Long information pushing method and device in bypass environment
An information push and environment technology, applied in the field of information network, can solve deployment and other problems, and achieve the effect of saving physical resources and good confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
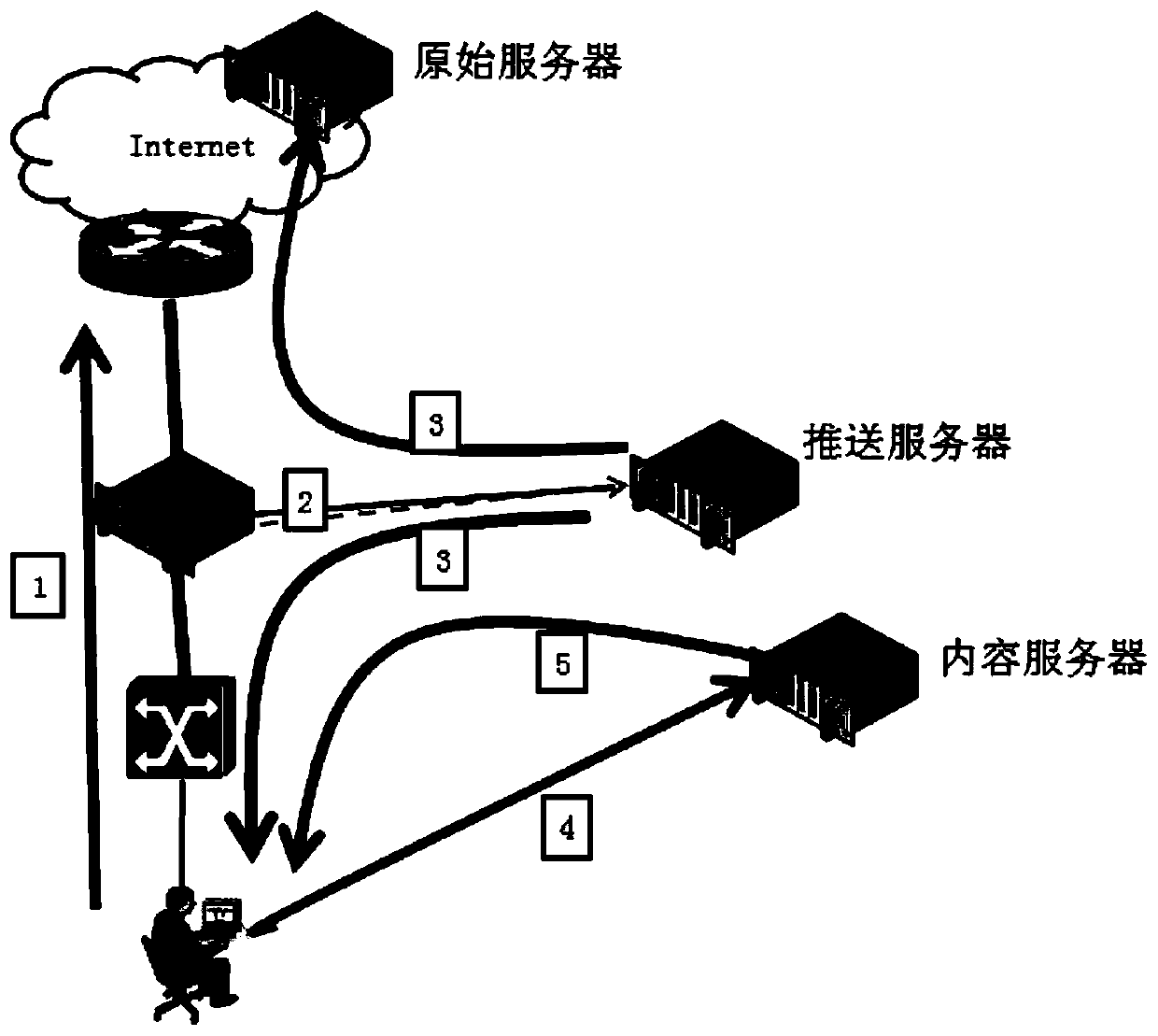
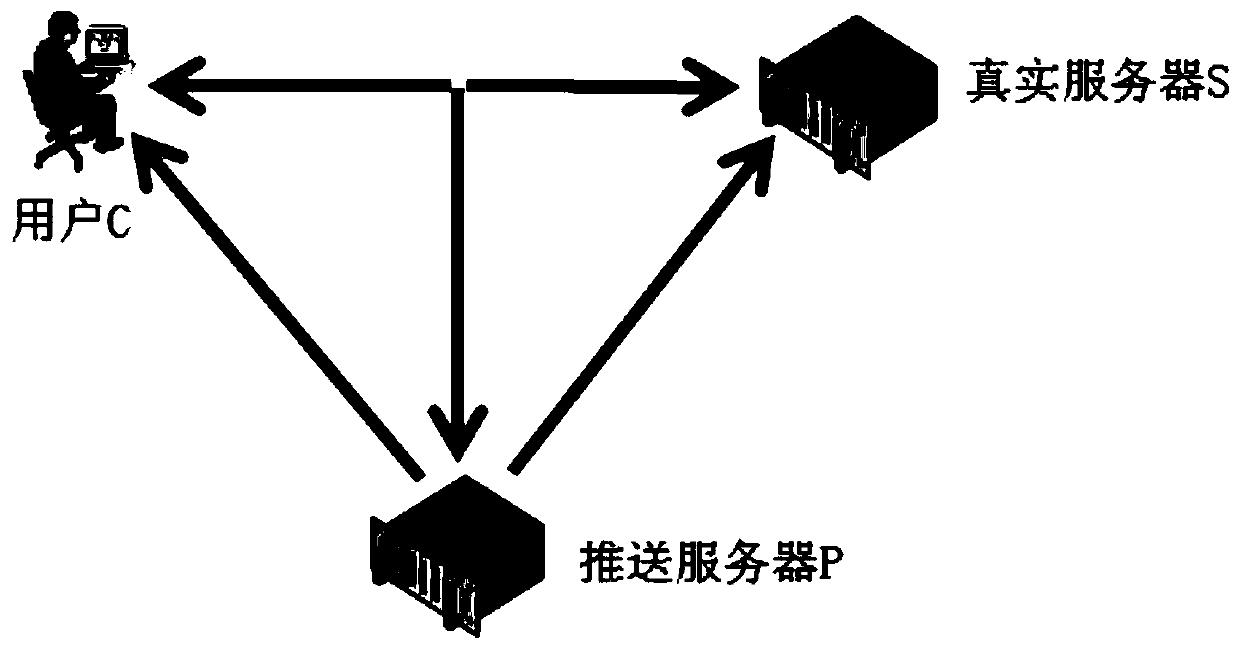
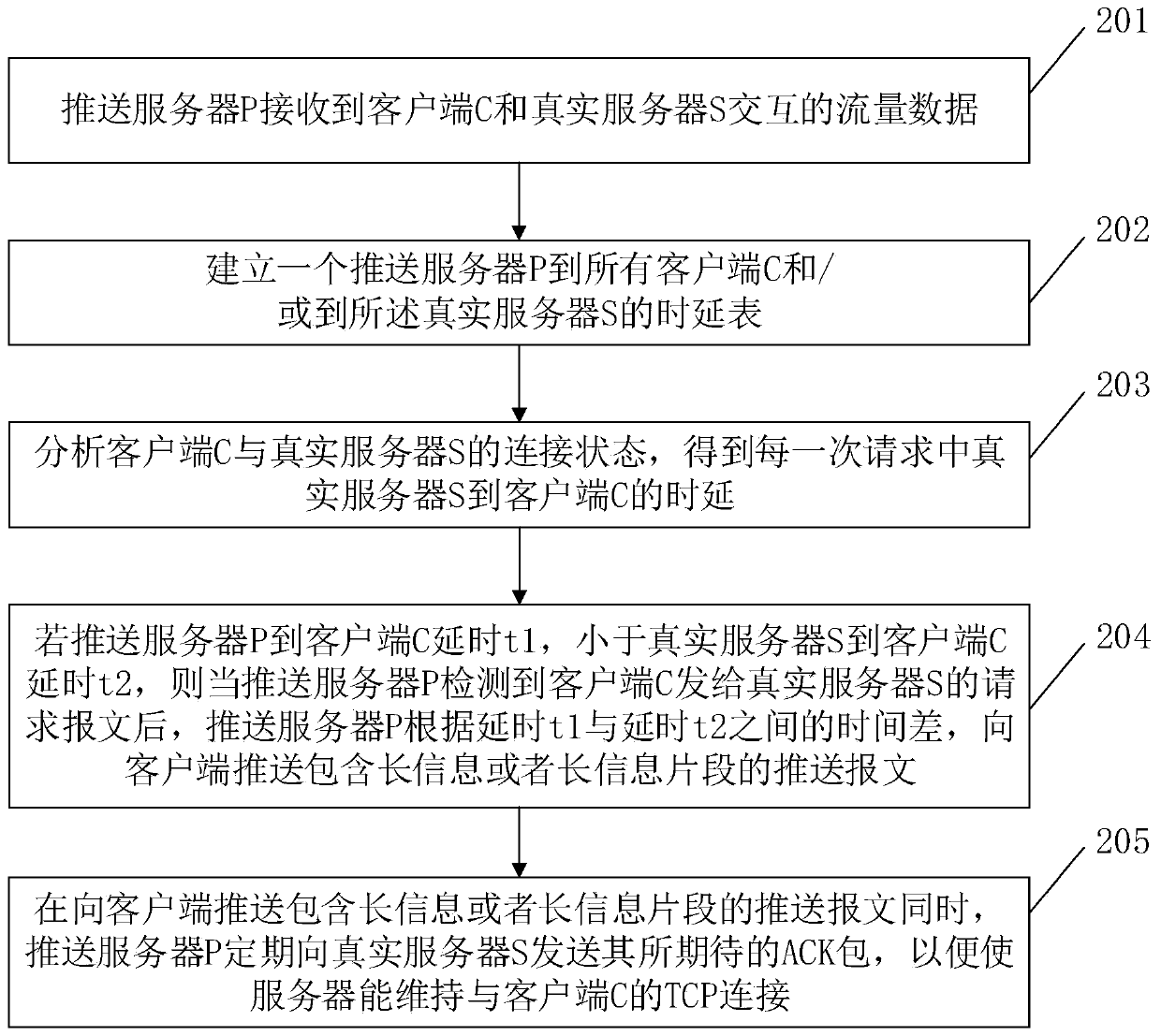
[0064] Embodiment 1 of the present invention provides a method for pushing long information in a bypass environment, and its system architecture is as follows figure 2 As shown, the client C and the real server S perform TCP interaction, and all the interactive messages can be received by the push server P, and the push server P is transparent to the client C and the real server S. In the embodiment of the present invention, the push server P selectively sends a packet to the user C or the real server S. When the push server P sends a packet to the user C, the source IP is the real server S. When the push server P sends a packet to the real server S, The source IP is user C; the interaction parties are user C and real server S. If two packets with the same TCP sequence number are received, the one received first shall prevail, and the one received later will be considered as duplicate information and discarded. Such as image 3 As shown, the methods include:
[0065] In ste...
Embodiment 2
[0085] Such as Figure 6 As shown, it is a schematic structural diagram of an apparatus for pushing long information in a bypass environment according to an embodiment of the present invention. The apparatus for pushing long information in a bypass environment in this embodiment includes one or more processors 21 and memory 22 . in, Figure 6 A processor 21 is taken as an example.
[0086] Processor 21 and memory 22 can be connected by bus or other means, Figure 6 Take connection via bus as an example.
[0087] Memory 22 is a non-volatile computer-readable storage medium as a method and device for pushing long information in a bypass environment, and can be used to store non-volatile software programs and non-volatile computer-executable programs, as in Embodiment 1 A method for pushing long messages in a bypass environment. The processor 21 runs the non-volatile software program and instructions stored in the memory 22, so as to execute the method of pushing long inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com