An equipment type identification and network intrusion detection method for the Internet of Things
A technology for network intrusion detection and Internet of Things equipment, applied in the Internet field, can solve the problems of low network traffic, low efficiency, scattered distribution of individual characteristics of equipment, etc., to improve the accuracy of identification and facilitate classification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Below in conjunction with accompanying drawing, the present invention will be further described.
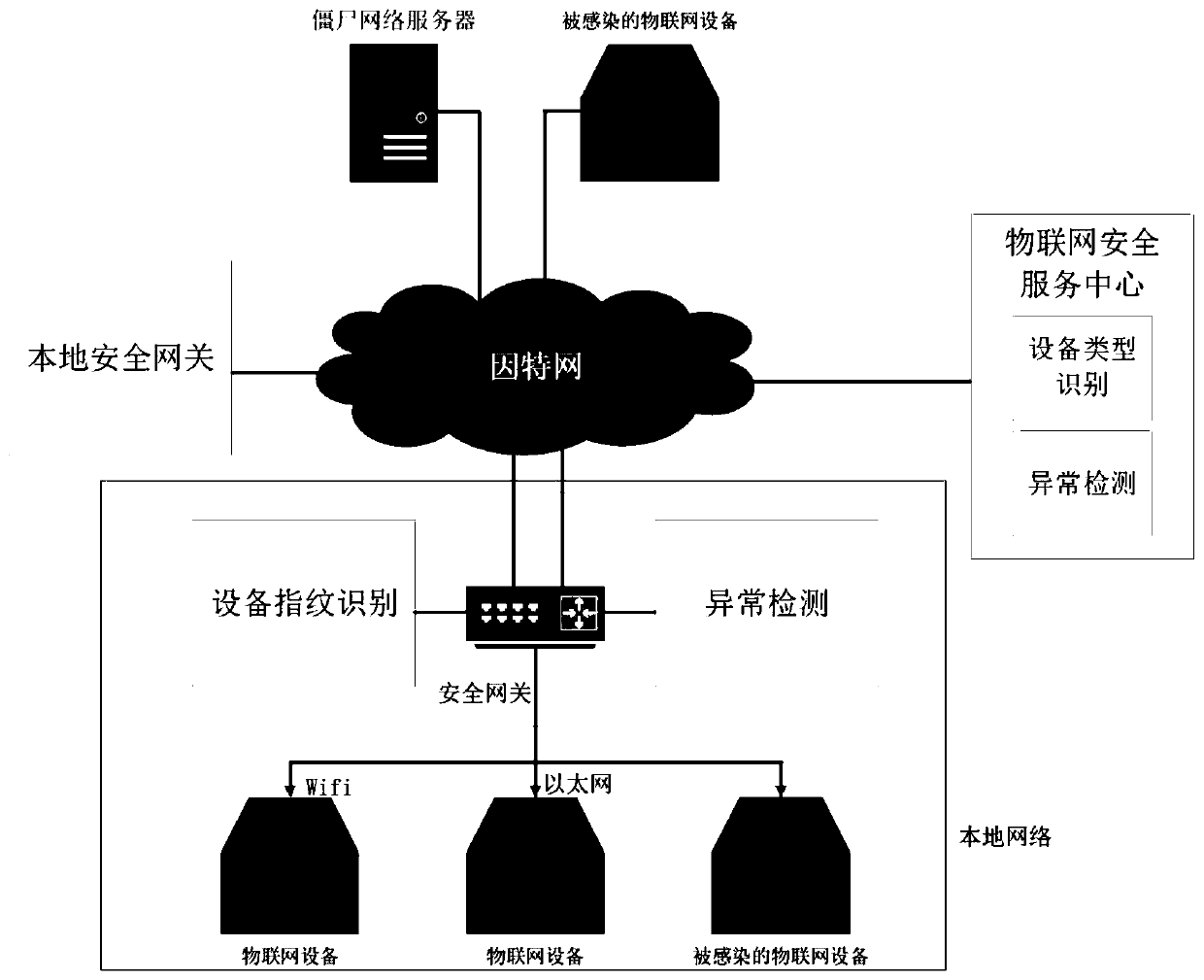
[0037] The technical solution adopted in this specific embodiment is: it includes a device type identification and matching system and an abnormality detection system; the device type identification and matching system is provided with a device fingerprint identification module; the abnormality detection system is provided with an abnormality detection module; see figure 1 As shown, in the local area network, all IoT devices, personal computers, and smart phone applications are directly or indirectly connected to the security gateway to access the Internet. The device fingerprint identification module in the security gateway monitors all communication behaviors of IoT devices and extracts communication behaviors. The mathematical features of the data are sent to the anomaly detection module and the normal communication behavior feature data set of the central Internet of Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com