Sensitive information identification method and device, electronic equipment and storage medium
A sensitive information identification and sensitive technology, applied in the field of data processing, can solve problems such as unrecognizable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
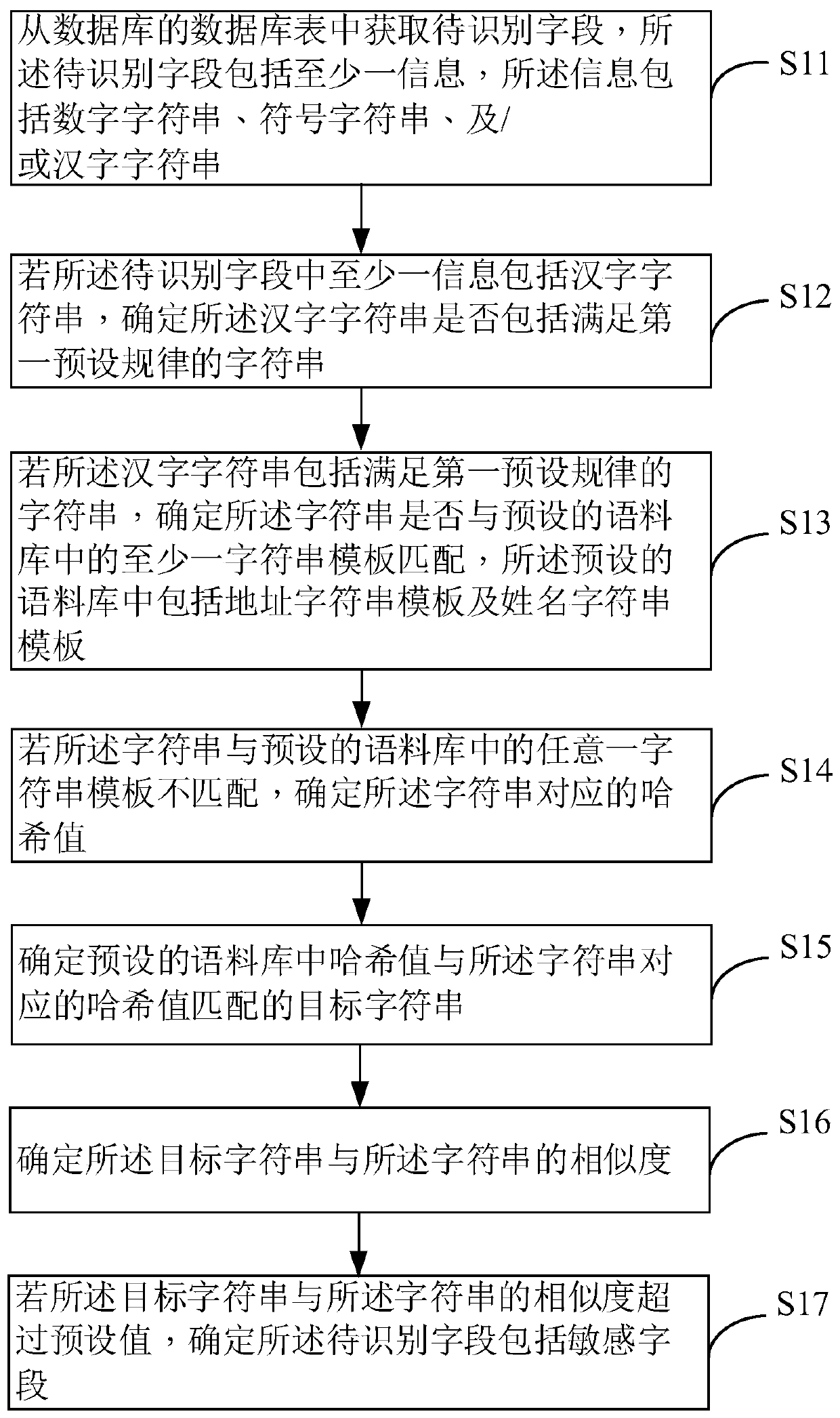
[0030] figure 1 It is a flow chart of the sensitive information identification method provided by Embodiment 1 of the present invention. The method is applied to an electronic device, and the electronic device may be any electronic product, for example, a personal computer, a tablet computer, a smart phone, a personal digital assistant (Personal Digital Assistant, PDA) and the like. Such as figure 1 As shown, the sensitive information identification method may include the following steps:
[0031] S11: Obtain a field to be recognized from a database table of the database, where the field to be recognized includes at least one piece of information, and the information includes a string of numbers, a string of symbols, and / or a string of Chinese characters.
