A detection method and system for a detector control attack
A detection method and detection system technology, which are applied in transmission systems, digital transmission systems, security communication devices, etc., can solve problems such as low code rate, difference in monitoring range, and difficulty in experiment implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
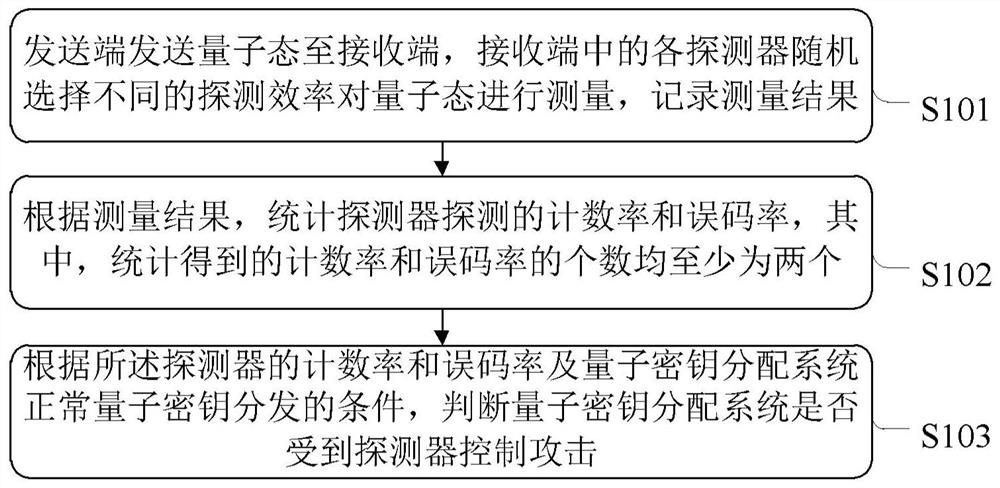
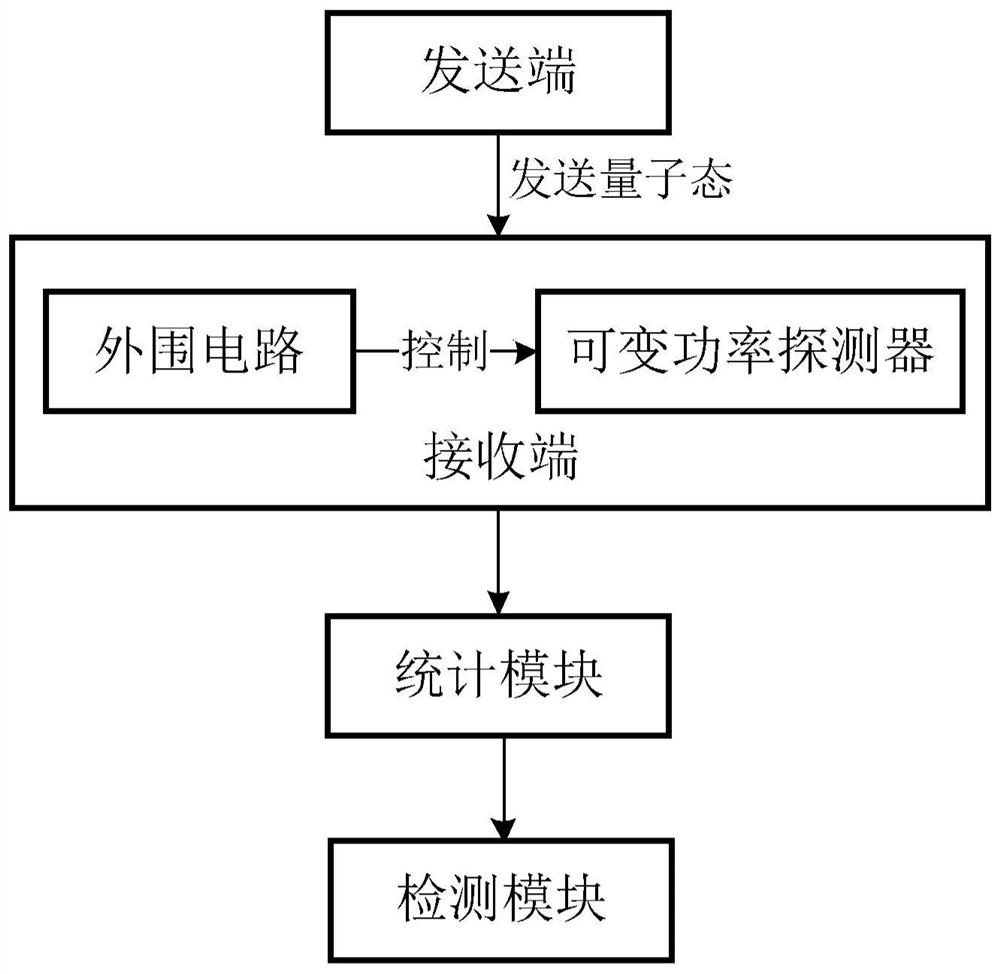
[0032] See figure 1 , figure 1 It is a flow chart of the detection method of the detector control attack provided by the first embodiment of the present invention, which is used to detect the detector control attack in the quantum key distribution system. The method is implemented based on a defense model (variable efficiency detector), including:
[0033] S101, the sending end sends the quantum state to the receiving end, each detector in the receiving end randomly selects different detection efficiencies to measure the quantum state, and records the measurement result.
[0034] Specifically, Alice at the sending end prepares a set of quantum states, and each time randomly selects any one of the two sets of mutual unbi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com