A Construction Method of Network Intrusion Detection Dataset in Small Sample Scenario
A network intrusion detection and construction method technology, applied in the field of information security, can solve the problems of research work and evaluation difficulties, and achieve the effect of keeping the main time and space structure unchanged, reducing construction costs, and preserving relevance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in further detail below in conjunction with the accompanying drawings.
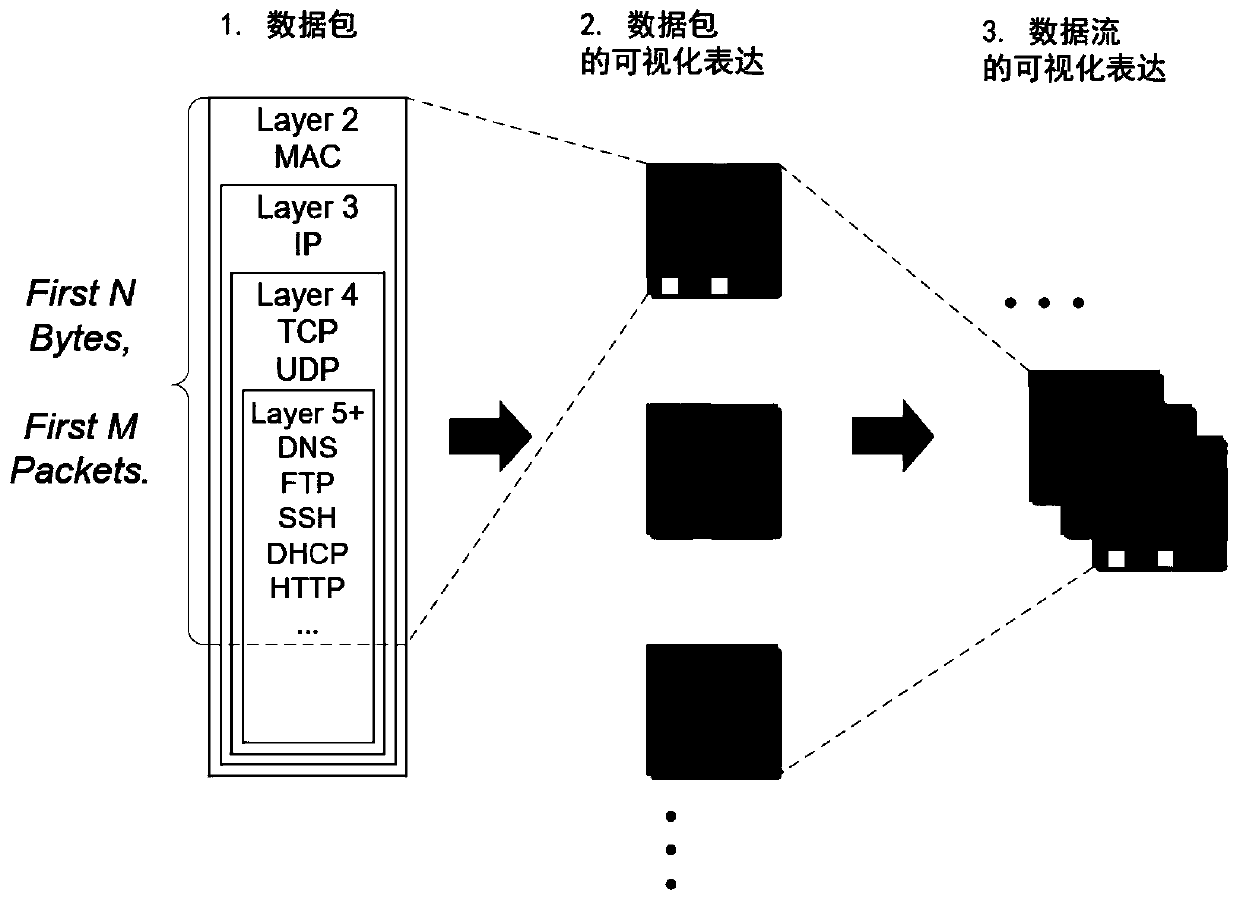
[0038] Step 1: Obtain network traffic packets from the target network. According to the definition of the Open System Interconnection (OSI) reference model, the network is divided into 7 layers from bottom to top. The smallest transmission unit of network traffic is a data packet, and each data packet consists of a header and a payload. For example, a hypertext transfer protocol (Hyper TextTransfer Protocol, HTTP) data packet sequentially includes a 14-byte medium access control (Medium Access Control, MAC) layer header, a 20-byte Internet Protocol (Internet Protocol, IP) layer header, and a 20-byte Section Transmission Control Protocol (Transmission Control Protocol, TCP) layer header, and then the HTTP header and payload.
[0039] The data packets obtained through the packet capture program can be reflected in the network traffic data except the first phy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com