[0032] The database can be an Oracle database, a SQL Server database, a Mysql database, a Sybase database, or a Hadoop database. At least one database table is stored in the database. The database table includes at leas...
Embodiment 2
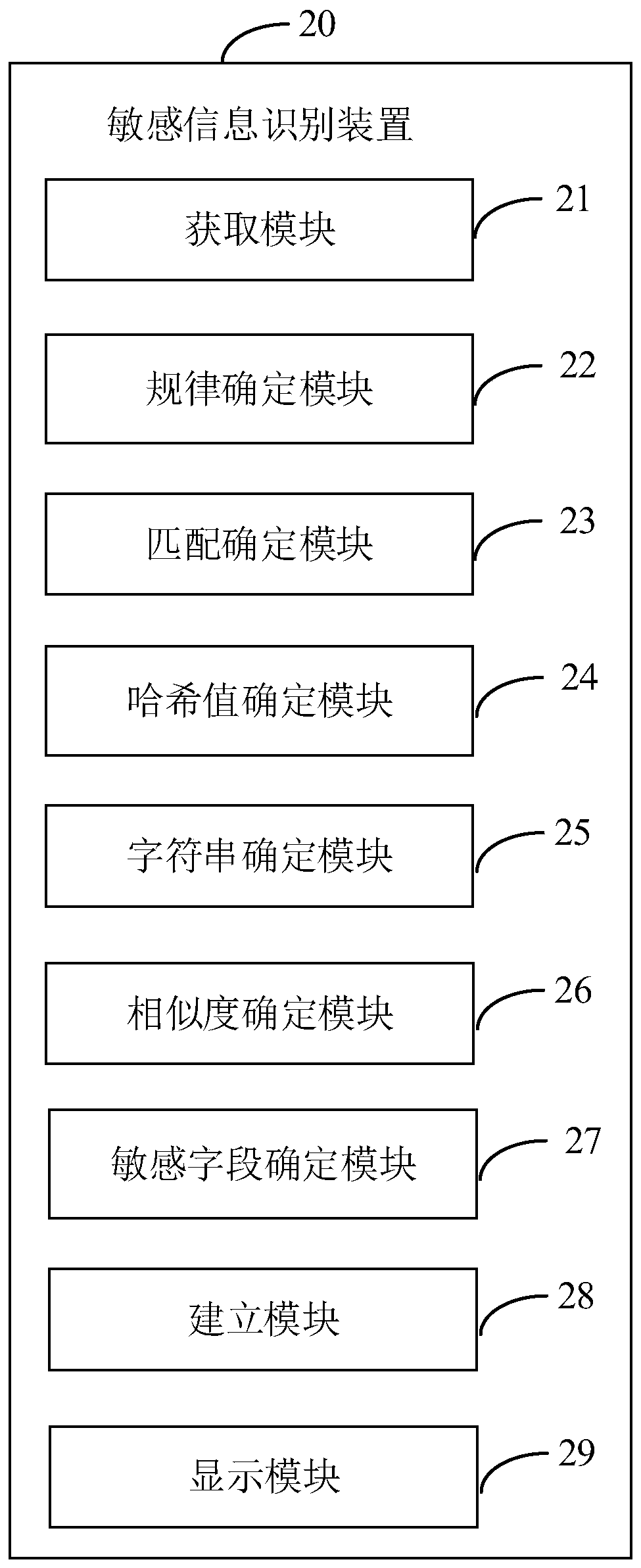
[0174] figure 2 It is a functional block diagram of the sensitive information identification device provided by Embodiment 2 of the present invention. In some embodiments, the sensitive information identification device 20 runs in an electronic device. The electronic device may be any electronic product, for example, a personal computer, a tablet computer, a smart phone, a personal digital assistant (Personal Digital Assistant, PDA) and the like. The sensitive information identification device 20 may include a plurality of functional modules composed of program code segments. The program codes of each program segment in the sensitive information identification device 20 can be stored in a memory and executed by at least one processor to automatically confirm customer service quality.
[0175] In this embodiment, the sensitive information identification device 20 can be divided into multiple functional modules according to the functions it performs. The functional modules m...
