Key management system
A key management system and key management technology, which is applied in the transmission system and key distribution, can solve the problems of cumbersome operation, low efficiency, and insufficient information encryption protection, so as to protect information security, prevent leakage, and facilitate timely transmission Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
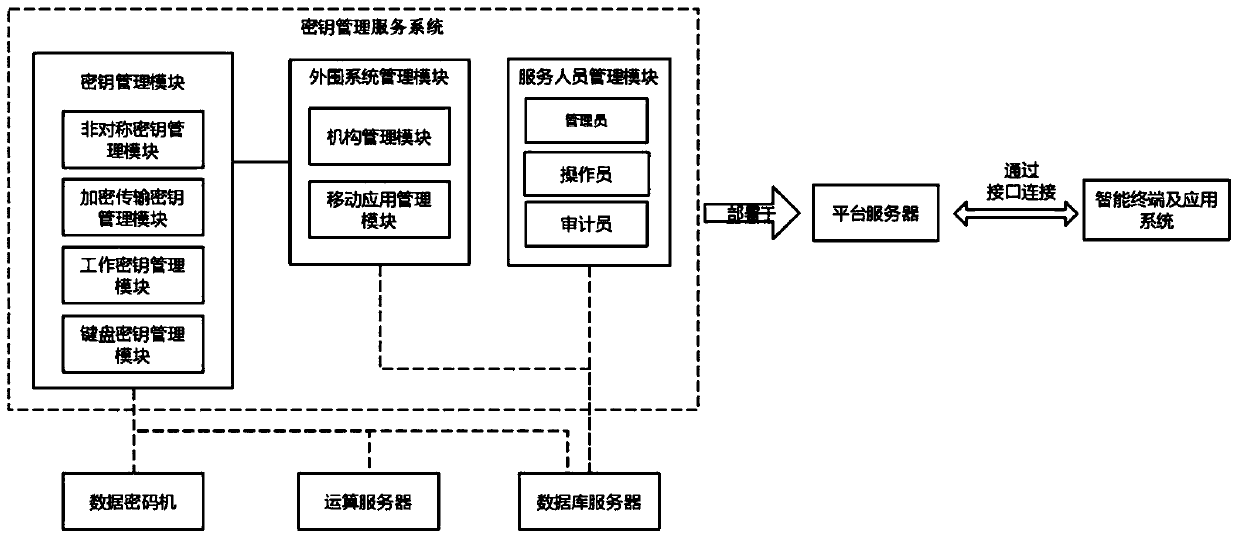
[0028] like figure 1 As shown, the key management system disclosed in the present invention includes a data cipher machine that provides the highest key, an operation server that provides the basis for decryption and encryption operations, a database server for storing keys and related data, and a platform server that provides system services , a key management service system deployed on a platform server for providing key services to smart terminals and application systems; the data cipher machine, computing server, and database server are respectively connected to the key management service system, and the platform The server is provided with an interface for connecting the key management service system with the smart terminal and the application system;
[0029] The key management service system includes a key management module for key generation, update, and application, for managing the smart terminal connected to the interface and a peripheral system management module fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com