Authorization verification method and device and storage medium
A verification method and authorized technology, applied in the direction of protocol authorization, instruments, payment systems, etc., can solve the problems of authorization invalidation, insufficient disclosure of authorization information, and heavy certificate management burden, so as to avoid unreliability and reduce the risk of authorization flooding. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
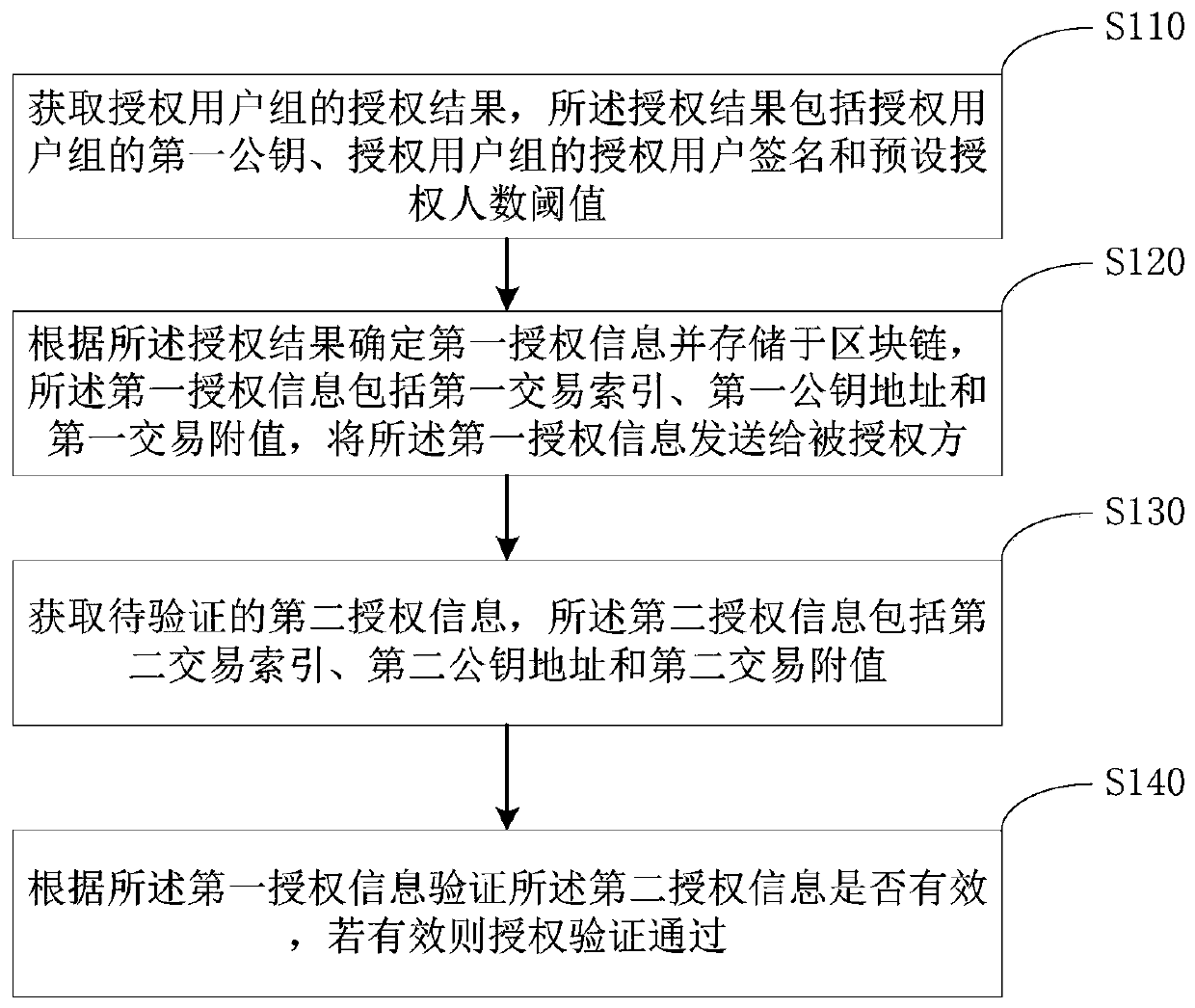
[0028] see figure 1 , this embodiment provides an authorization verification method, specifically, the method includes the following steps:
[0029] S110. Obtain an authorization result of the authorized user group, where the authorization result includes the first public key of the authorized user group, the signature of the authorized user of the authorized user group, and a preset authorized number threshold.
[0030] The authorized user group is a set composed of all authorized users. Each user in the authorized user group has a pair of public key and private key. There is no restriction on the user form here, which can be an individual or an organization. This embodiment does not limit the specific generation algorithm of the public-private key pair. For example, algorithms such as RSA and ECDSA can be used to generate a public-private key pair. The set composed of the public keys of all users in the user group is called the first public key. In this embodiment, the spec...
