Program vulnerability repair method and device, storage medium and server
A vulnerability repair and program technology, applied in the computer field, can solve problems such as incompatibility of large-scale projects, interruption of business operations, impact on user experience, etc., to avoid interruption and the impact of program operation, and to achieve the effect of simple and convenient operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
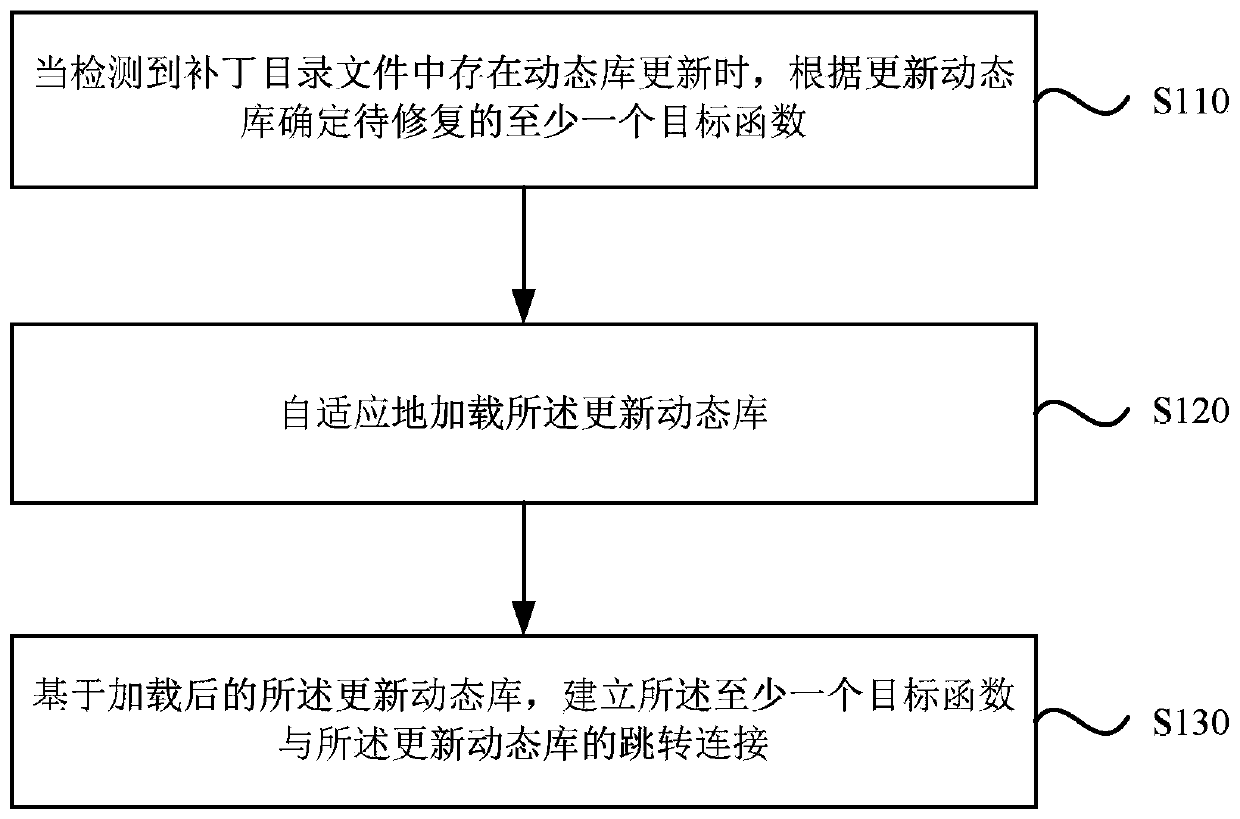
[0027] figure 1 It is a schematic flowchart of a method for repairing program vulnerabilities provided by Embodiment 1 of the present invention. This embodiment is applicable to the case of repairing program vulnerabilities for server clusters. This method can be executed by the device for repairing program vulnerabilities provided by the embodiment of the present invention. The vulnerability repairing device can be realized by means of software and / or hardware, and can be integrated into at least one server in the server cluster, and specifically includes the following steps:
[0028] S110. When it is detected that there is a dynamic library update in the patch directory file, determine at least one target function to be repaired according to the updated dynamic library.
[0029] S120. Adaptively load the updated dynamic library.
[0030] S130. Based on the loaded updated dynamic library, establish a jump connection between the at least one target function and the updated dy...
