Data sharing method and related device, equipment and system
A data sharing and data technology, applied in the field of data processing and the Internet, can solve problems such as poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
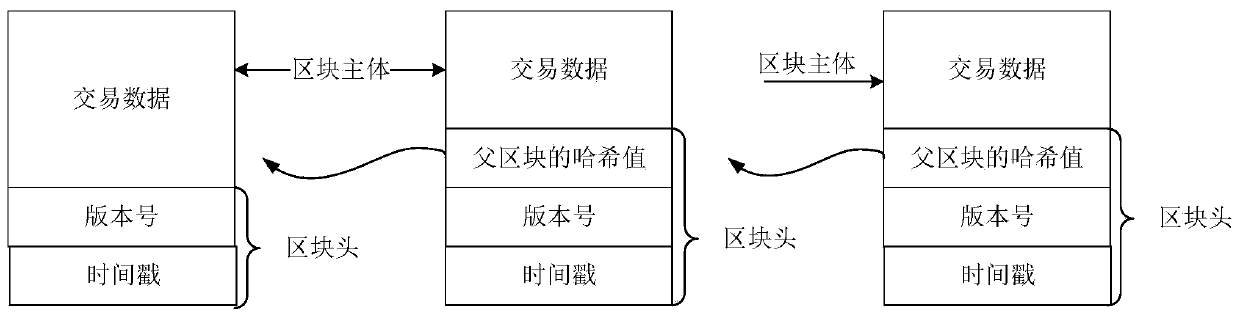
Image
Examples
Embodiment 1
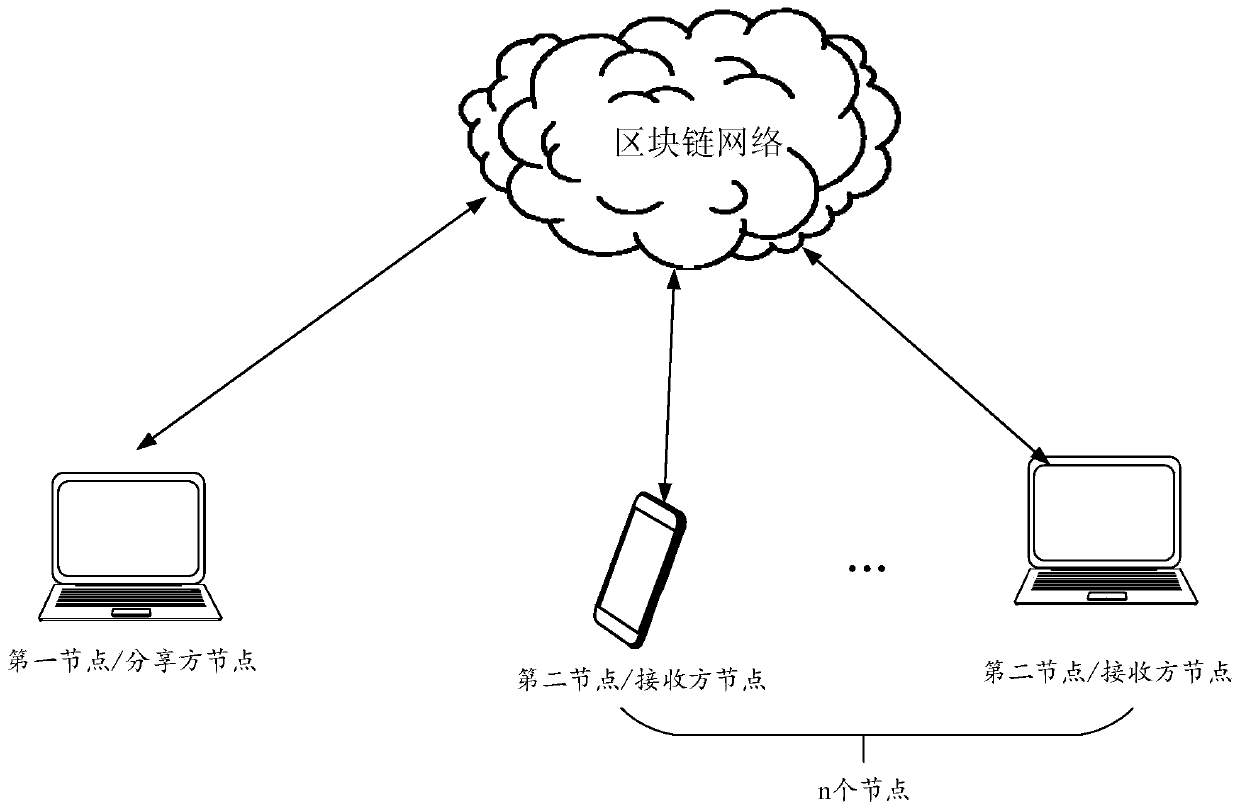
[0088] Combine below Figure 1A The shown system introduces a data sharing method provided by the embodiment of the present application. The present application takes the first node to share data with N nodes as an example, wherein the second node is one node among the n nodes. In the introduction When n nodes obtain the shared data (ie, the target data in the embodiment of the present application), the second node is taken as an example for illustration. It should be understood that the above-mentioned first node, n nodes and second nodes are all nodes in the blockchain network, such as Figure 3A As shown, this data sharing method can be implemented by Figure 1A As shown in the system implementation, specifically, the method includes some or all of the following steps:
[0089] S11: The first node receives a sharing request for the target data, and the sharing request is used to request to share the target data with n nodes in the blockchain network, where n is a positive i...
