Communication protocol credibility verification device
A verification device and communication protocol technology, applied in the field of communication, can solve problems such as difficulty in ensuring the quality of verification results, insufficient strictness of ambiguity, and low accuracy of natural language
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
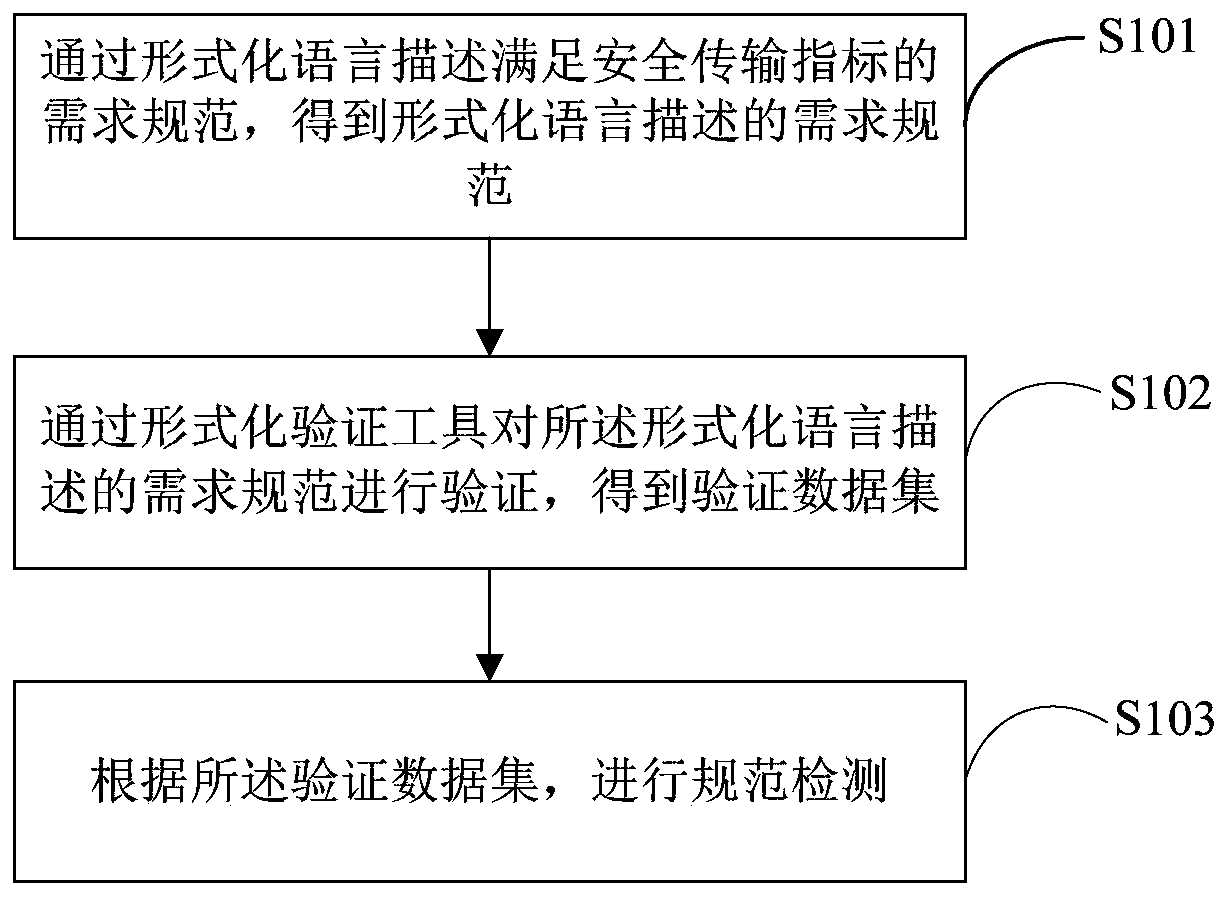
[0052] figure 1 It is a schematic flowchart of a communication protocol authenticity verification method shown according to an exemplary embodiment;
[0053] In some embodiments, a communication protocol authenticity verification method includes:
[0054] Step S101, describe the requirement specification that satisfies the security transmission index through the formal language, and obtain the requirement specification described in the formal language;
[0055] In some optional embodiments, the computing platform is no longer a simple operation of a single node. Today's computing nodes are networked and systematic. Computing platform systems form a powerful platform system through data communication. The computing platform system Reliable data communication between computers is the basis to ensure the safe operation of the entire software, and the communication between computing platform systems is restricted by the communication protocol of the platform. The communication p...