Embodiment 3
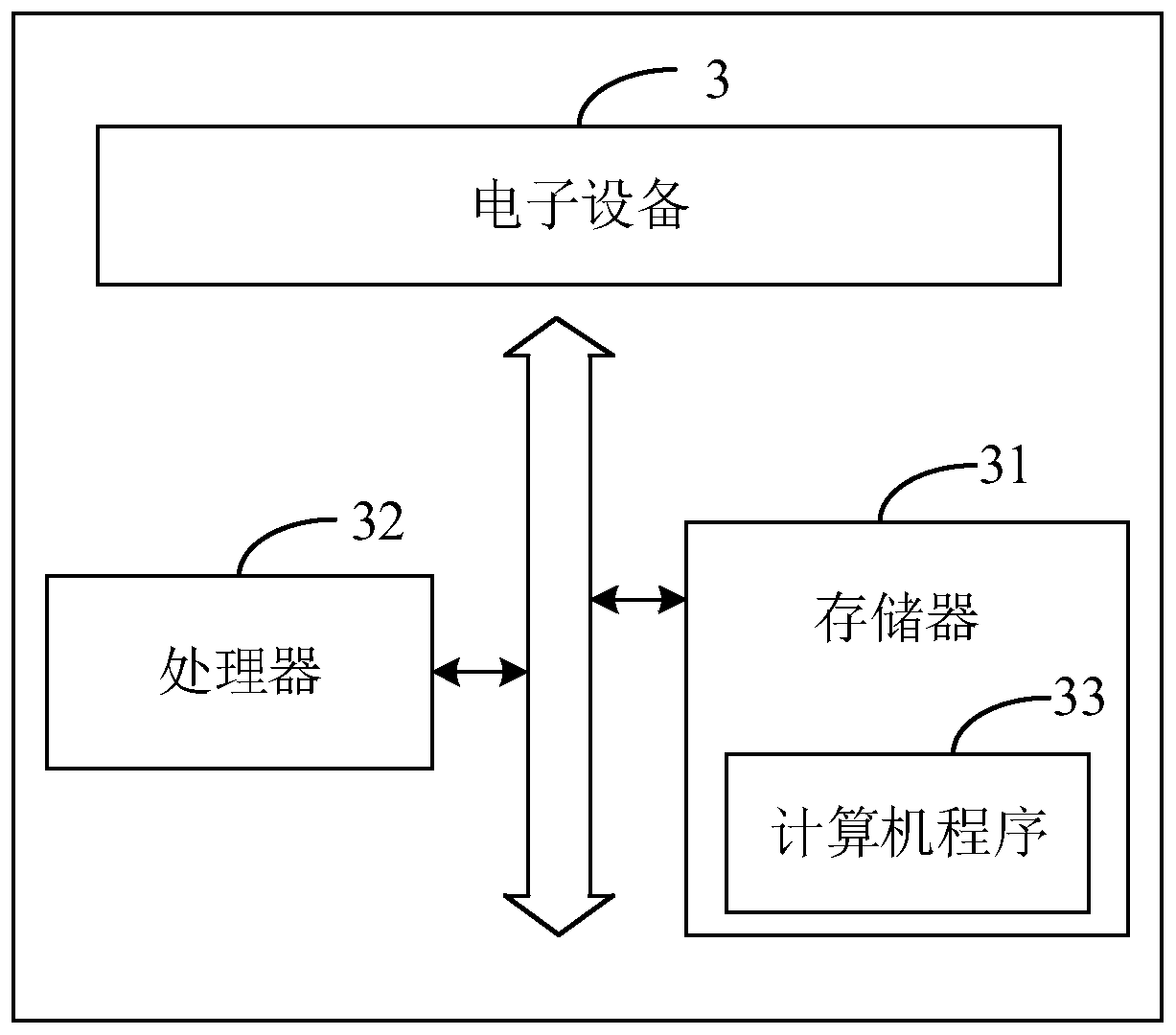
[0319] image 3 It is a schematic diagram of the electronic device provided by Embodiment 3 of the present invention.
[0320] The electronic device 3 includes: a memory 31 , at least one processor 32 , and a computer program 33 stored in the memory 31 and operable on the at least one processor 32 . When the at least one processor 32 executes the computer program 33, the steps in the foregoing method embodiments are implemented. Alternatively, when the at least one processor 32 executes the computer program 33, the functions of the modules in the above device embodiments are realized.
[0321] Exemplarily, the computer program 33 may be divided into one or more modules / units, and the one or more modules / units are stored in the memory 31 and executed by the at least one processor 32, To complete the present invention. The one or more modules / units may be a series of computer program instruction segments capable of accomplishing specific functions, and the instruction segment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com