A security flow control device and method for a mimetic switch
A technology of flow control device and switch, applied in data exchange network, data exchange through path configuration, digital transmission system, etc., can solve problems such as low efficiency and difficulty in distribution and assignment, so as to improve security and increase attacks effect of difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
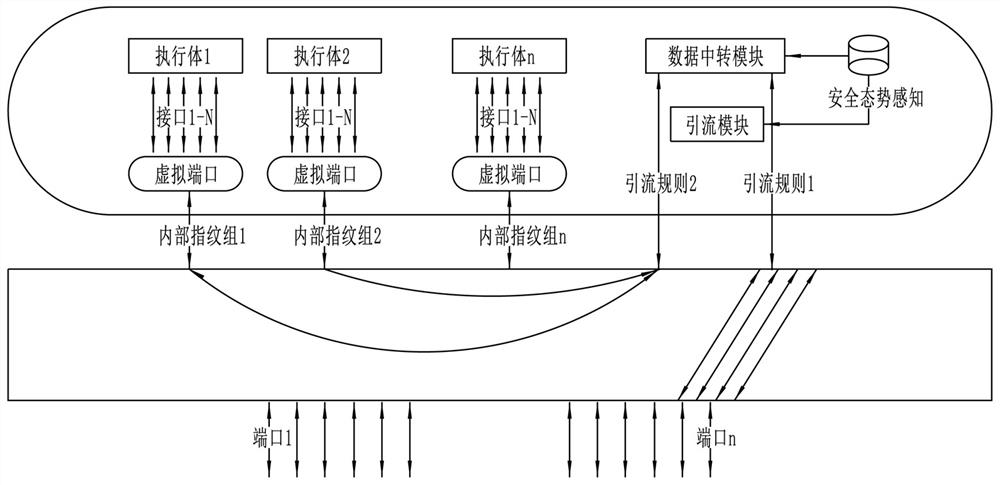
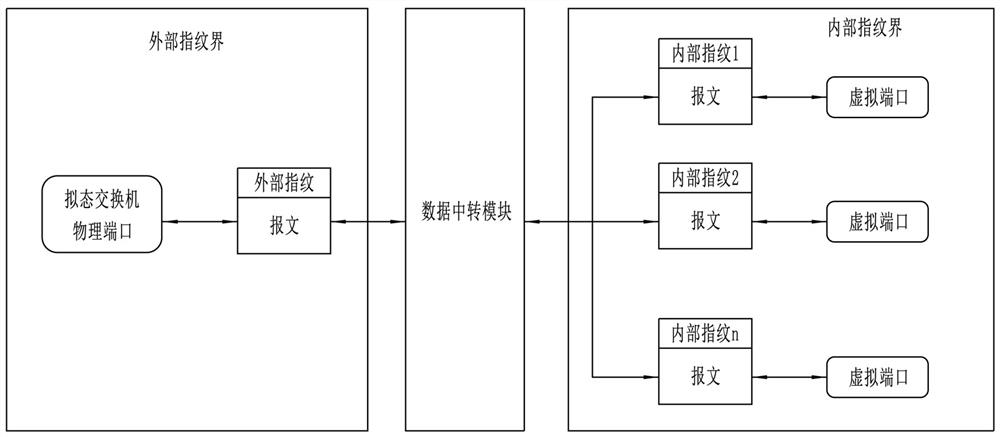
[0045] Such as figure 1 and figure 2 As shown, a security flow control device for a mimetic switch, including:
[0046]The security situation awareness module is used to maintain the message feature database and formulate security policies; the message feature database records the message feature tuples related to the security of the mimic switch, and the security policy is a dynamic rule formulated by the current security situation , including message filtering mechanism, external fingerprint and internal fingerprint mapping relationship information;
[0047] The drainage module formulates dynamic drainage strategies, maintains the data path of the security traffic of the mimic switch between the physical port of the mimic switch and the data transfer module, and maintains the data path between the data transfer module and the virtual port of the heterogeneous executive body;
[0048] The data transfer module executes the message parsing process on the traffic from the phy...
