Software plagiarism detection method based on reduced shortest path birthmarks
A technology of the shortest path and detection method, applied in software testing/debugging, error detection/correction, instruments, etc., can solve problems such as insufficient consideration of program semantics and behavior, overall plagiarism, difficulty in handling large programs, etc., to improve anti-deep confusion ability, wide application range, great practical value effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
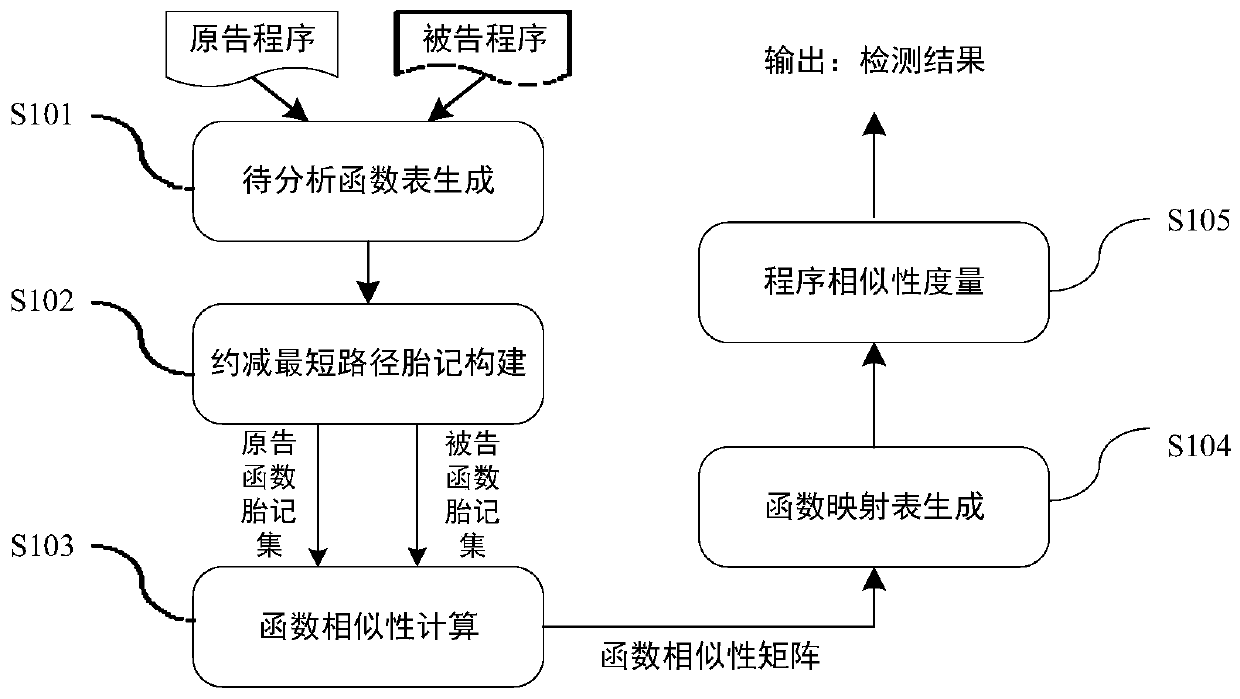
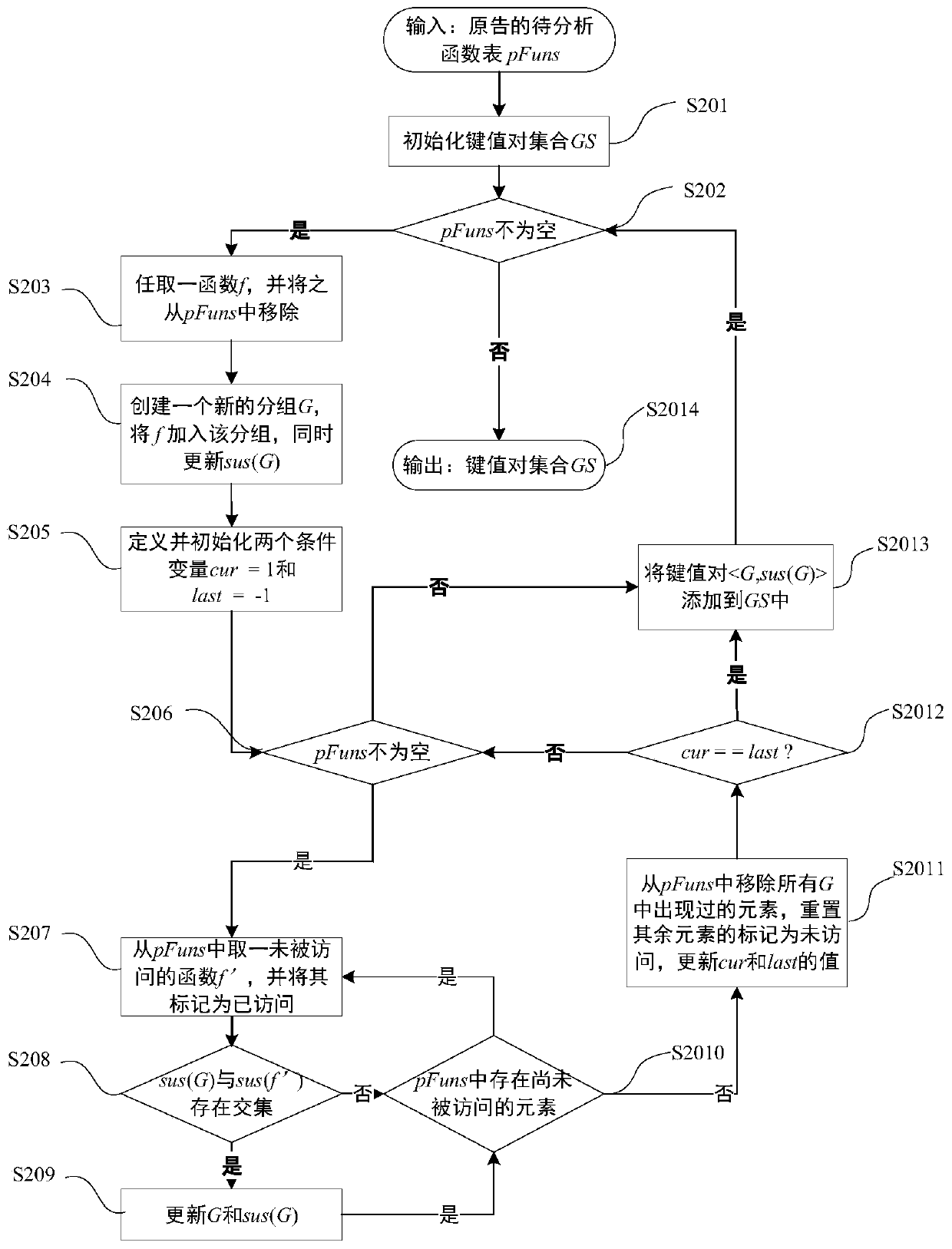
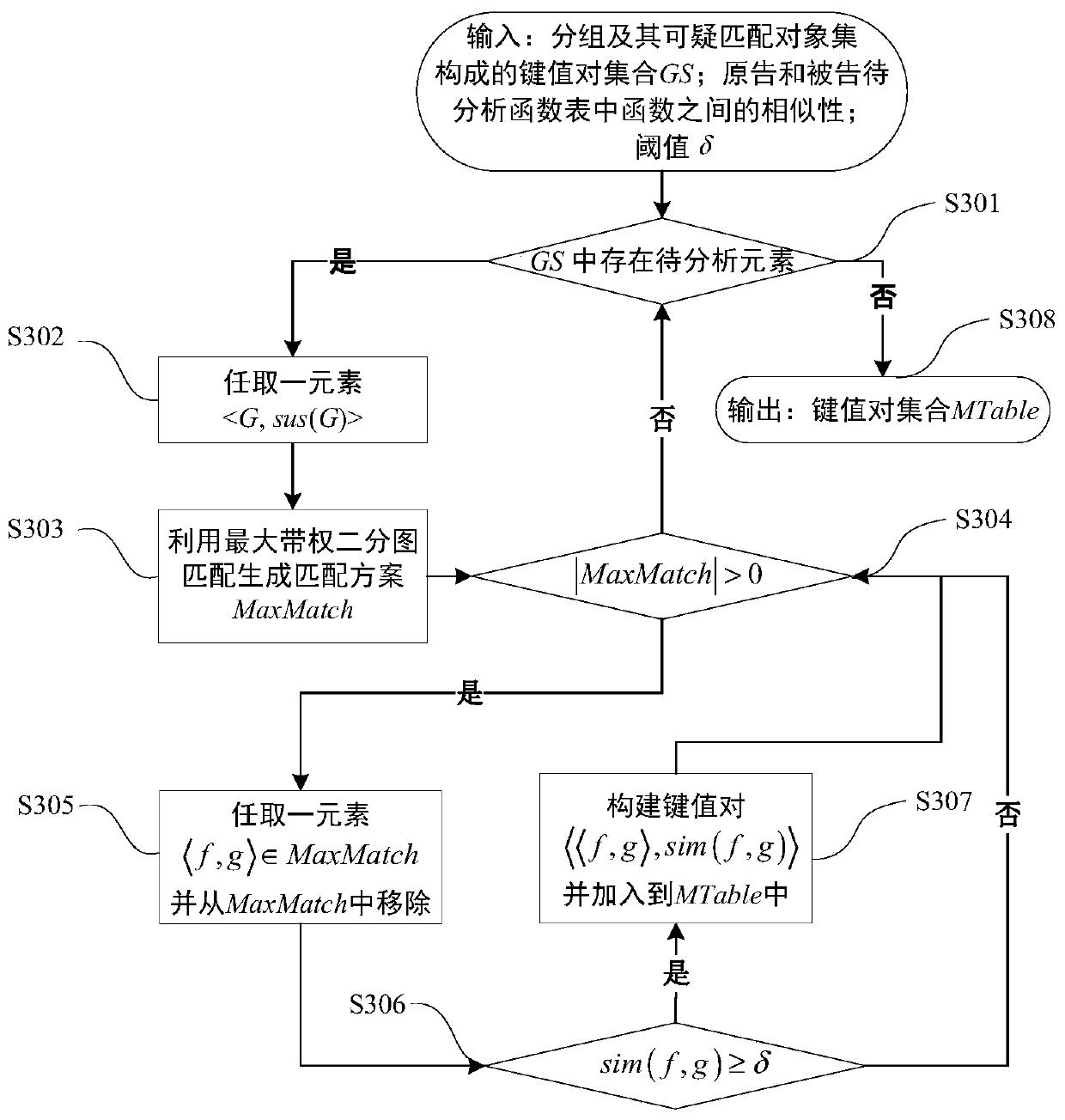
[0053] see figure 1 , which is the processing flow of the software plagiarism detection method based on reducing the shortest path birthmark, where the plaintiff program refers to the original program developed by the program owner, and the defendant program refers to the suspicious program suspected of plagiarizing part or all of the code of the original program. All are binary object programs and do not contain source code.
[0054] A software plagiarism detection method based on reducing the shortest path birthmark according to an embodiment of the present invention comprises the following steps:
[0055] Step S101: Use the static disassembly tool IDA Pro to analyze the plaintiff's program, extract all functions and their key elements from it, and the key elements include function address ID, assembly instruction set BODY, and con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com