Network user group security management technology based on proprietary algorithm
A technology for network user and security management, applied in the fields of management, industrial Internet network security, and network security, it can solve problems such as loss of firewall meaning, performance degradation, and complicated configuration, so as to achieve no impact on network communication efficiency, overcome inefficiency, and network environment. clean effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to describe the technical content of the present invention more clearly, further description will be made below in conjunction with specific implementation cases.
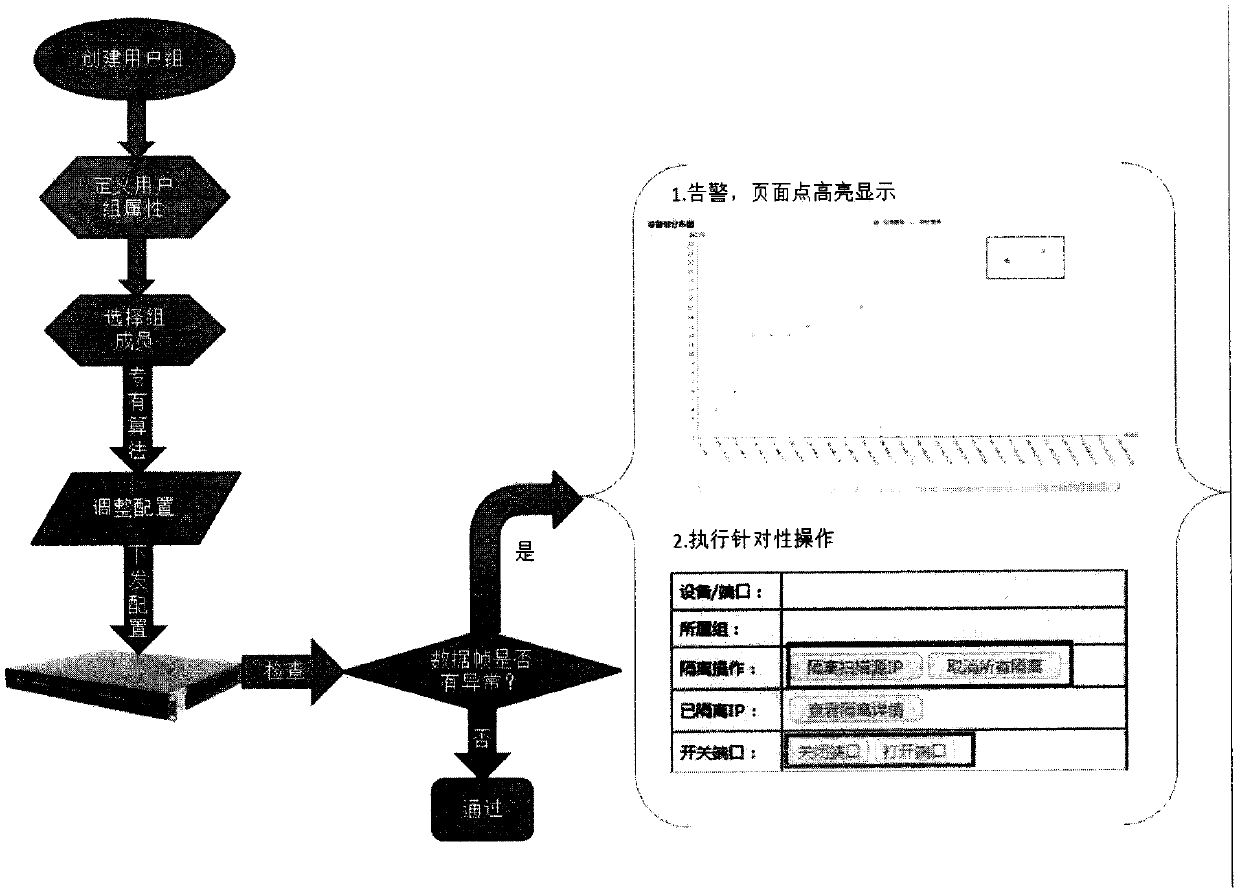
[0021] Such as figure 1 , figure 2 As shown, the network user group security management technology based on the proprietary algorithm of the present invention achieves the purpose of maintaining network security by realizing multiple isolations of the network. The firewall can only isolate the boundary between the internal network and the external network. Illegal communication and malicious attacks in the internal network cannot be monitored and stopped on the network. Moreover, personal firewalls or anti-virus software only check themselves, and cannot do anything about the malicious spread of viruses, worms, etc. in the intranet.
[0022] Such as image 3 As shown, the network user group safety management technology realized based on proprietary algorithm of the present invention reduces the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com