Abnormal information mining method, device, system and terminal equipment
A technology of abnormal information and excavation devices, applied in the field of information processing, can solve the problems of low accuracy, risk control platform cannot add risk adjustment, rework, etc., and achieve the effect of improving prevention and control capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
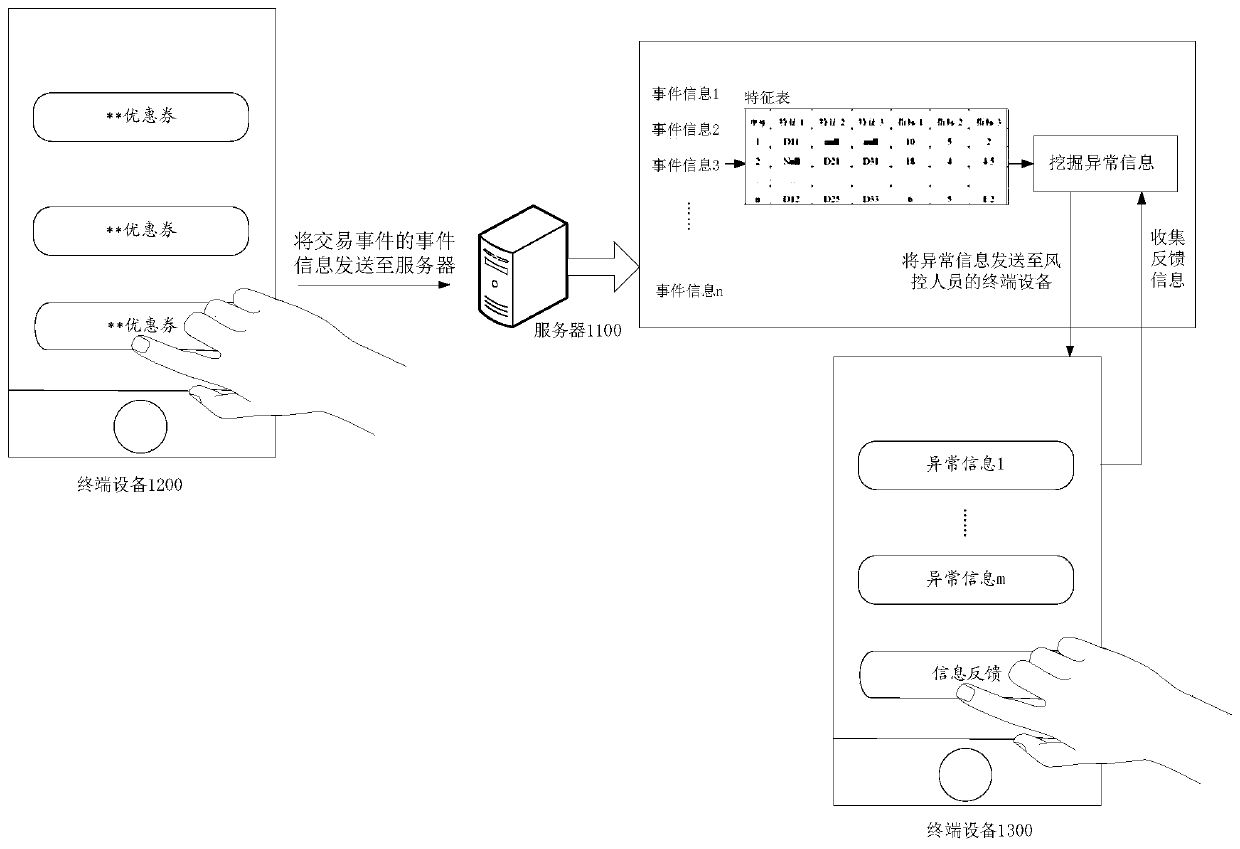
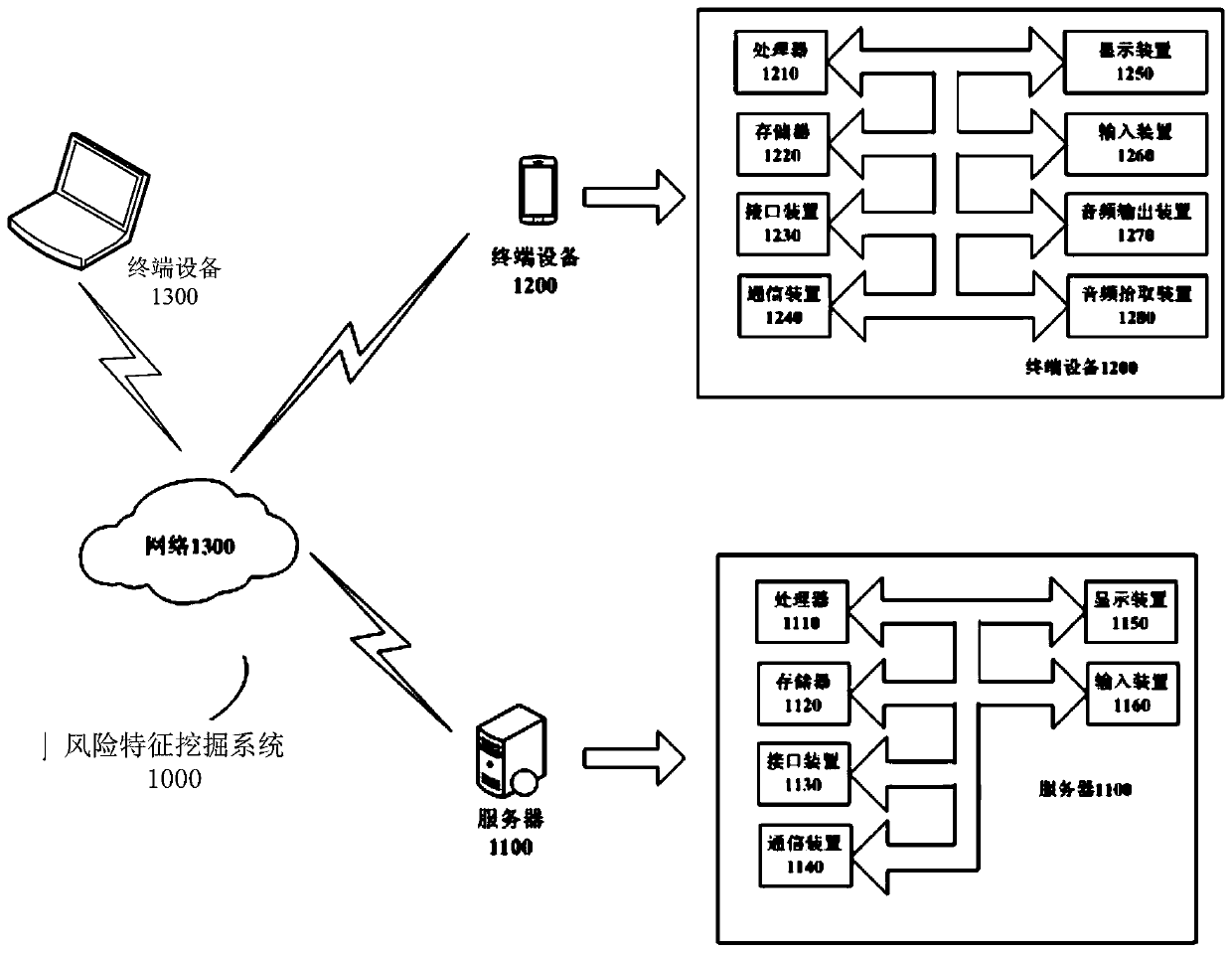
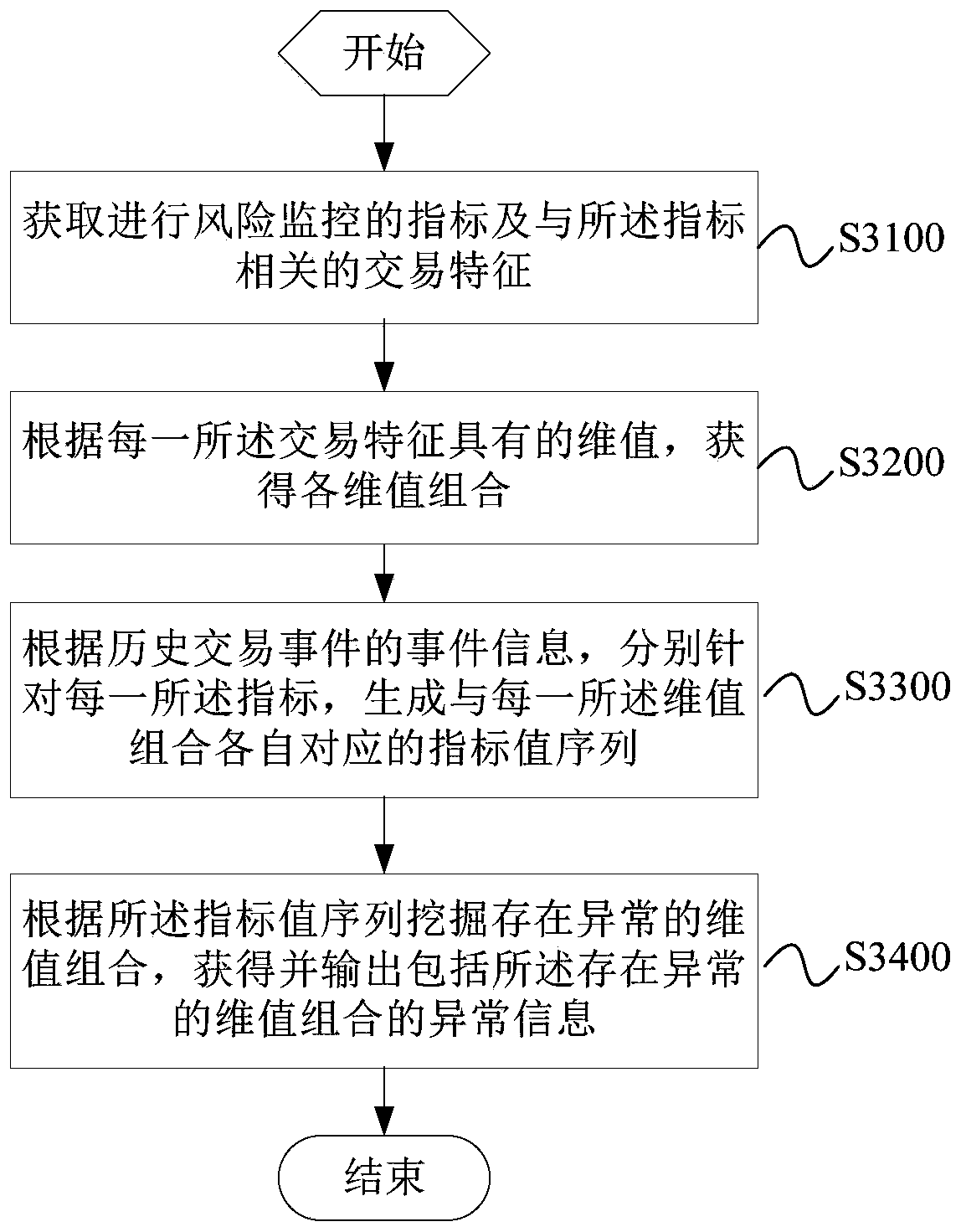
[0111] This embodiment provides a method for mining abnormal information. For example, the method can be implemented by a server as an abnormal information mining device. The server can be as follows figure 1 or figure 2 Server 1100 is shown. Such as image 3 As shown, the method may include the following steps S3100-S3400:
