A secure image retrieval method based on secret sharing in cloud environment
A technology of secret sharing and cloud environment, applied in the field of multimedia information security protection, to achieve the effect of protecting index security, overcoming precision loss, and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
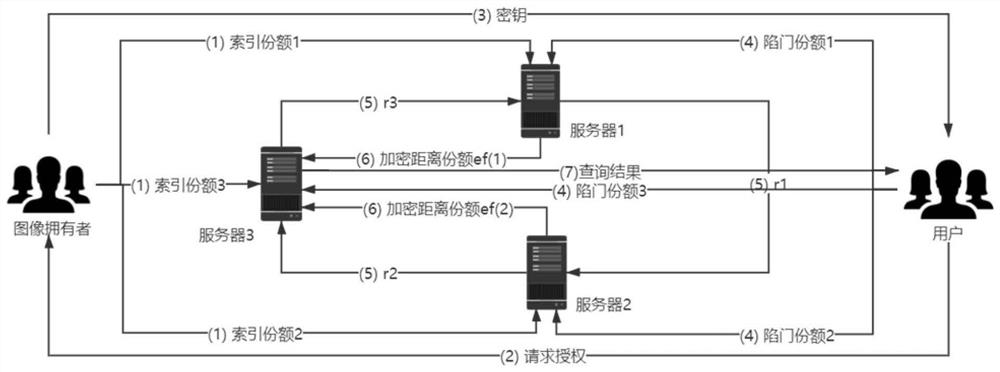
[0060] Such as figure 1 As shown, an image security retrieval method based on secret sharing in a cloud environment provided by the embodiment of the present invention, the specific implementation steps are:
[0061] Step 1, the image owner extracts image features, generates index shares, and uploads the index shares and encrypted images to the cloud:
[0062] Step 1.1, index construction: for all images of the image owner, extract color features to generate an index, where the yth image feature is expressed as n represents the dimension of the feature point descriptor;
[0063] Step 1.2, build index share: generate a string of random numbers a=(a 1 ,...,a n ), for image h y Generate index shares. For m=1,2,..,n:
[0064]
[0065]
[0066]
[0067] index share h y (1) Send to server 1, index share h y (2) Send to server 2, index share h y (3) send to server 3;
[0068] Step 1.3, use the AES encryption algorithm and key K to encrypt the yth original image I ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com