Embodiment 2
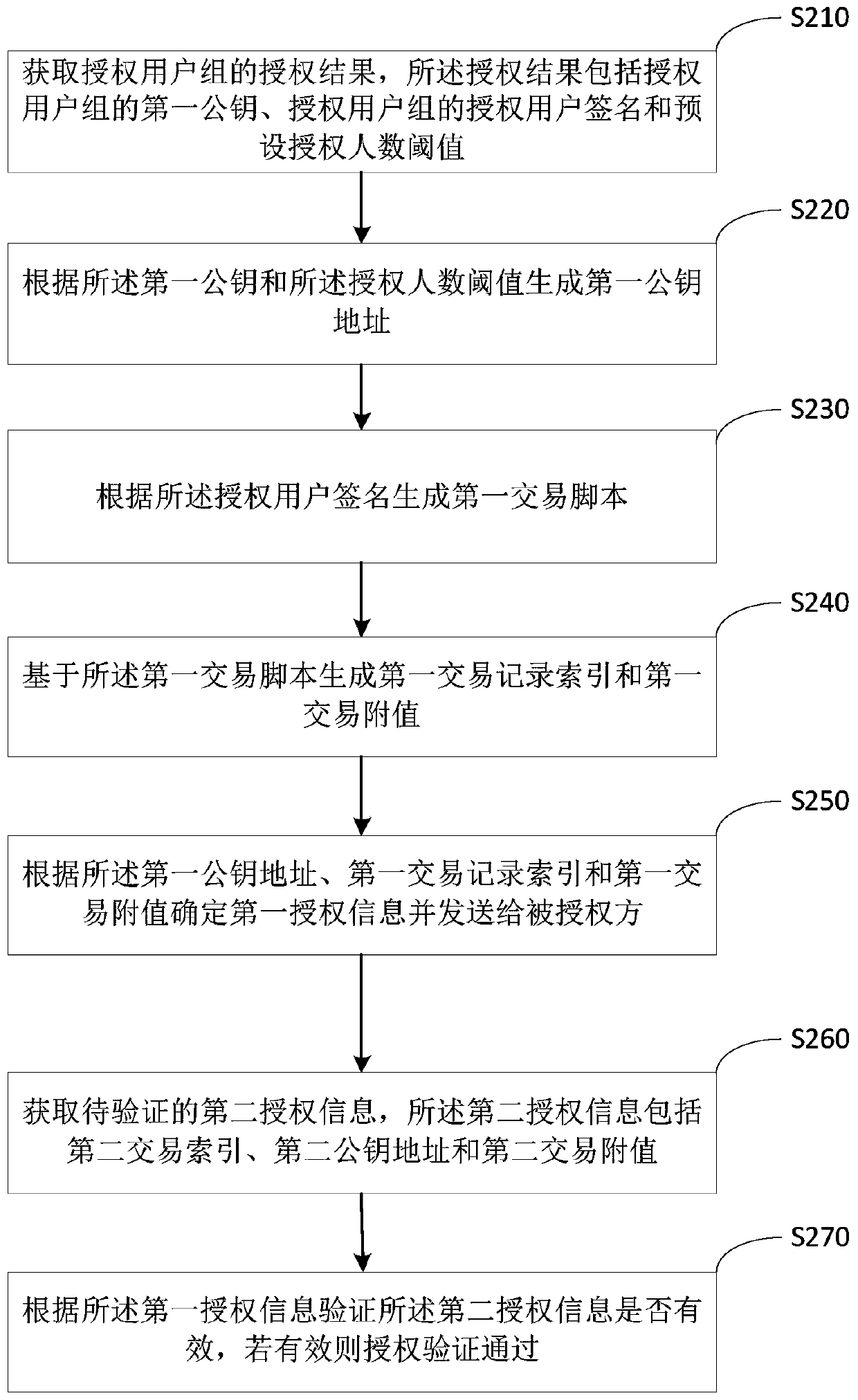
[0048] This embodiment further explains and exemplifies some processes in the authorization verification method on the basis of the first embodiment, specifically as figure 2 shown, including:
[0049] S210. Obtain an authorization result of the authorized user group, where the authorization result includes the first public key of the authorized user group, the signature of the authorized user of the authorized user group, and a preset authorized number threshold.
[0050] Step S210 is identical to step S110.
[0051] S220. Generate a first public key address according to the first public key and the authorized number threshold.
[0052] Specifically including: generating a public key combination according to the first public key, generating a first public key address and a first hash value according to the preset authorized number threshold, the total number of authorized user groups and the public key combination .
[0053] This embodiment does not limit the specific way...
Embodiment 3
[0075] image 3 A schematic structural diagram of an authorization verification device provided in Embodiment 3 of the present invention, as shown in image 3 As stated, the device includes:
[0076] The first acquiring module 310 is configured to acquire an authorization result of the authorized user group, where the authorization result includes the first public key of the authorized user group, the signature of the authorized user of the authorized user group, and a preset authorized number threshold.
[0077] Authorization module 320, configured to determine first authorization information according to the authorization result and store it in the block chain, the first authorization information includes the first transaction index, the first public key address and the first transaction value, and the The first authorization information is sent to the authorized party.
[0078] Specifically, in some embodiments, the authorization module 320 includes:
[0079] A public ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com