Embodiment 2
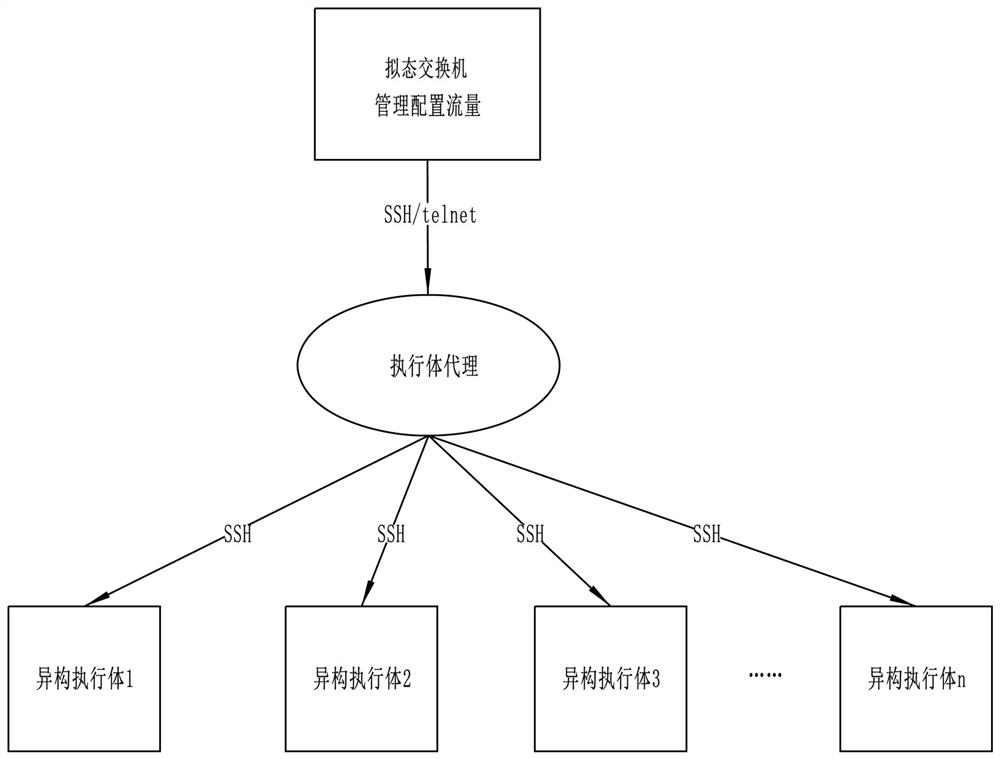
[0058] Such as image 3 and Figure 4 As shown, the difference between this embodiment and Embodiment 1 is that: the data transfer module sets an executive agent, and the executive agent includes a main executive and a distribution agent module, and the distribution agent module receives data from the physical port of the mimic switch The traffic is redirected to the main executive body and establishes connection with each heterogeneous executive body; the main executive body manages the configuration information, and distributes the configuration information to each heterogeneous executive body through the distribution agent module. Wherein, the main executive is elected from the pool of heterogeneous executives according to the election algorithm specified by the security situation awareness module. In particular, the distribution agent module redirects the traffic from the physical port of the mimic switch to the main executive and establishes SSH connections with each het...
Embodiment 3
[0064] Such as Figure 5 As shown, the difference between this embodiment and embodiment 2 is that a specific common security message is provided, such as protocol messages such as ARP and ICMP, the security flow control method:
[0065] ①Assume that the traffic enters from the physical port 17 of the mimic switch;
[0066] ②The message is captured by the drainage rules of the drainage module and redirected to the data transfer module;
[0067] ③The data transfer module analyzes the external fingerprint carried by the message, that is, the frame mark, and knows that the message enters from port 17, and needs to send it to the corresponding port 17 of the main executive;
[0068] ④The data transfer module completes the fingerprint transformation according to the mapping relationship between the internal fingerprint and the external fingerprint;
[0069] ⑤The message is sent from the data transfer module, carrying the VLAN tag that can be identified by the internal fingerprint...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com