Preventing misure of copied subscriber identity in mobile communication system
A technology for user identification and device identification number, which is applied in the field of prohibiting the abuse of a duplicated user identification code in a mobile communication, and can solve the problems of undiscoverable and expensive calls.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
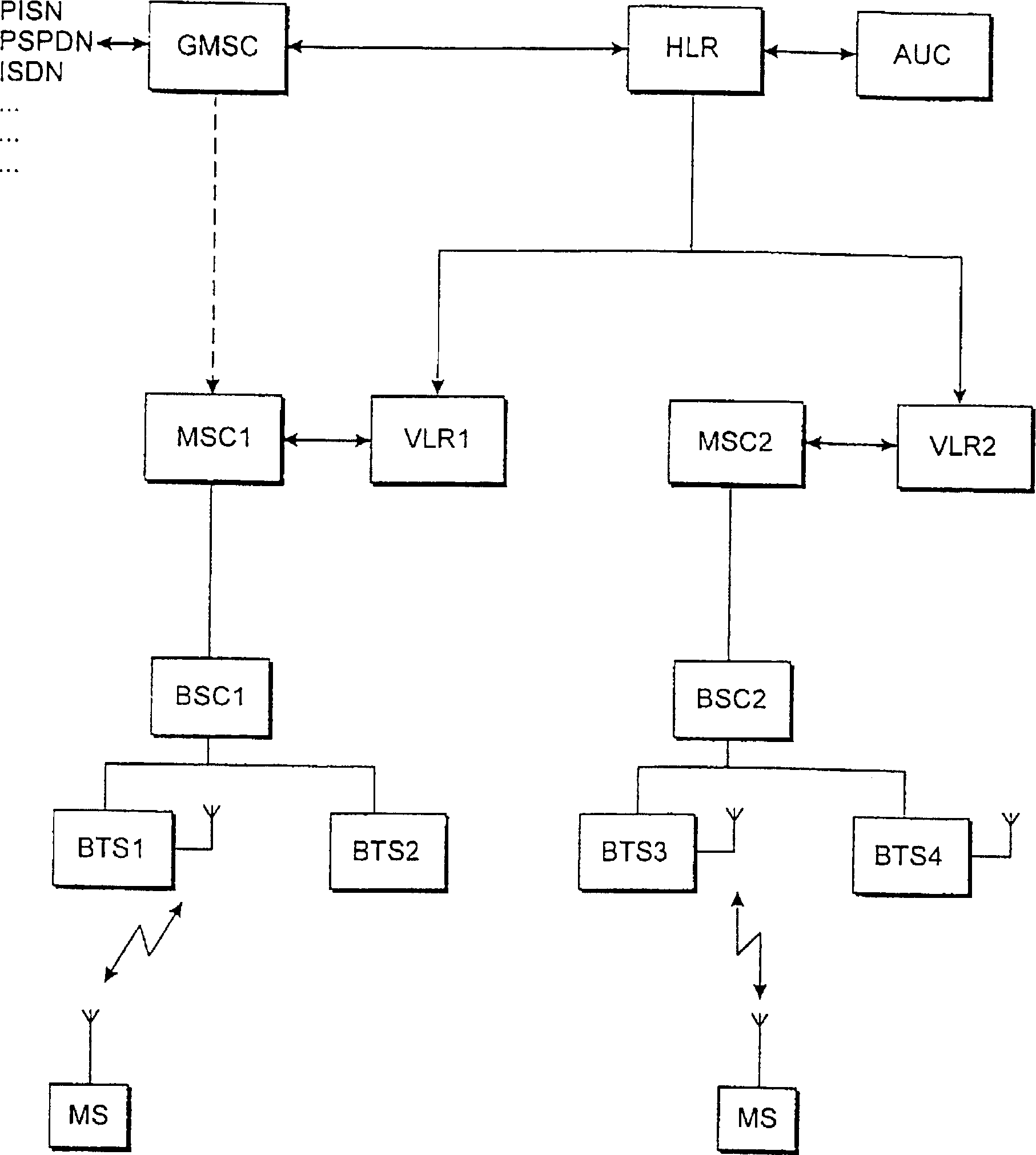
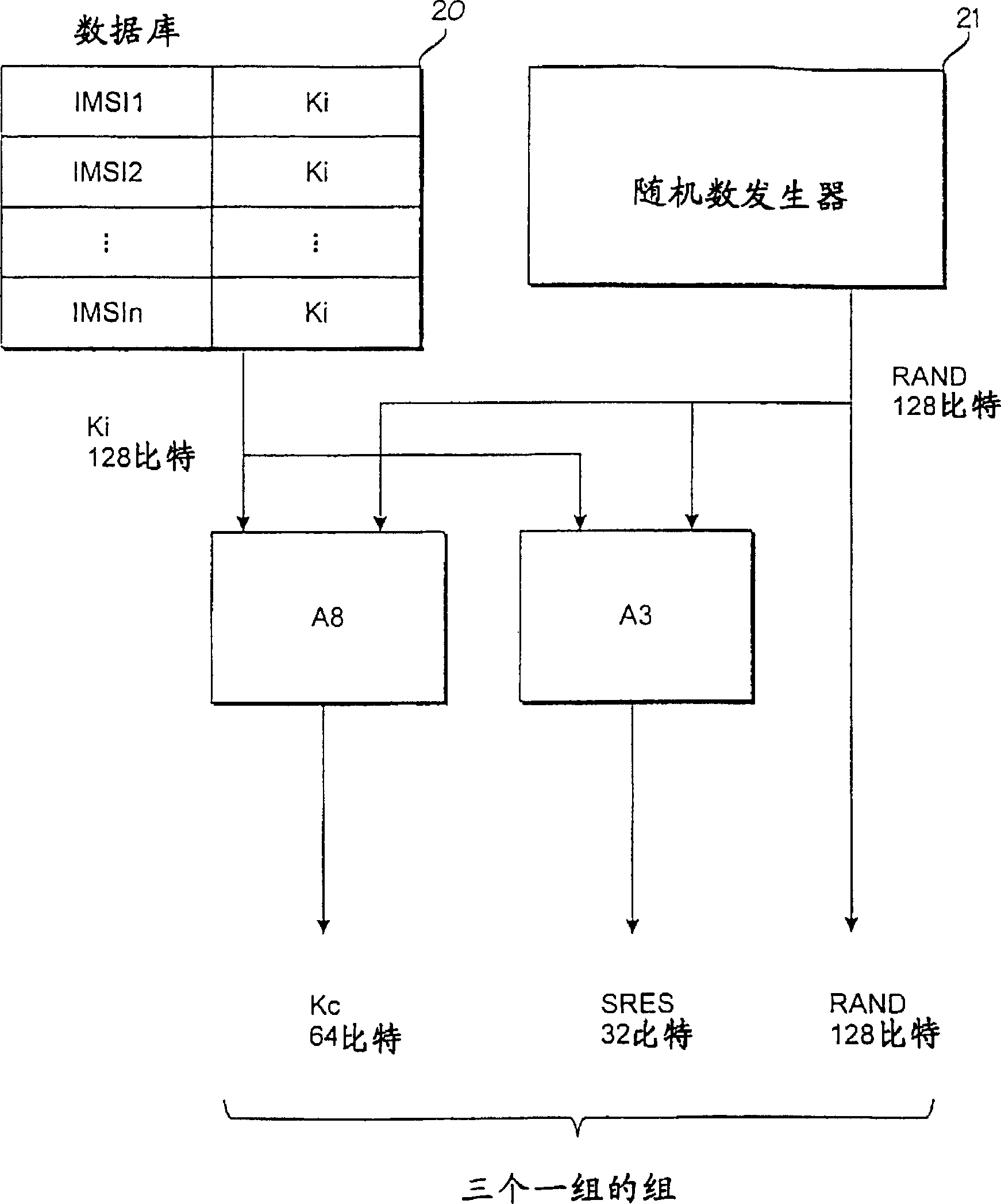
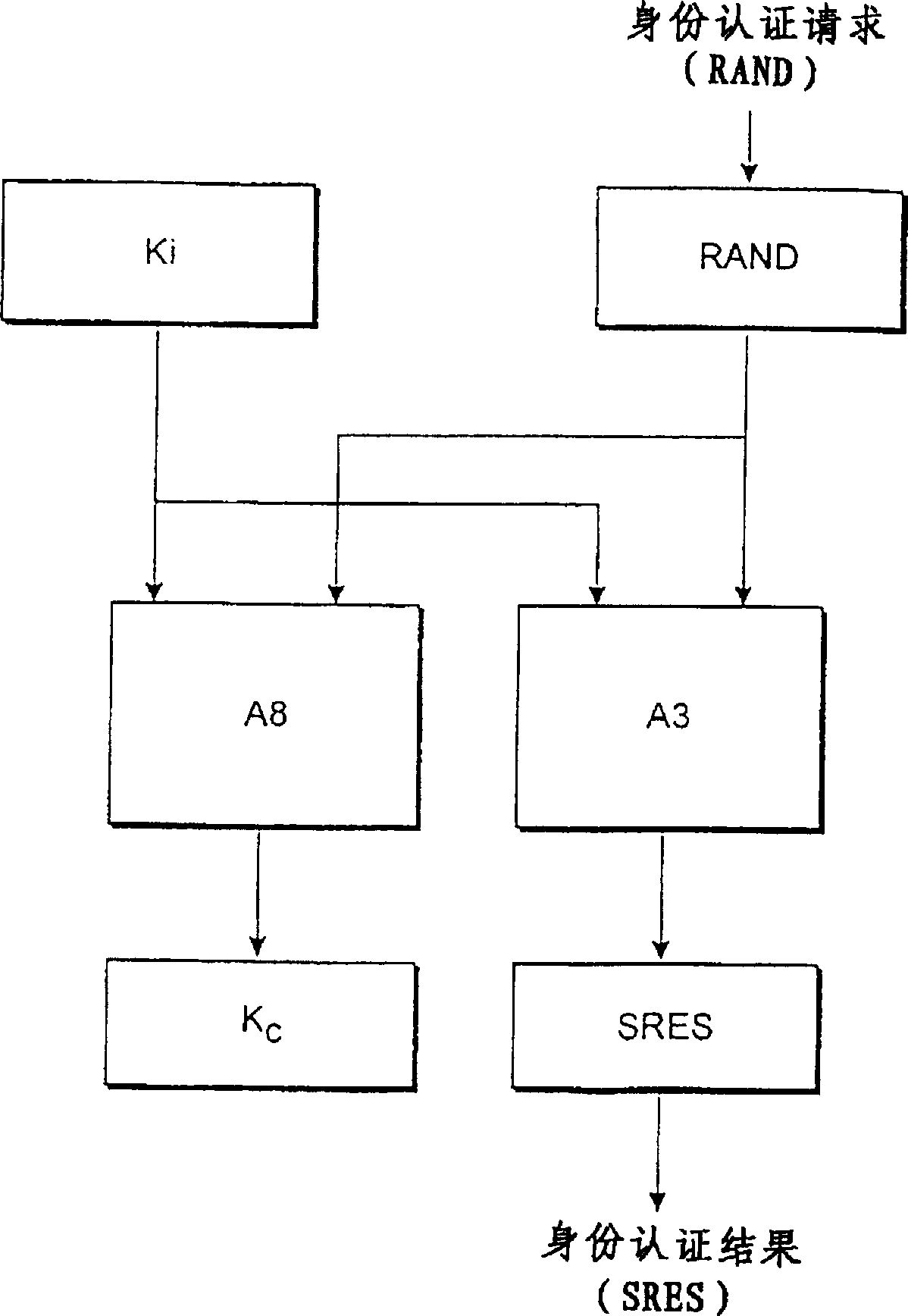
[0030] refer to Figures 6 to 8 , when the operation according to the present invention takes effect, a table 60 for holding terminal identities (IMEI, columns 62-64) which are permissible to said subscriber identity number (IMSI, column 61) is associated with the home location register HLR is generated together. Alternatively, an existing table, file or database can be extended to include the table 60 data. In the GSM system used as an example, the subscriber identification number is the IMSI and the terminal identification number is the IMEI. Figure 6 A situation is shown where two permitted terminals whose identification numbers in columns 62 and 63 have the values IMEI-1a and IMEI-1b respectively have been defined as permissible for the subscriber identification number IMSI-1. (symbol 64 represents that the number of allowed IMEI identification numbers is not limited to two). Only a permitted terminal whose identification number is IMEI-2a is defined as permitted for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com