Multi-core processor and fault injection method thereof
A technology of multi-core processor and fault injection, which is applied in the direction of electrical digital data processing, detecting faulty computer hardware, using fault dictionary to detect faulty hardware, etc. It can solve problems such as voltage influence and error, and achieve the effect of reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
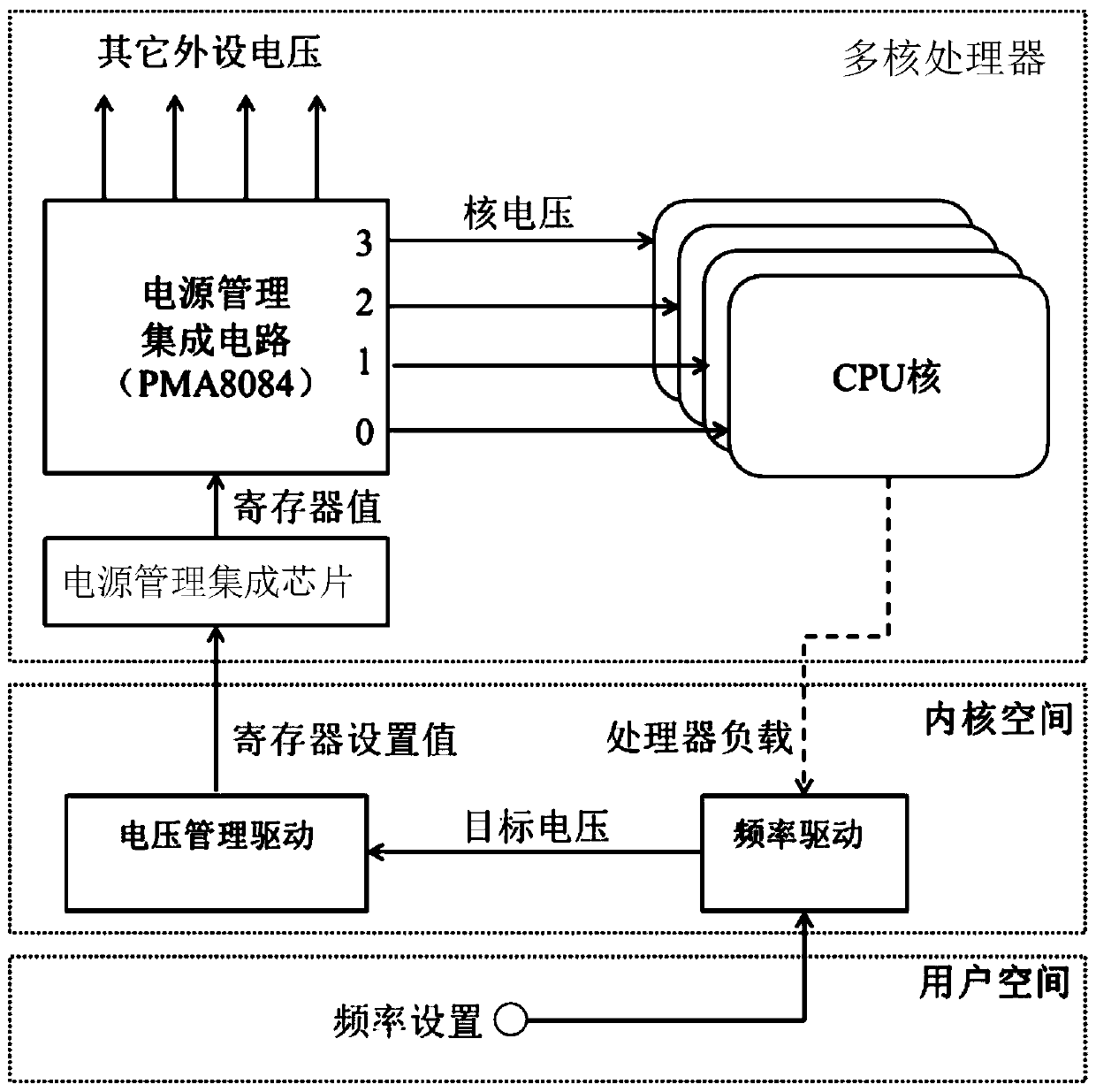
[0051] Based on the above modification to the voltage management driver, this application provides a frequency-voltage difference fault injection method based on a multi-core processor. When a hardware fault needs to be injected into a certain processor core, the processor core is designated as the attacked core , Bind the attacked program to the attacked core for execution, the processor core running the attacking program is used as the attacking core, and other processor cores are used as other unrelated cores. Therefore, the attacking core running the attacking program can be used The designated program injects hardware faults into the attacked core, and does not affect the normal operation of other unrelated cores and programs on them.