Embodiment 2
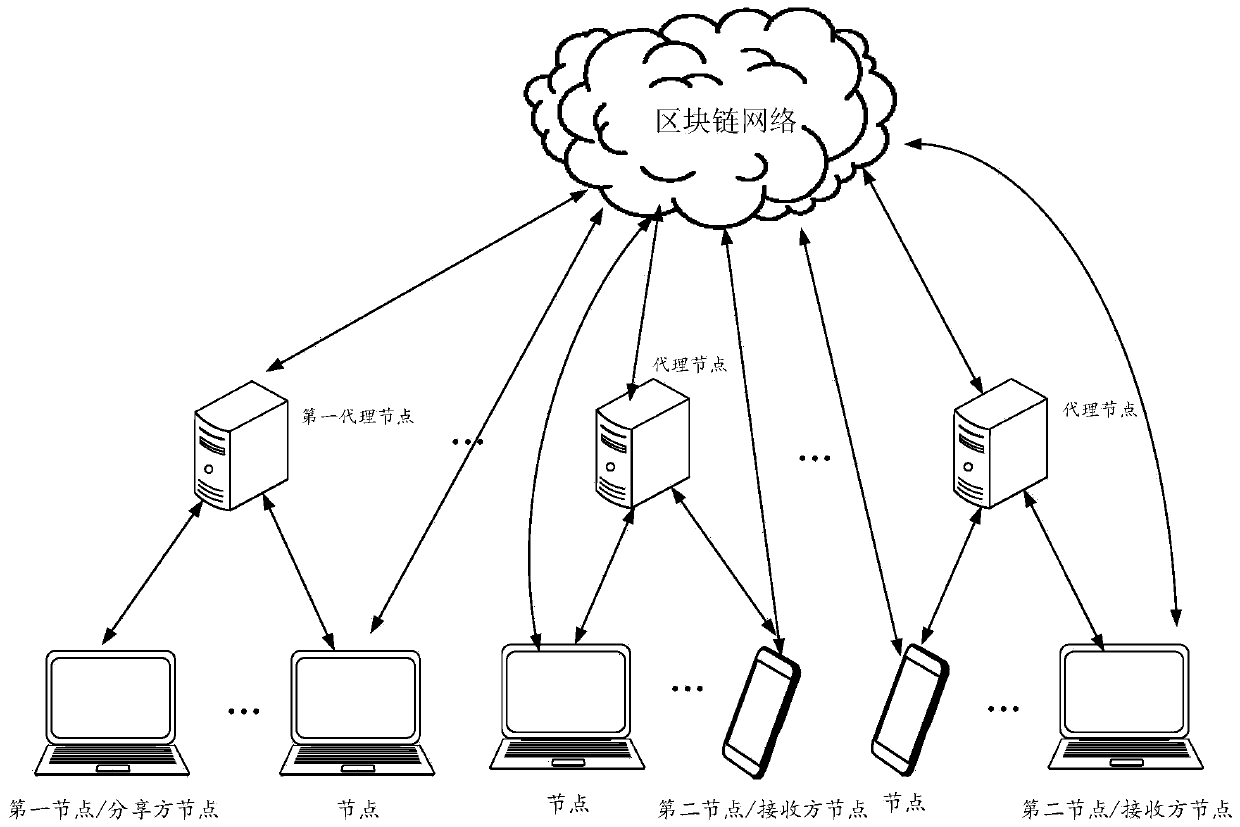
[0118] Combine below Figure 1B The system shown introduces another data sharing method provided by the embodiment of this application. In this method, ordinary nodes do not have the authority to upload data to the blockchain network, and their proxy nodes complete the upload. This application takes the first node to share data with n nodes as an example to illustrate, wherein, the second node is one of the n nodes, and n nodes are introduced to obtain the shared data (that is, in the embodiment of this application, the target data) is described by taking the second node as an example. It should be understood that the first node, the n nodes, the first proxy point, the second node, and the second proxy node are all nodes in the blockchain network, such as Figure 3B As shown, this data sharing method can be implemented by Figure 1B As shown in the system implementation, specifically, the method includes some or all of the following steps:
[0119] S21: The first node sends...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com