Security log collection and analysis method, device and equipment and medium
An analysis method and log technology, which is applied in the field of security log collection and analysis, can solve the problems of high development cost, difficulty in analysis and use, separation of regular expressions and variables, etc., and achieve the effect of efficient processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
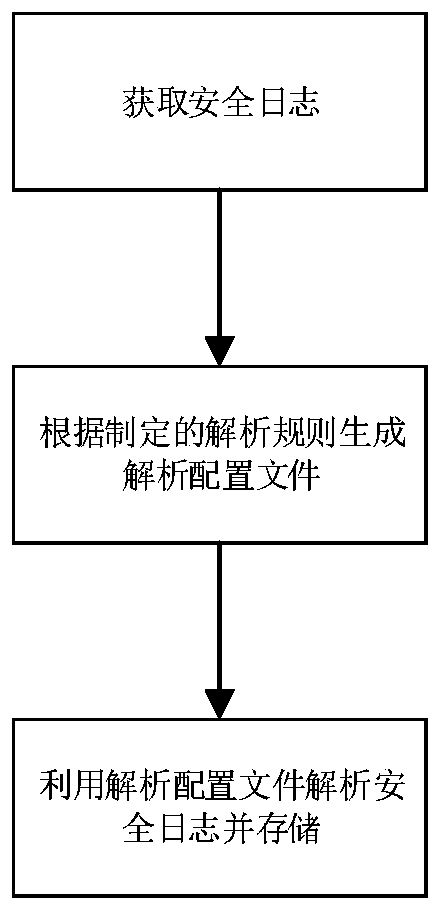
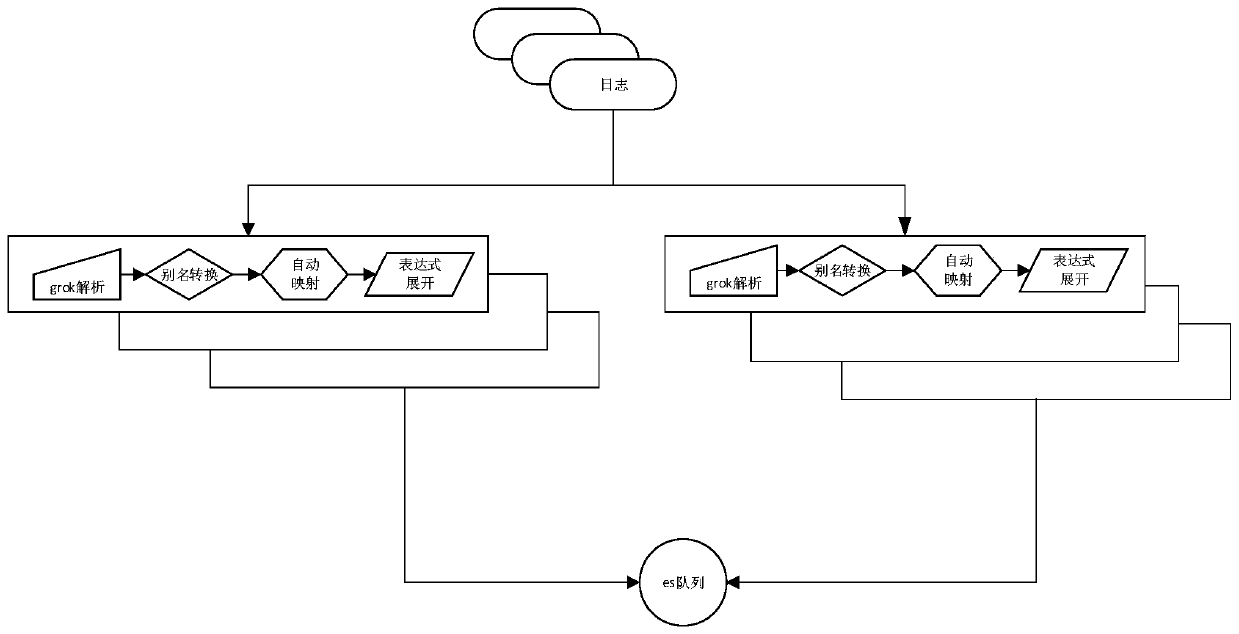
[0032] This embodiment provides a method for collecting and analyzing security logs, which aims to formulate different types of analysis rules according to different scenarios and different types of security logs, and write different analysis rules into the analysis configuration file to realize the analysis of different types of security logs. unified processing.
[0033] According to the above principles, the security log collection and analysis method is introduced, as follows: figure 1 Shown:
[0034] The security log collection and analysis method specifically includes the following steps:
[0035] receive security logs;
[0036] Generate a parsing configuration file according to the formulated parsing rules;
[0037] The security log is parsed by using the parsing configuration file, and the parsed security log is stored.
[0038] In this embodiment, the syslog server is used as the log accepting server to complete the receiving of the security log. The syslog server...
Embodiment 2
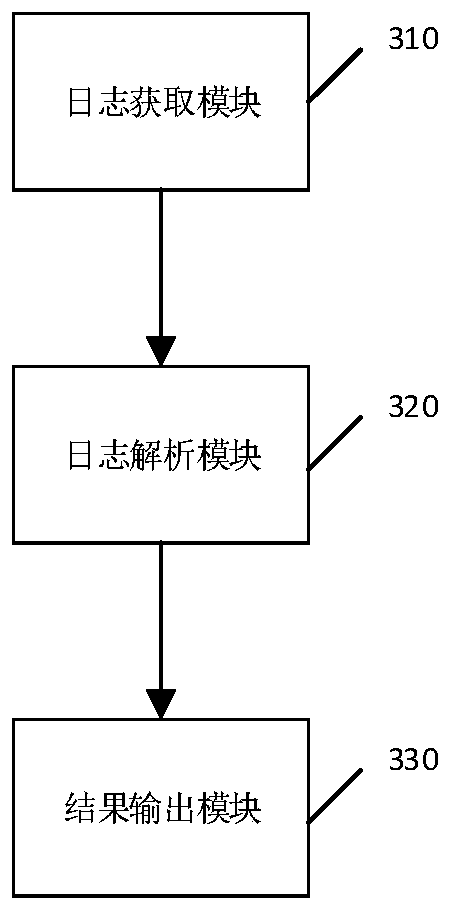
[0054] Embodiment 2 discloses a device corresponding to the security log collection and analysis method in Embodiment 1, which is the virtual device structure of the above embodiment, please refer to figure 2 shown, including:
[0055] A log acquisition module 310, configured to receive a security log;
[0056] The log analysis module 320 is configured to generate an analysis configuration file according to the analysis rules, and utilize the analysis configuration file to complete security log analysis;
[0057] The result output module 330 is configured to output a security log analysis result and store the security log analysis result.
Embodiment 3
[0059] Figure 4 A schematic structural diagram of an electronic device provided by Embodiment 3 of the present invention, such as Figure 4 As shown, the electronic device includes a processor 410, a memory 420, an input device 430, and an output device 440; the number of processors 410 in a computer device may be one or more, Figure 4 Take a processor 410 as an example; the processor 410, memory 420, input device 430 and output device 440 in the electronic device can be connected by bus or other methods, Figure 4 Take connection via bus as an example.
[0060] The memory 420, as a computer-readable storage medium, can be used to store software programs, computer executable programs and modules, such as program instructions / modules corresponding to the security log collection and analysis method in the embodiment of the present invention (for example, a security log collection and analysis device The log acquisition module 310, the log parsing module 320 and the result ou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com