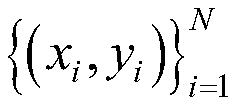Network real-time intrusion detection method based on fast gradient boosting tree model
A gradient boosting tree and intrusion detection technology, applied in the field of network security, can solve the problems of difficult to meet real-time requirements, difficult to deal with network intrusion, high false alarm rate, etc., achieve good time efficiency, improve detection performance, and reduce false positives. The effect of reporting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
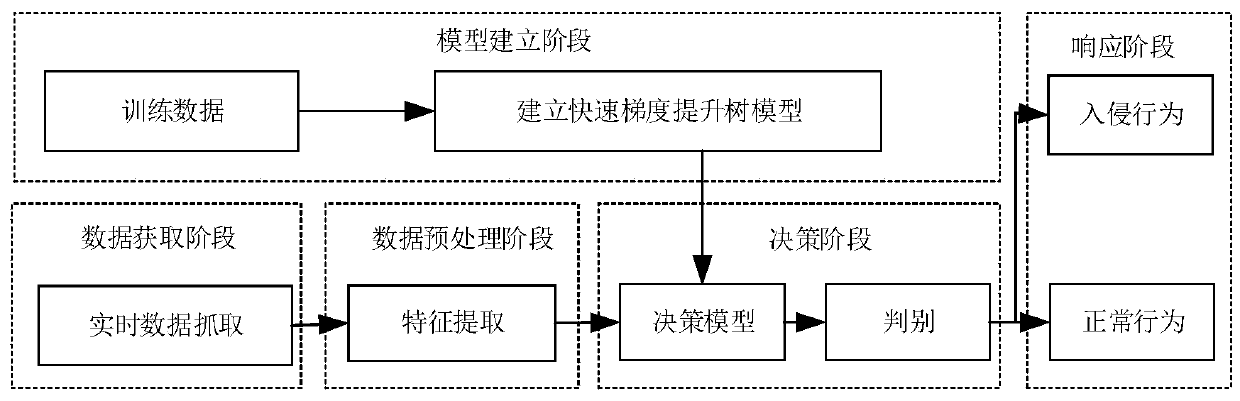
[0043] Such as figure 1 As shown, the present embodiment provides a real-time network intrusion detection method based on a fast gradient boosting tree model, comprising the following steps:
[0044] S1. In the model building stage, use the training data to train the fast gradient boosting tree classification model;
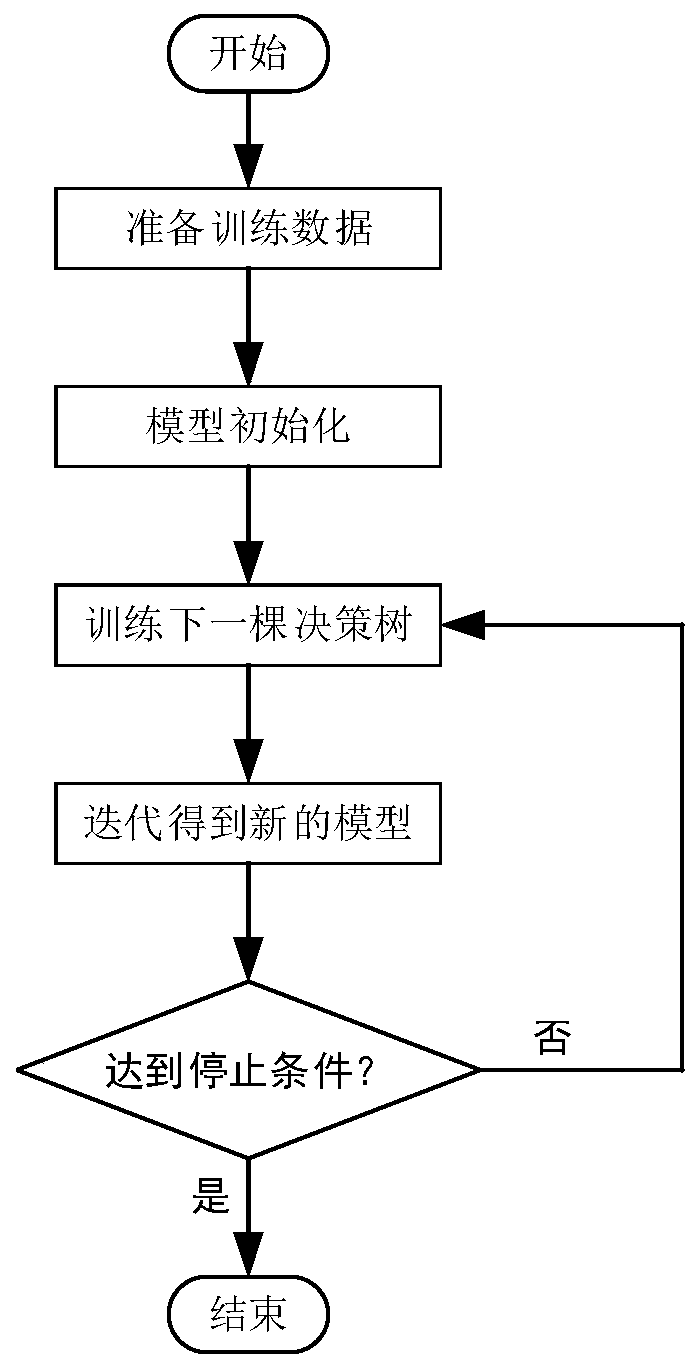
[0045] Such as figure 2 As shown, the specific steps to establish a classification model based on fast gradient boosting trees include:
[0046] The original data is sampled by GOSS (Gradient-based One-Side Sampling) to reduce the amount of data, and at the same time, the mutually exclusive sparse features are bound by EFB (Exclusive Feature Bundling) to reduce the feature dimension, and the obtained data is used as training data;
[0047] The training data set comes from the network environment deployed by the intrusion detection system, expressed as a feature vector set:
[0048]
[0049] Among them, N represents the number of feature vectors, x i is th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com