Access control method, device and system
An access control and access control technology, applied in the field of devices and systems, and access control methods, can solve problems affecting the security of access control, and achieve the effects of preventing intrusion attacks and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
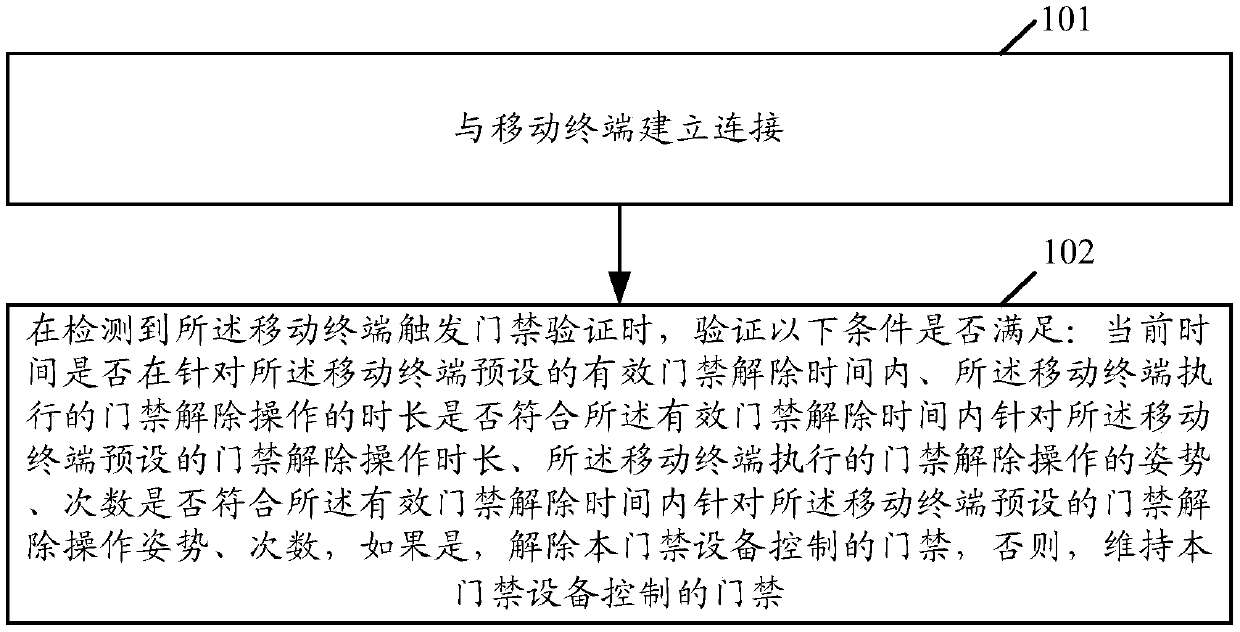
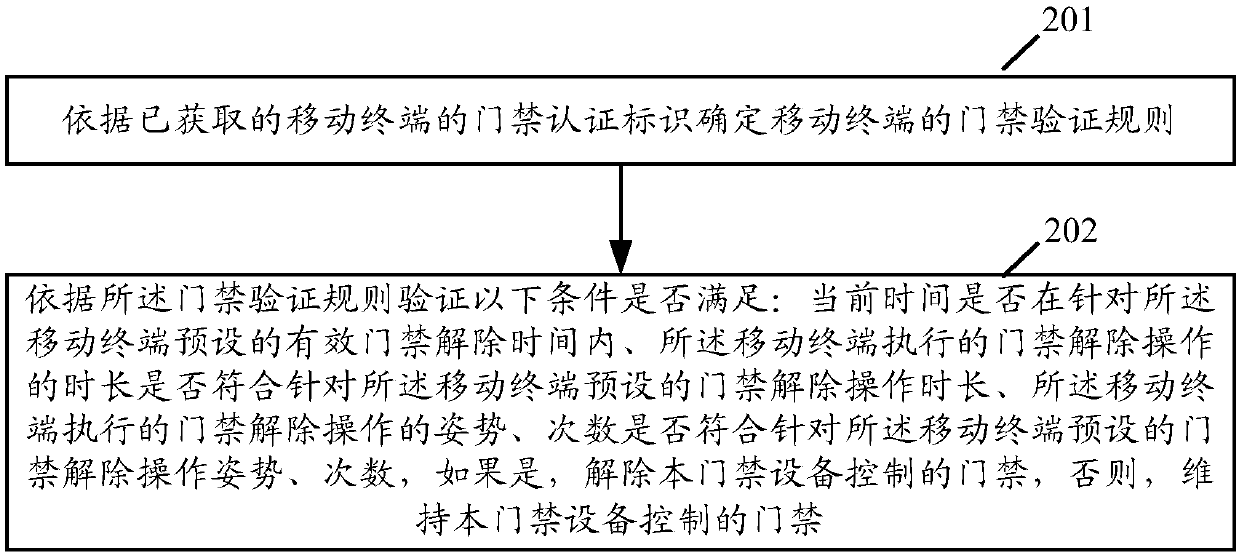
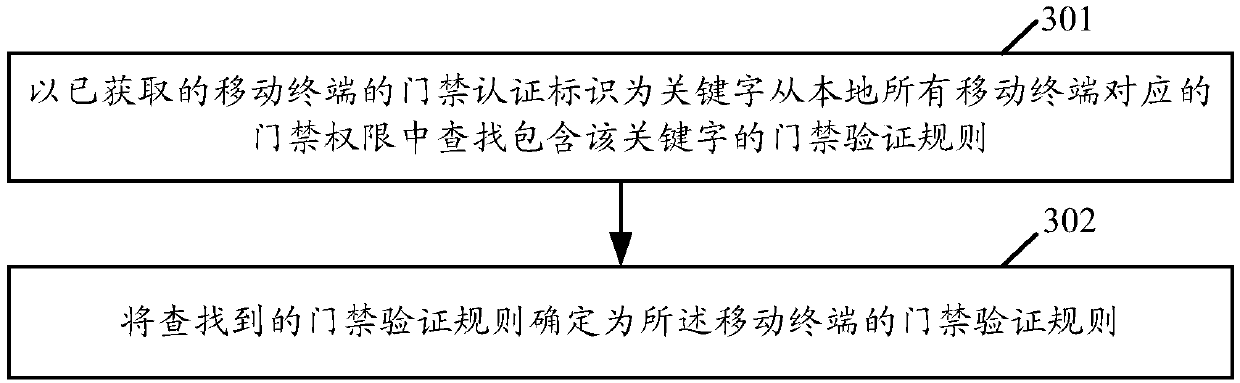
[0049] In the access control method provided by the present application, the current time when the mobile terminal triggers the access control verification, and the duration, posture, and times of the access control release operation performed by the mobile terminal are involved in the access control verification. Compared with the existing fixed access control equipment, all mobile The terminal has the same access control verification rules in all time periods. This application can greatly improve the security of the access control equipment and effectively prevent intrusion attacks by third-party illegal users. In an example, the access control device here may be a door station, an access control card reader, etc., which are not specifically limited in this application.
[0050] In order to make the purpose, technical solutions and advantages of the present application clearer, the present invention will be described in detail below in conjunction with the accompanying drawin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com