Method and device for jointly processing data by two parties
A data processing and two-party technology, applied in the field of data security, can solve problems such as leakage of user privacy, exposure of user sample feature values, exposure of data processing model model parameters, etc., to achieve a small amount of communication and calculation, and ensure safe private data Calculation, the effect of safe multiplication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
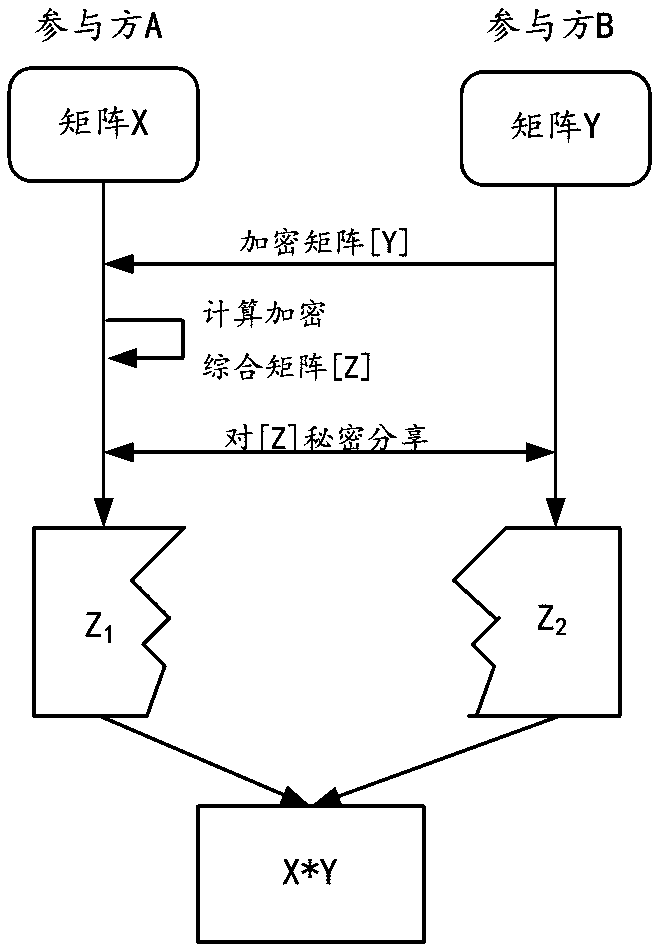
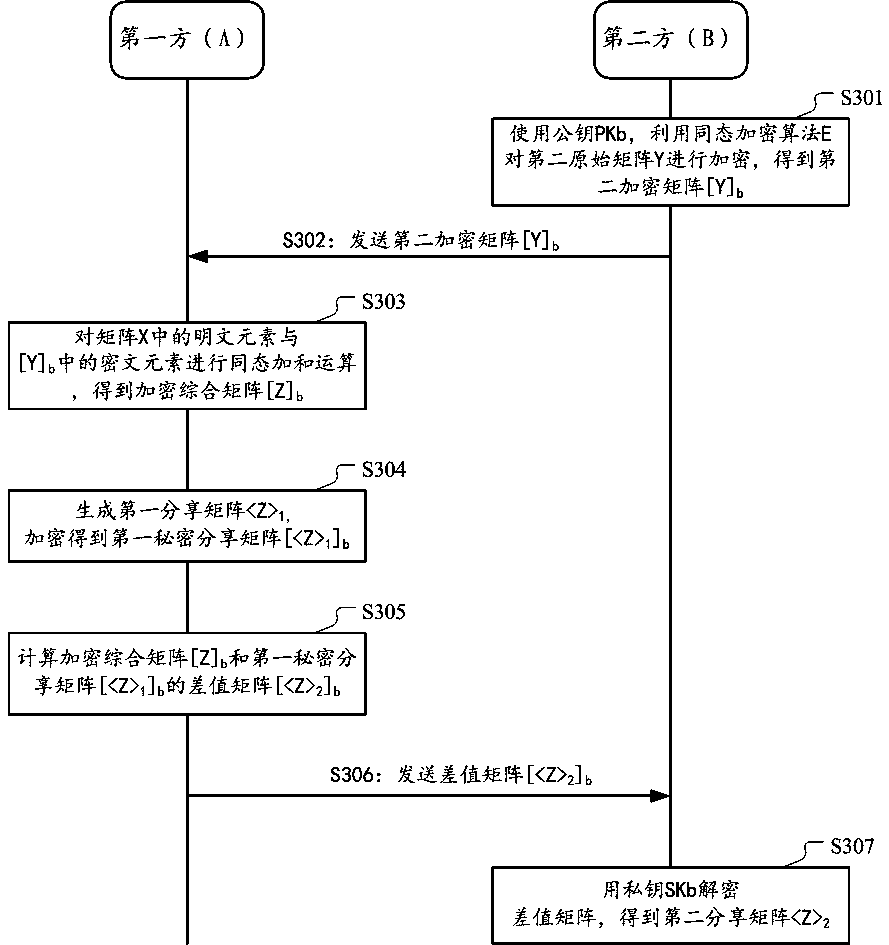
[0105] According to an implementation manner, the apparatus 400 further includes a transceiver unit (not shown), configured to: send the first sharing matrix to the second party, and / or; receive the shared matrix from the second party Describe the second sharing matrix.
[0106] According to another embodiment, the transceiving unit is configured to: send the first sharing matrix to a third party different from the first party and the second party.
[0107] According to yet another embodiment, there is provided an apparatus for jointly performing data processing by two parties, wherein the two parties include a first party and a second party, the first party has first private data recorded as a first original matrix, and the second party has The two parties have the second privacy data recorded as the second original matrix, and the dimension of the second original matrix is smaller than the first original matrix; the above-mentioned device is deployed in the second pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com