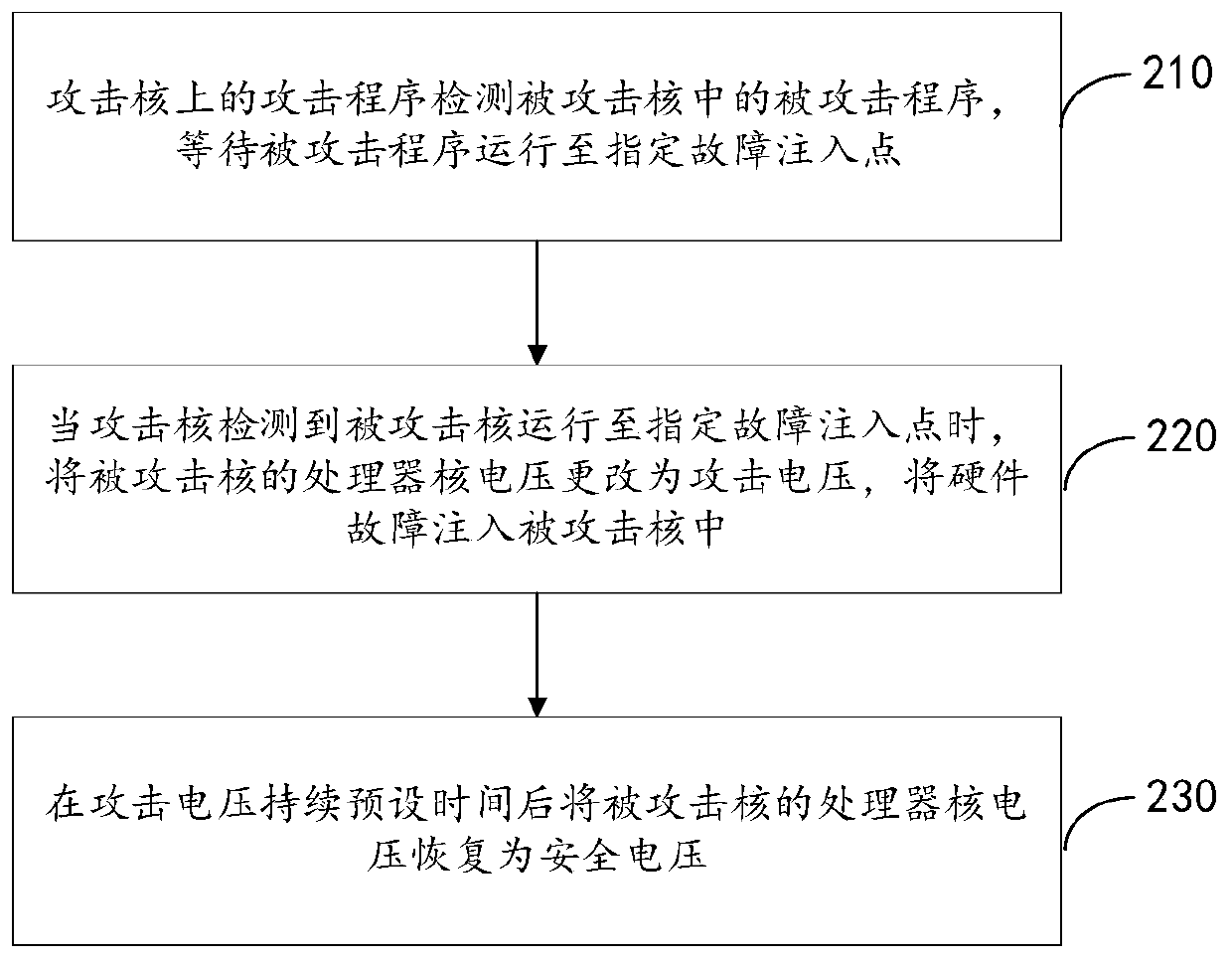
[0052] In this embodiment, the attack program running on the attacking core has a fault injection method for the attacked core as follows: figure 2 Shown, including:
[0053] Step 210: The attack program on the attacking core detects the attac...