Embodiment 2
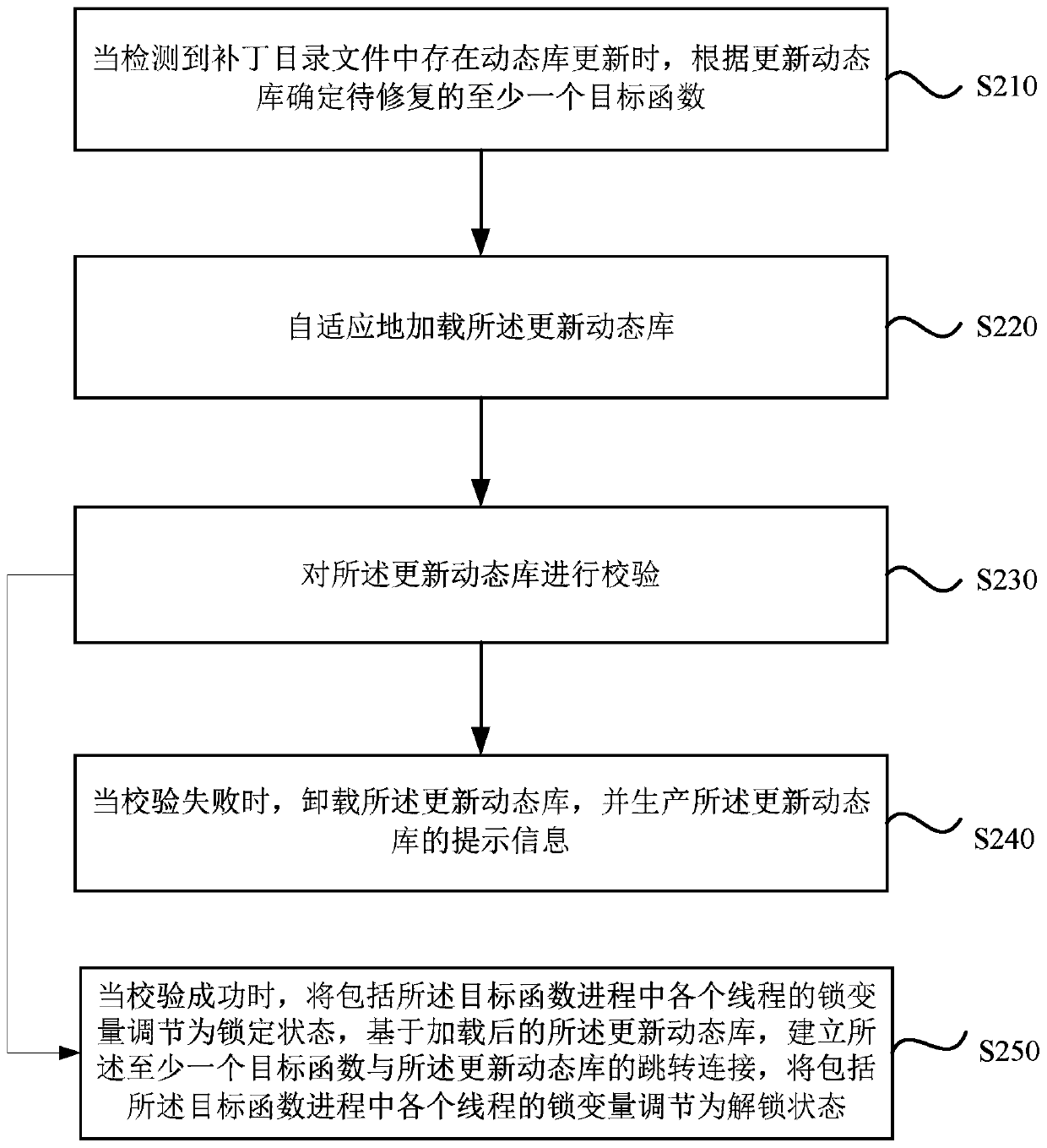
[0041] image 3 It is a schematic flow diagram of a method for repairing program bugs provided in Embodiment 2 of the present invention, which is optimized on the basis of the above embodiments, and the method specifically includes:
[0042] S210. When it is detected that there is a dynamic library update in the patch directory file, determine at least one target function to be repaired according to the updated dynamic library.
[0043] S220. Adaptively load the updated dynamic library.
[0044] S230. Verify the updated dynamic library.
[0045] S240. When the verification fails, uninstall the updated dynamic library, and generate prompt information for the updated dynamic library.
[0046] S250. When the verification is successful, set the lock variable including each thread in the target function process to a locked state, and based on the loaded updated dynamic library, establish a relationship between the at least one target function and the updated dynamic library The ...
