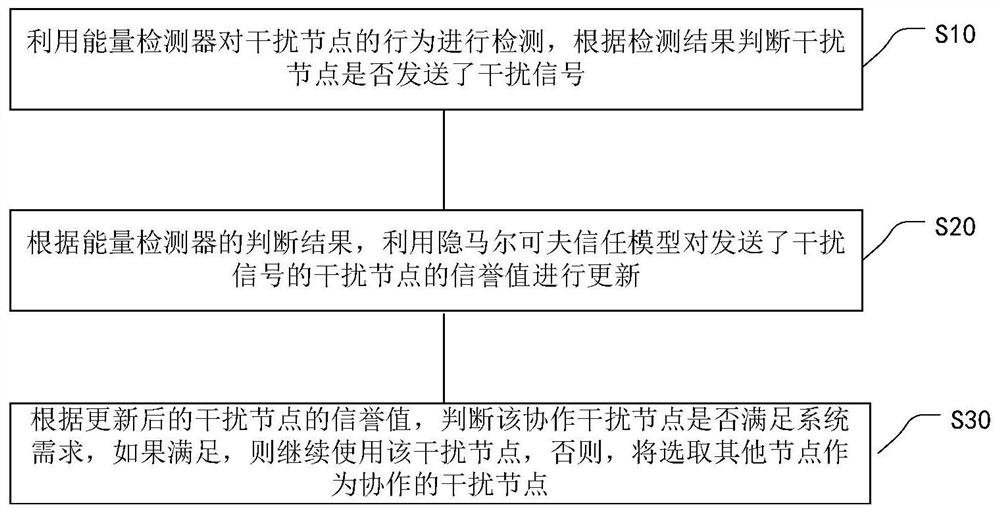
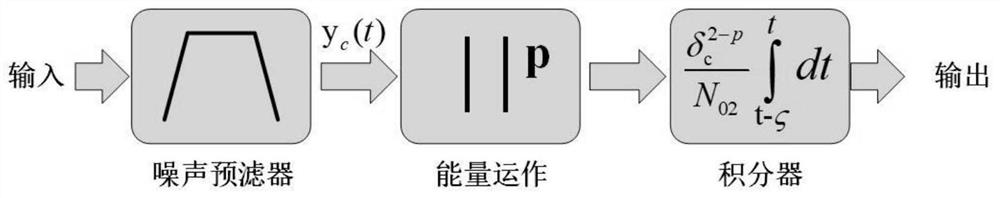
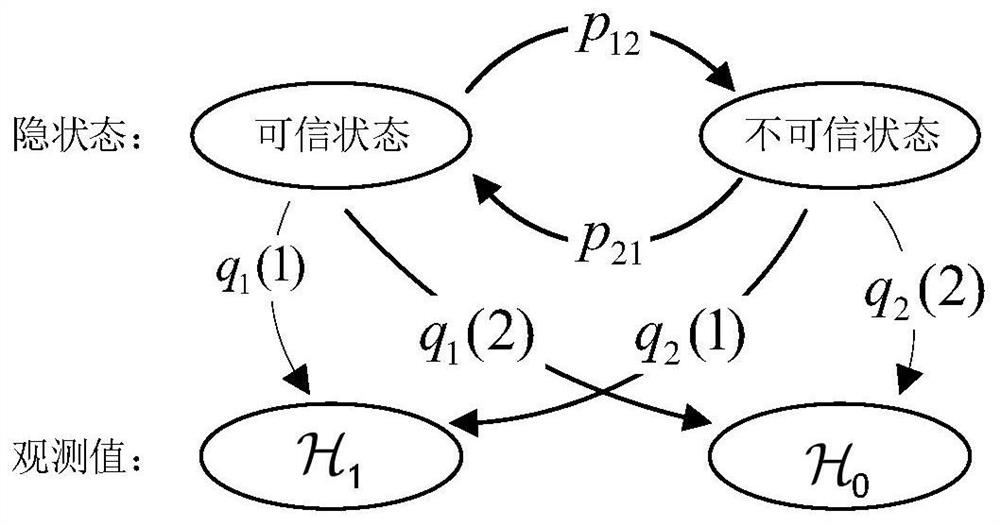
Credible Collaborative Interference Node Selection Method Based on Hidden Markov Model
A cooperative interference and node technology, applied in wireless communication, transmission monitoring, electrical components, etc., to achieve the effect of ensuring safety performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0086] Example 1 Selection Strategy of Trusted Collaborative Interference Nodes in the Internet of Things
[0087] In the embodiment of the present invention, the secure transmission in the Internet of Things system is considered. This IoT system consists of two access nodes and various types of IoT devices. In this system, access node 2 wants to send information to an IoT device (smart kettle). Meanwhile, an eavesdropper (sweeping robot) intends to intercept and decode the message. In order to protect the sent messages from being decoded by eavesdroppers, another access node 1 selects an IoT device (smart safe) as a cooperative interference node. Cooperating jamming nodes send jamming signals to eavesdroppers so that messages cannot be decoded correctly.
[0088] However, there is a challenge that needs to be addressed in cooperative jamming techniques. Traditionally, cooperative jamming techniques are considered to be based on a fundamental assumption: cooperative jammin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com