Embodiment 2
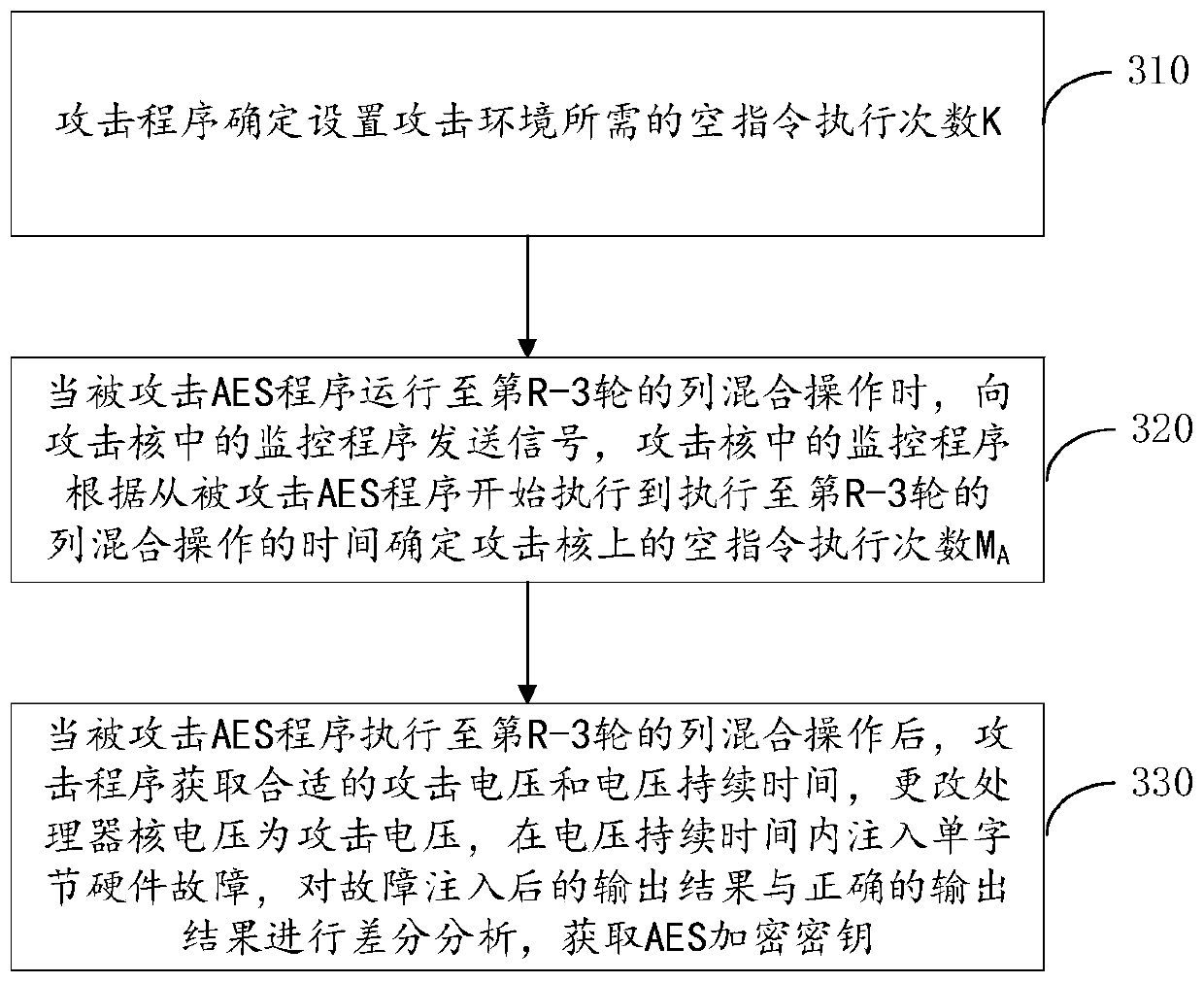
[0067] On the basis of the modification of the voltage management driver program of the embodiment to realize the hardware fault injection through the frequency-voltage difference, the second embodiment of the present application takes the AES encryption key obtained in the AES encryption program as an example to illustrate, the second embodiment includes: image 3 As shown to obtain the AES encryption key in the ordinary world and as Figure 4 Obtain the AES encryption key in TrustZone as shown;
[0068] Taking the designated fault injection point as inputting a single-byte fault in the R-2 round of the AES encryption program as an example, in order to make the input of the R-2 round of the AES encryption program a single-byte fault, the fault injection point is controlled In the R-3 round of column mixing operations.
[0069] image 3 In order to obtain the method flow chart of the AES encryption key in the ordinary world through frequency-voltage difference based fault injection,...
Embodiment 3
[0091] The third embodiment of this application provides a verification experiment in which a processor based on the ARM Krait architecture injects hardware faults into the AES encryption program to obtain the AES encryption key:
[0092] Image 6 Shown is the relationship diagram between the number of executions and the frequency of empty instructions required to wait for the attacked function to start executing. Among them, the frequency of the attack core is set to 0.42GHz, and the attack voltage is set to 0.6V. Image 6 It can be seen that the frequency affects the execution speed of the attacking core and the attacked core. When the attacking core frequency and the processor core voltage remain unchanged, the greater the frequency of the attacked core, the shorter the waiting time for the attacked function to start execution.
[0093] Figure 7 It shows the relationship between the number of executions and the frequency of the empty instructions required from the execution of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com