Embodiment 3
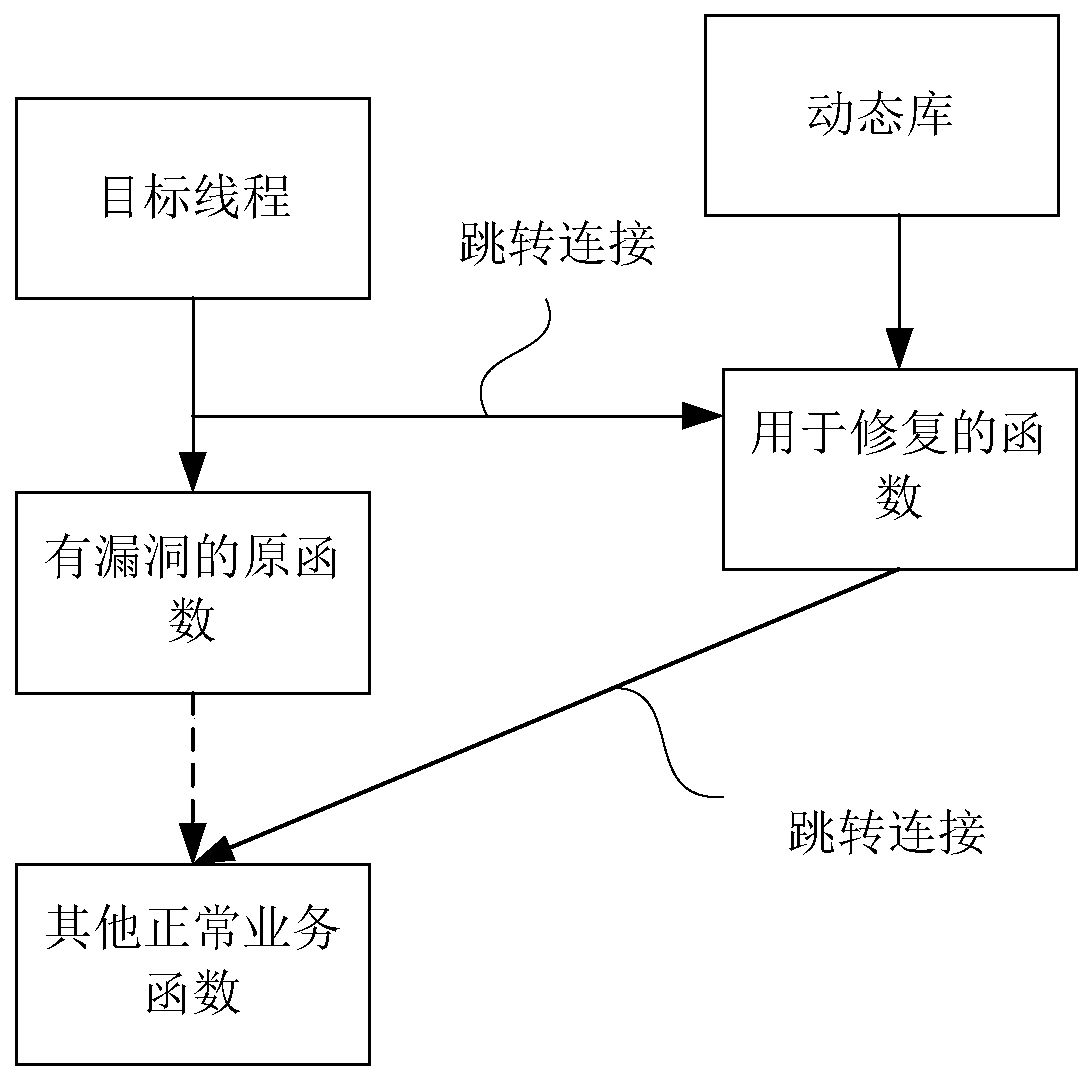
[0054] Figure 4 It is a schematic structural diagram of a program vulnerability repairing device provided in Embodiment 3 of the present invention. The device includes a target function determination module 310, a dynamic library loading module 320, and a target function repairing module 330, wherein:
[0055] The target function determination module 310 is used to determine at least one target function to be repaired according to the updated dynamic library when it is detected that there is a dynamic library update in the patch directory file;
[0056] A dynamic library loading module 320, configured to adaptively load the updated dynamic library;
[0057] The target function repair module 330 is configured to establish a jump connection between the at least one target function and the updated dynamic library based on the loaded updated dynamic library, wherein the jump connection is used to execute any When the target function is described, the update dynamic library is ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com