[0112] Step S3100, acquiring indicators for risk monitoring and transaction characteristics related to the indicators.
[0113] The indicators for risk monitoring can be set according to the risks that need to be monitored. For example, the risk that needs to be monitored is the risk of fleece. The indicators for risk monitoring can include the sum of the amount received at one time SUM(A), the number of coupons received at one time COUNT(B), and the sum of the amount SUM(A) and the number of coupons COUNT( Any one or multiple items in the ratio SUM(A) / COUNT(B) of B).
[0114] In this embodiment, one indicator for risk monitoring or multiple indicat...
Embodiment 2
[0206] Figure 5 It is a schematic flowchart of a method for identifying abnormal information according to another embodiment of this specification. This embodiment is implemented by a terminal device used by risk control personnel, for example, by figure 2 The terminal device 1300 in the implementation.
[0207] Such as Figure 5 As shown, the method in this embodiment may include the following steps S5100-S5300:
[0208] Step S5100, receiving abnormal information provided by the abnormal information mining device, including abnormal dimension value combination, wherein the dimension value combination is composed of at least one dimension value of each transaction feature, and the transaction feature is related to the index for risk monitoring.
[0209] Step S5200, obtaining feedback information provided for the abnormal information, wherein the feedback information includes the corresponding relationship between the features and validity of the dimension value combination...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com