Embodiment 2
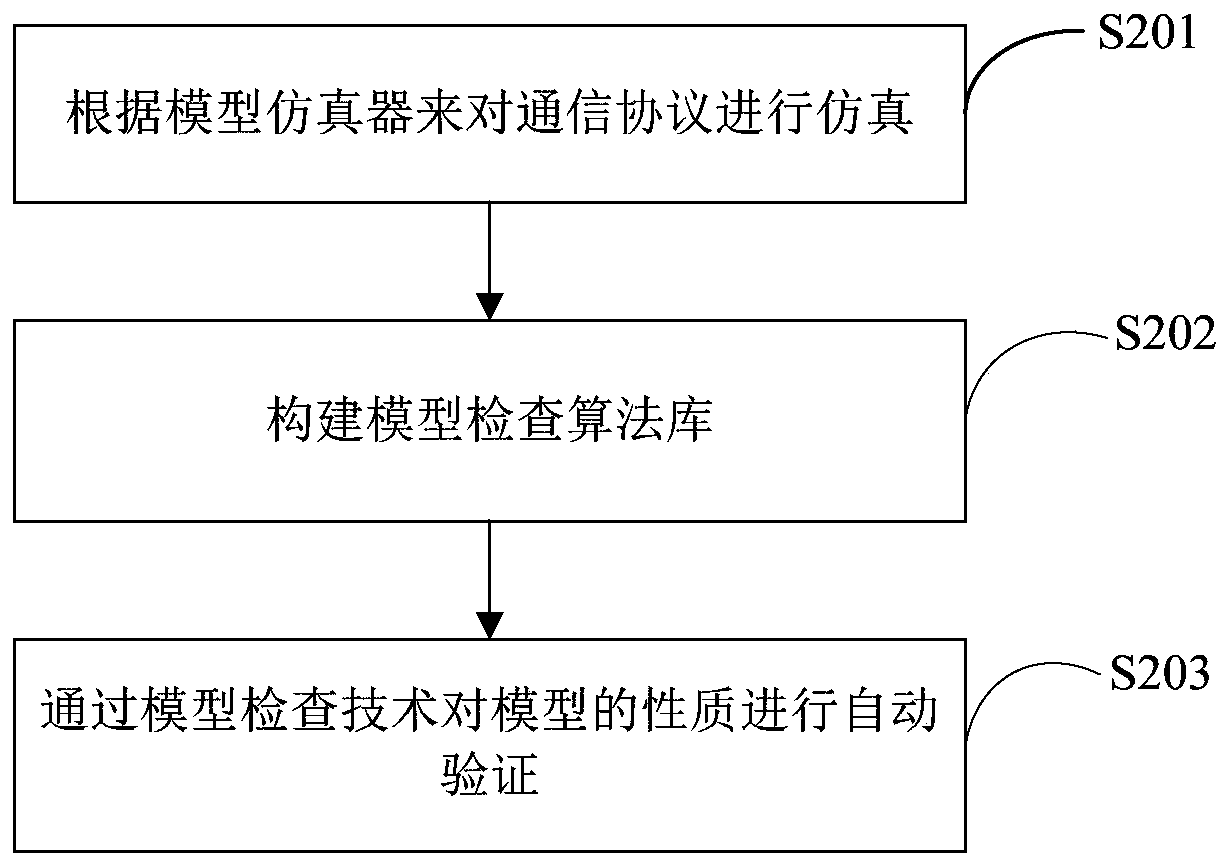
[0102] In a preferred embodiment, the trusted verification method of the communication protocol based on the computing platform system of the present invention is used to carry out trusted verification of the Powerlink protocol between computing platforms.
[0103] Open source real-time communication technology Powerlink is a real-time Ethernet protocol used to solve the real-time nature of data transmission in the field of industrial control and data acquisition on the standard Ethernet medium. This protocol mainly specifies the communication on the data link layer. The protocol supports periodic Communication and aperiodic communication, one protocol cycle mainly includes isochronous synchronous phase and asynchronous communication phase, periodic communication occurs in isochronous synchronous phase, acyclic communication occurs in asynchronous communication phase, Powerlink contains two types of communication nodes, the main Station node and slave station node, and accordin...
Embodiment 3
[0109] An embodiment of the present disclosure provides a communication protocol authenticity verification device, Figure 4 It is a schematic structural diagram of a communication protocol authenticity verification device according to an exemplary embodiment.
[0110] Such as Figure 4 As shown, a communication protocol authenticity verification device, including:
[0111] S401 The formal language description module is used to describe the requirement specifications that meet the security transmission indicators through the formal language description, and obtain the requirement specifications described in the formal language;
[0112] S402 A formal verification module, configured to verify the requirement specification described in the formal language through a formal verification tool to obtain a verification data set;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com