JavaScript code obfuscation method of custom obfuscation scheme
A code obfuscation and self-definition technology, which is applied in the field of JavaScript code obfuscation, can solve the problems of low confidentiality and complex JavaScript code confidentiality, etc., and achieve the effect of strong confidentiality, multiple verification steps, and strong user operability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
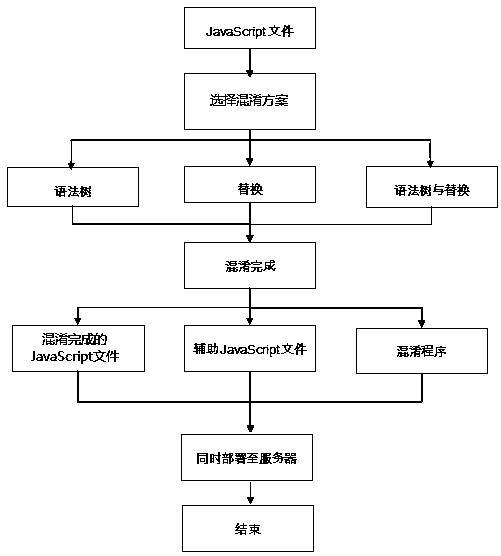
[0039] A custom obfuscation scheme, this embodiment is described based on scheme 1, such as figure 1 and figure 2 As shown, the scheme 1 is implemented based on JavaScript syntax parser, obfuscator and syntax tree parser in the following steps:
[0040] Step S1.1 removes redundant codes in the initial JavaScript code;
[0041] Step S1.2 uses the JavaScript parser to split the initial JavaScript code into independent word blocks, and generates a syntax tree whose root node is the window variable according to the split independent word blocks;
[0042] Step S1.3 passes the syntax tree generated in step S1.2 into the obfuscator; the obfuscator performs full tree traversal on the generated syntax tree, and performs node obfuscation for each tree node; after node obfuscation, then Each tree node is added redundantly;
[0043] Step S1.4 Use the grammar tree parser to extract the word blocks of the tree nodes in sequence from the grammar tree processed in step S1.3 according to t...
Embodiment 2
[0051] In order to better realize the present invention, further, the scheme 1 can be replaced by the scheme 2, and the scheme 2 specifically includes the following steps:
[0052] Step S2.1 searches for variables and function names in the initial JavaScript code, and saves them in a key-value pair object;
[0053] Step S2.2 sets an array of meaningless strings, traverses the key-value pair objects, and replaces the variables and function names stored in the key-value pair objects with meaningless strings in the meaningless string array through regular matching.
[0054] Working principle: use the corresponding meaningless string to replace variables and function names to generate obfuscated JavaScript code, and then only need to follow the corresponding relationship in advance to complete deobfuscation.
[0055] Other parts of this embodiment are the same as those of Embodiment 1 above, so details are not repeated here.
Embodiment 3
[0057] In order to better realize the present invention, further, solution 1 or 2 can also be replaced by solution 3, and the solution 3 specifically refers to: first process the initial JavaScript code in solution 1, and then perform the processing in solution 2.
[0058] Working principle: First perform syntax tree obfuscation, and then perform variable replacement obfuscation. The obfuscation will be more complicated, but you need to pay attention to the operation. When obfuscating, first perform syntax tree obfuscation, and then perform variable substitution obfuscation. It is necessary to de-obfuscate the variable replacement first, and then de-obfuscate the syntax tree.
[0059] Other parts of this embodiment are the same as those of Embodiment 1-2 above, so they will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com