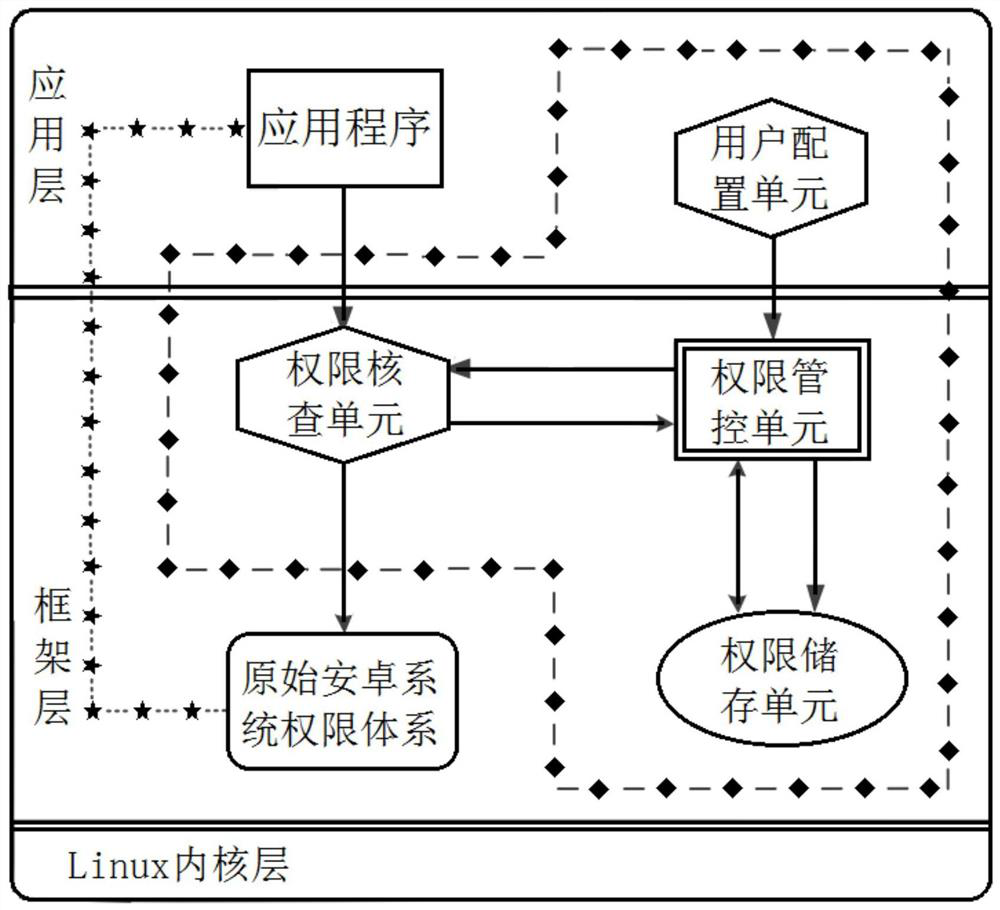
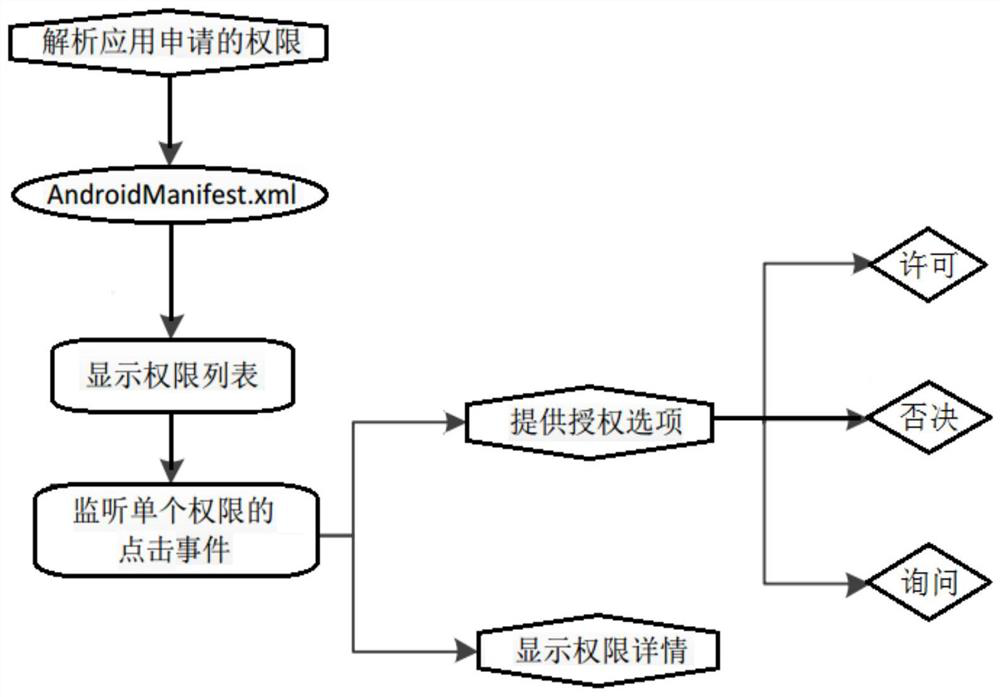
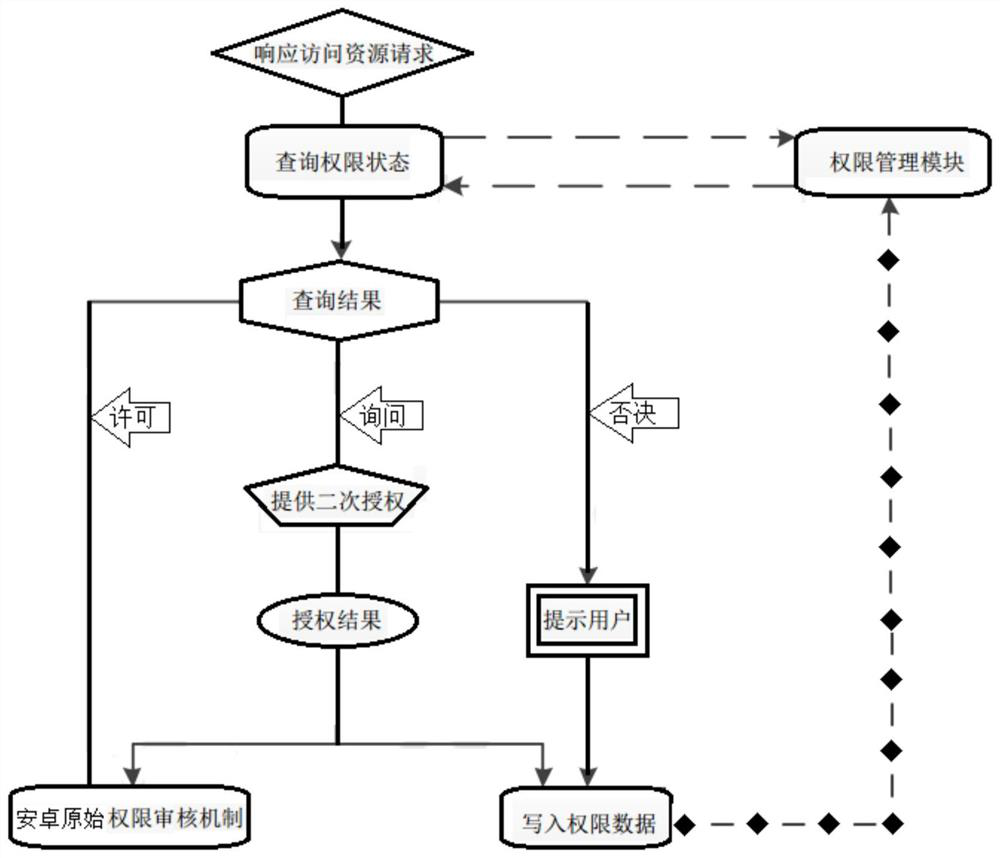
[0086] The refined and enhanced authority control and analysis system for the Android platform provided by the present invention proposes an authority management and control method that integrates refined and enhanced authorization, real-time intelligent deployment, authority combination analysis, calculation of security risk values, and authority threat defense, mainly including refinement Enhanced authorization management and control system and combined authority security detection and analysis system are two major aspects; in the refined and enhanced authorization management and control system, it includes user configuration unit, authority control u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com